Daily Drop (906): TSA: Key Transportation Sectors | RU: Sanctions | Texas Oilfield's | Trump and Tariffs | Zelenskyy & RU Accountability | MirrorFace | Musk’s & Fed | Ukrainian GPS Spoofing |
11-08-24
Friday, Nov 08 2024 // (IG): BB // ScraperDaddy // Cloud Email Harvester
New Tool Release:
Overview
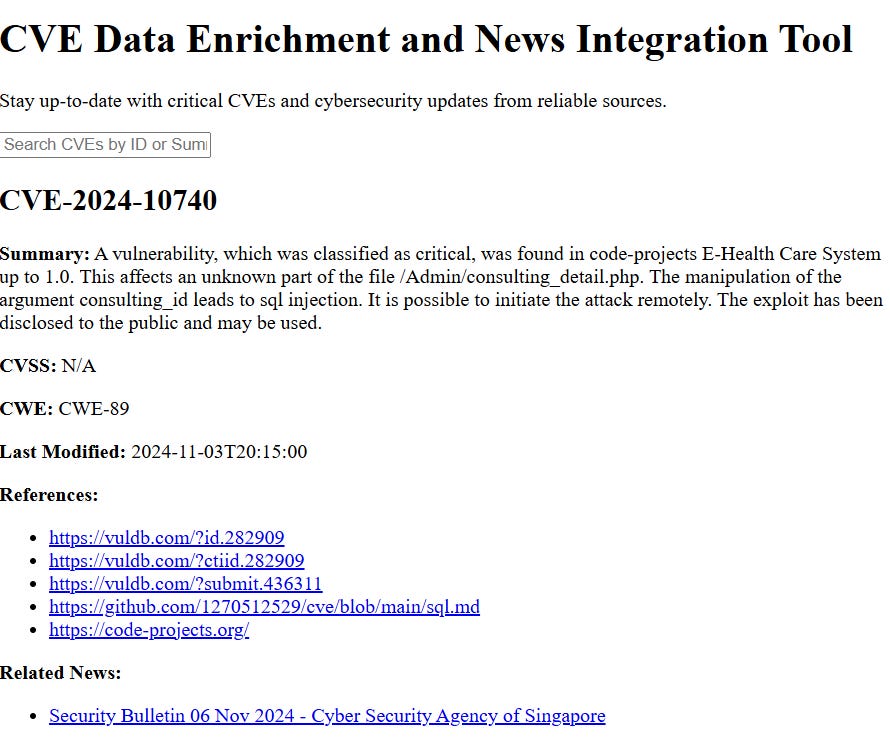
This project is a Python script designed to make handling CVE data easier and more insightful. It automatically extracts and enriches Common Vulnerabilities and Exposures (CVE) information by loading the data from a local JSON file. It then fetches additional details from an online CVE database and gathers related news articles from Google News RSS feeds. The goal is to provide enriched and up-to-date information about each vulnerability, which is then saved to an output file for further analysis or reporting.
How Western Sanctions Are Straining Russia’s Economy
Bottom Line Up Front (BLUF): Western sanctions on Russia are increasingly effective, impacting its economy despite outwardly stable GDP numbers. While Russia maintains export surpluses, resource limitations due to sanctions on imports, financial transactions, and access to foreign reserves are straining its industrial and military operations.
Analyst Comments: The effectiveness of these sanctions illustrates how strategic economic restrictions can reshape a war economy by limiting access to critical resources. Russia’s pivot to barter and high interest rates to sustain domestic military production underscores the challenges of sanctions evasion. With Russia increasingly relying on domestic resources, Western allies may seek to further tighten sanctions, especially on financial transactions, to maintain pressure.
FROM THE MEDIA: The Financial Times reported on November 7, 2024, that Western sanctions are pushing Russia’s economy against its resource limits. Key industrial figures, like Sergei Chemezov of Rostec, voiced concerns about unsustainable interest rates and material shortages due to sanctions restricting access to dual-use goods, financial networks, and $300 billion in foreign reserves. To cope, Russia is resorting to high-interest loans and even barter to circumvent traditional trade. Military spending, which now consumes around 40% of Russia’s budget, is straining domestic resources and increasing inflationary pressures. Western allies may look to impose further financial restrictions to counter Russian efforts to bypass the sanctions.
READ THE STORY: FT
Texas Oilfield Supplier Hit by Ransomware Attack, Disrupting Operations
Bottom Line Up Front (BLUF): Texas-based oilfield supplier Newpark Resources faced a ransomware attack on October 29, which disrupted access to its internal systems. Although the attack affected some business functions, the company has maintained essential field operations through established downtime procedures.
Analyst Comments: The oil and gas sector's ongoing vulnerability to ransomware is a trend that has made the industry a repeated target due to its critical nature and the financial impact of potential downtime. Newpark’s ability to continue operations underscores the value of established contingency protocols, yet the attack raises concerns about the cost and future cybersecurity investment needed to prevent such disruptions. With federal initiatives pushing for increased cybersecurity protections, this may add pressure on critical industries to strengthen defenses against ransomware threats.
FROM THE MEDIA: Newpark Resources disclosed that a ransomware attack had impacted its internal systems, limiting access to some operational and reporting applications. In a filing to the U.S. SEC, the company reported that the incident affected several business applications, though manufacturing and field operations continued as usual through contingency plans. Newpark, which provides tools for oilfield drilling and other energy sectors, has not identified a responsible hacking group and is still assessing the financial impact. This attack adds to a growing list of ransomware incidents targeting the oil and gas industry, pushing for stricter cybersecurity measures within the sector to safeguard critical infrastructure.
READ THE STORY: The Record
China’s Traditional Tariff Strategy May Fail Against Trump’s Proposed Tariff Hikes
Bottom Line Up Front (BLUF): With Donald Trump proposing a 60% tariff on Chinese imports if re-elected, China’s usual economic strategies—like diverting exports and currency depreciation—may not fully offset the impact. These new tariffs could strain Beijing’s economy, which is already contending with domestic challenges, including a struggling real estate market and weak consumer demand.
Analyst Comments: China’s response options are more constrained now than in 2018, when the first trade war prompted export redirection and currency devaluation. While diverting goods to Southeast Asia and other regions helped mitigate previous tariffs, the larger scale of Trump’s proposed tariffs and China’s weakened currency limit these options. Economic pressure from these tariffs could incentivize Beijing to strengthen domestic consumer demand through fiscal measures, but this may take time to impact growth significantly. U.S. import costs would likely rise, fueling inflation if tariff policies take effect.
FROM THE MEDIA: Trump’s plans to implement higher tariffs on Chinese imports could force Beijing into difficult decisions. China’s exports to the U.S. have fallen to 15% of its total exports, down from 19% in 2017, as goods were redirected to other markets like Southeast Asia. However, this diversion has limitations, and previous tariffs have already reduced China’s GDP by an estimated 0.65 percentage points. Goldman Sachs estimates the new 60% tariff could hit China’s GDP by two percentage points. Beijing’s options, including further devaluing the yuan, are limited due to capital flight risks and unfavorable bond yield differences with the U.S. China may thus focus on domestic growth to replace lost export demand, though this approach may face delays.
READ THE STORY: WSJ
Zelenskyy Rejects Calls for Peace Concessions to Russia
Bottom Line Up Front (BLUF): Ukrainian President Volodymyr Zelenskyy has firmly opposed calls from some Western leaders for Ukraine to make concessions to Russia in exchange for a ceasefire. He argues that any peace deal requiring concessions would ultimately compromise Ukraine’s sovereignty and weaken Europe’s security.
Analyst Comments: Zelenskyy's comments underscore the tension between Kyiv and confident European leaders advocating for a ceasefire. His resistance reflects Ukraine’s strategic concerns about halting hostilities before achieving concrete security assurances, especially in light of Donald Trump’s recent electoral win, which could lead to shifts in U.S. support. If Kyiv perceives a reduction in military support from the West, Ukraine may push European allies harder for robust backing, potentially complicating intra-EU relations.
FROM THE MEDIA: At a European summit hosted by Hungarian Prime Minister Viktor Orbán, Zelenskyy addressed leaders advocating for a ceasefire with Russia. He described peace concessions as “suicidal” for Ukraine and dangerous for European stability. Trump’s recent electoral win, which Orbán suggested could shift Western opinion toward peace talks, underscores growing West divisions over handling the conflict. Russian President Vladimir Putin, while open to negotiations, rejected external pressures, prompting Zelenskyy to urge Europe to increase military support to Ukraine rather than push for early peace talks.
READ THE STORY: FT
China-linked Hackers Target Japanese Organizations Through European Diplomatic Channels
Bottom Line Up Front (BLUF): The China-aligned hacking group MirrorFace has reportedly expanded its target range to include a diplomatic organization in the European Union, marking its first known attack outside Japan. Despite this broader targeting, MirrorFace remains focused on Japanese-themed operations, as indicated by spearphishing attempts related to Japanese events.
Analyst Comments: MirrorFace's pivot to European targets signifies a strategic shift, possibly aimed at exploiting diplomatic channels to gather intelligence linked to Japan's international relations. This expansion illustrates a growing sophistication and adaptability among China-aligned threat actors, who are targeting broader geopolitical interests while still maintaining a focus on Japan. Given the history of such attacks, this move could indicate a pattern where Japan’s adversaries are diversifying their approach to gather intelligence across multiple fronts.
FROM THE MEDIA: Slovak cybersecurity firm ESET reported that the MirrorFace hacking group, believed to be China-aligned, targeted a diplomatic organization within the European Union. This is the first documented case of the group shifting its focus beyond Japanese entities. The phishing email used a Japanese-themed lure document titled "The EXPO Exhibition in Japan in 2025" to appeal to the target’s interests. Historically, MirrorFace has focused on Japan-based organizations such as media, political entities, universities, and manufacturers. This latest incident adds to a series of high-profile attacks allegedly by Chinese hackers on Japanese networks, including a severe breach of Japan's defense networks in 2020, exposing significant vulnerabilities in Japan’s cybersecurity defenses.
READ THE STORY: The Record
Anthropic, Palantir, and AWS Bring Claude AI to U.S. Defense Intelligence
Bottom Line Up Front (BLUF): Anthropic has partnered with Palantir and Amazon Web Services (AWS) to integrate its AI model, Claude, into U.S. defense and intelligence applications. The partnership aims to enhance data processing, pattern analysis, and decision-making for classified environments, leveraging AWS and Palantir's secure infrastructure.
Analyst Comments: This collaboration highlights the expanding role of AI in national security and intelligence. Claude’s integration into defense platforms reflects a trend of using AI to streamline high-stakes decision-making and increase operational efficiency. Compared to policies by companies like Meta, the flexibility of Anthropic’s acceptable use policy for government use suggests openness to high-risk applications within secure environments. As these systems become integral to sensitive missions, understanding and addressing AI's ethical and operational implications in defense will be increasingly crucial.
FROM THE MEDIA: Palantir, Anthropic, and AWS announced a collaboration to deploy Claude AI models within U.S. defense and intelligence agencies. This integration allows Claude to operate in Impact Level 6 (IL6) environments—certified for classified data handling—using Palantir’s AI Platform and AWS's secure infrastructure. Unlike Meta's AI model Llama, which requires specific acceptable use policy exceptions for government applications, Claude operates under Anthropic’s established allowances for defense and intelligence purposes. The AI will speed up data processing, document reviews, and pattern recognition, supporting time-sensitive intelligence operations. Anthropic confirmed that Claude’s deployment would adhere to legal constraints while supporting foreign intelligence and potential military activity monitoring, positioning AI as a tool for proactive defense.
READ THE STORY: The Register
Cost-Cutting Lessons from Musk’s Playbook for the Federal Government
Bottom Line Up Front (BLUF): Elon Musk, known for his aggressive cost-cutting measures at companies like Tesla, SpaceX, and Twitter, may soon bring his approach to government spending. Appointed by President-elect Trump to lead a new efficiency-focused department, Musk has ambitious goals, including slashing $2 trillion from the federal budget.
Analyst Comments: Musk’s record of rapid cost-cutting and workforce reductions in the tech industry signals a potential shift in government spending philosophy. While his tactics have previously led to leaner, more efficient operations, applying them to the public sector could face significant challenges. Much of the federal budget is tied to fixed expenses like Social Security, Medicare, and defense, which may limit the scope of Musk’s efforts. Additionally, his approach could encounter resistance from long-standing government structures, unions, and regulatory bodies.
FROM THE MEDIA: Musk is expected to lead the newly established Department of Government Efficiency (DOGE) under the Trump administration. Known for his cost-cutting expertise, Musk plans to tackle federal spending with the same intensity he brought to Twitter-turned-X, where he famously cut 80% of the workforce while maintaining operations. Musk’s initial goal is to identify $2 trillion in budget cuts, but he faces challenges, as more than half of government spending is allocated to entitlements and defense. However, with a Republican-majority Congress, Musk may find an unprecedented opportunity to push for reductions in discretionary spending and regulatory streamlining. His approach could involve leveraging administrative authority to reduce agency functions and limit spending outside of Congressional cuts, aiming to create a leaner federal government.
READ THE STORY: WSJ
Ukrainian Military GPS Spoofing Creates Civilian Disruptions Amid Drone Attacks
Bottom Line Up Front (BLUF): Ukrainian electronic warfare (EW) efforts to counter Russian drones inadvertently caused GPS disruptions across civilian devices in Kyiv. Phones incorrectly displayed locations and times based on Russian cities. Ukrainian officials advised citizens to disable automatic phone time adjustments to prevent further confusion.
Analyst Comments: The unintentional effects of EW technology illustrate the complexities of defending against drone warfare in civilian areas. This incident highlights Ukraine’s significant challenges in balancing military tactics with civilian impact, as GPS spoofing can disrupt critical daily activities. As both Ukraine and Russia expand their use of electronic warfare, civilians in conflict zones may increasingly experience unintended technological interference.
FROM THE MEDIA: Multiple Ukrainians in Kyiv reported unexpected changes in their phone’s time and location data, which shifted to Russian zones like Moscow and Belgorod. The Ukrainian General Staff confirmed that EW systems used to counter Russian drone strikes were responsible for GPS spoofing, which can mislead drones or cause them to crash. This technology, however, affected civilian phones, causing many to be late or miss appointments. Users took to social media to share their frustrations, prompting officials to recommend disabling automatic time changes. The incident is part of broader electronic warfare tactics by both Ukraine and Russia, with the Ukrainian military responding to a high volume of Russian drone attacks over recent months.
READ THE STORY: The Record
TSA Proposes Cybersecurity Regulations for Key Transportation Sectors
Bottom Line Up Front (BLUF): The Transportation Security Administration (TSA) has proposed cybersecurity regulations to enhance the resilience of critical transportation infrastructure. The rules target pipelines, railroads, airlines, and related sectors, consolidating emergency measures enacted after the Colonial Pipeline ransomware incident in 2021.
Analyst Comments: These new mandates mark a significant shift toward standardized, enforceable cybersecurity protocols across transportation sectors. The TSA aligns its rules with current cybersecurity best practices by broadening incident reporting requirements to the Cybersecurity and Infrastructure Security Agency (CISA) and requiring adherence to secure-by-design principles. As administration changes loom, this proposal may serve as a long-standing framework to secure critical transportation infrastructure in the U.S.
FROM THE MEDIA: The TSA introduced a proposal to formalize and unify cybersecurity standards for pipelines, rail, and air transport. This Notice of Proposed Rulemaking (NOPR) builds on emergency directives issued following the Colonial Pipeline ransomware attack, which exposed vulnerabilities in critical infrastructure. The TSA’s proposed regulations mandate that nearly 300 entities develop cyber risk management programs, undergo routine cybersecurity audits, and report significant incidents to CISA. Industry reaction has been mixed; some trade groups initially resisted similar directives but have since recognized the need for structured cybersecurity defenses. The proposed rules are expected to impact around 73 freight railroads, 34 public transportation agencies, 115 pipeline facilities, and numerous bus operations. Public comments are open until February 5, 2025.
READ THE STORY: CyberScoop
TSMC prioritizing high-NA EUV scanners for R&D
Bottom Line Up Front (BLUF): A leading semiconductor manufacturer plans to install high numerical aperture (NA) extreme ultraviolet (EUV) scanners at its research facility by the end of this year. These highly advanced tools are critical for developing future semiconductor technology but will require several years of testing and optimization before being ready for mass production, likely after 2030.
Analyst Comments: The investment in high-NA EUV scanners demonstrates a forward-thinking approach to semiconductor innovation to meet future demands for higher-performance and more densely packed chips. The lengthy testing phase highlights the sophistication and importance of these machines in advancing chip technology, as well as the global strategic value of EUV tools, which are subject to export restrictions, particularly to China. This focus on R&D indicates a commitment to technological leadership and the ability to deliver cutting-edge solutions for years.
FROM THE MEDIA: A significant semiconductor company will focus its initial high-NA EUV scanners on R&D efforts. These scanners, each costing around $350 million, can use extreme ultraviolet light to etch wonderful, dense patterns on semiconductor wafers, paving the way for future generations of chips with higher transistor density and efficiency. The machines, set to arrive by year-end at the company’s research facility in Taiwan, will undergo extensive testing and refinement before they are ready for commercial-scale production, anticipated around 2030. By then, these high-NA EUV systems are expected to support the debut of advanced chip nodes, enabling the next era of computing power.
READ THE STORY: The Register
CVE-2024-38213: Exploiting Vulnerabilities for Full System Compromise in Targeted Attacks
Bottom Line Up Front (BLUF): Veriti Research has uncovered a sophisticated attack exploiting CVE-2024-38213, a vulnerability enabling attackers to bypass security protocols by disguising malware as part of the Gas Infrastructure Europe (GIE) Annual Conference in Munich. The attack utilizes the malware LummaStealer to siphon sensitive data from targeted systems, presenting a critical risk to the organizations involved.
Analyst Comments: The exploitation of CVE-2024-38213 reflects a growing trend in which attackers leverage known vulnerabilities to penetrate high-profile, industry-specific events. Focusing on GIE attendees, this campaign shows how cybercriminals craft highly targeted campaigns that bypass traditional security warnings. The vulnerability’s ability to evade Microsoft’s Mark-of-the-Web defenses makes it particularly concerning for industries relying on Windows-based systems, requiring robust, proactive defenses like SIGMA detection rules and blocked IoCs.
FROM THE MEDIA: Veriti reported a phishing campaign exploiting CVE-2024-38213, named “Copy2Pwn,” to launch malware attacks on attendees of the GIE conference. Attackers sent emails with malicious LNK files that, when opened, connected to domains mimicking the GIE’s official conference URL. The attack uses LummaStealer malware, which establishes a connection to command-and-control servers, enabling attackers to exfiltrate data from compromised devices. This vulnerability circumvents Windows’ Mark-of-the-Web protections, allowing attackers to deploy payloads without flagging them as high-risk, complicating detection efforts. The attack’s origins are traced back to a malicious domain registered in October 2024, indicating premeditated targeting of conference participants.
READ THE STORY: Security Boulevard
Winos4.0 Malware Abuses Gaming Apps to Infect Windows Machines
Bottom Line Up Front (BLUF): Attackers use gaming-related applications to infect Windows devices with a malware framework called Winos4.0, giving them full control over compromised systems. According to Fortinet, the malware, a rebuilt version of Gh0strat, is suspected to be targeting educational organizations.
Analyst Comments: Winos4.0 highlights the evolving risk of using seemingly benign applications as a vector for malware, particularly in environments where users may download unverified apps, such as educational institutions. By employing gaming utilities as a lure, attackers increase the chances of targeting younger, less security-conscious users. The sophisticated multi-stage infection chain and persistent command-and-control (C2) communications indicate a well-organized threat actor, possibly state-linked. Organizations should exercise caution and avoid unofficial downloads, especially gaming-related software.
FROM THE MEDIA: Fortinet reported that criminals use game-enhancement apps to deliver Winos4.0 malware to Windows machines. The infection chain begins with a seemingly innocuous gaming-related app, which downloads a fake BMP file from "ad59t82g[.]com" that initiates the malware. Winos4.0 proceeds through multiple stages, including injecting shellcode, establishing persistence, and communicating with a C2 server. The final stage collects extensive system data, including IP address, CPU, operating system, and crypto wallet details. It also takes screenshots, steals documents, and installs a backdoor to allow ongoing access. Winos4.0 has reportedly been used in campaigns linked to Silver Fox, a group suspected of ties to the Chinese government.
READ THE STORY: The Register
Items of interest
Trump Transition Eyes Key Cyber Policy Roles for New Administration
Bottom Line Up Front (BLUF): As Donald Trump prepares to take office, several top cybersecurity positions are under consideration, with notable names from the Trump administration’s first term emerging as potential candidates. The picks will shape U.S. cyber policy direction in agencies like CISA, the Pentagon, and the Department of Energy.
Analyst Comments: Trump’s anticipated picks for key cybersecurity roles highlight a preference for officials with prior government experience and alignment with Trump-era priorities. This strategy may streamline Senate confirmation processes but could signal a shift toward previous approaches to cyber policy, focusing on robust national defense measures. Including figures from past cybersecurity roles suggests continuity in Trump’s cyber policy framework, with a potential emphasis on resilience against foreign cyber threats.
FROM THE MEDIA: According to sources cited by POLITICO on November 7, 2024, individuals such as Sean Plankey, Karen Evans, and Joshua Steinman are top contenders for leading agencies like CISA, the NSC cyber office, and the DOE’s cybersecurity division. Other names being discussed include Katie Arrington, Rob Strayer, and Matt Hayden, who bring experience from the Department of Defense, the State Department, and DHS, respectively. Each has expressed a commitment to national cyber defense, with some indicating a willingness to rejoin public service if asked. Arrington, for instance, has voiced enthusiasm for a potential role, citing the importance of cyber resilience amidst ongoing non-kinetic threats to U.S. infrastructure.
READ THE STORY: POLITICO
The Evolution of U.S. Cyber Strategy (Video)
FROM THE MEDIA: In the early 2000s, the U.S. government viewed cyberspace with optimism with the belief that access to and information from the internet would help spread democracy worldwide. However, cyberattacks from state and non-state actors, such as North Korea's attack on Sony and Iran's campaign against U.S. banks, highlights the growing threat posed by cyberwarfare. The United States must now strategically adapt its approach to cybersecurity and recognize the ever-changing and complex digital landscape to successfully face the array of cyber threats from rival nations and bad actors.
Former cybersecurity official on misinformation in the 2024 election (Video)
FROM THE MEDIA: Chris Krebs, former director of the Cybersecurity and Infrastructure Security Agency during the 2020 election, joins TODAY to share what he’ll be watching for on Election Day, the foreign interference in the race for the White House, and his message to voters as they head to the polls.
The selected stories cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not endorse any third-party claims made in its original material or related links on its sites; the opinions expressed by third parties are theirs alone. For further questions, please contact InfoDom Securities at dominanceinformation@gmail.com.