Daily Drop (905): Synergia II | Schneider Electric | UK: FTDI | Cisco URWB AP's | Raptor Lake Processors | UAE: Africa | MirrorFace | AstraZeneca | AT&T Settles With FCC |
11-07-24
Thursday, Nov 07 2024 // (IG): BB // ScraperDaddy // Cloud Email Harvester
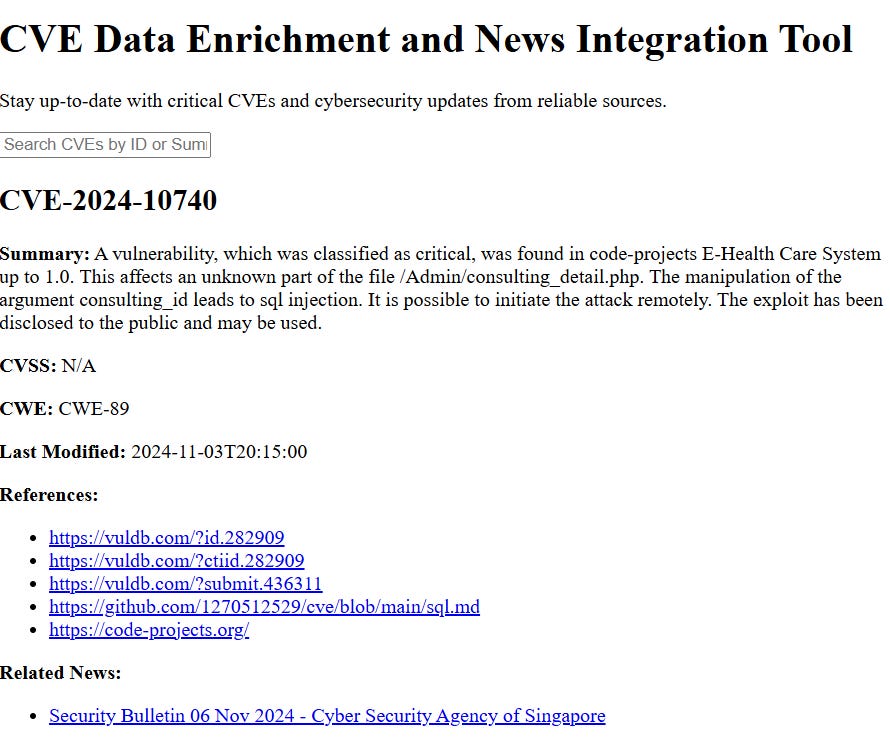
New Tool Release:
Overview
This project is a Python script designed to make handling CVE data easier and more insightful. It automatically extracts and enriches Common Vulnerabilities and Exposures (CVE) information by loading the data from a local JSON file. It then fetches additional details from an online CVE database and gathers related news articles from Google News RSS feeds. The goal is to provide enriched and up-to-date information about each vulnerability, which is then saved to an output file for further analysis or reporting.
Interpol's Operation Synergia II Targets Global Cybercriminals, Dismantling Infrastructure and Making 41 Arrests
Bottom Line Up Front (BLUF): Interpol's recent Operation Synergia II has led to 41 arrests, shutdowns of over 22,000 IP addresses, and seizures of 59 servers and 43 other devices in a large-scale cybercrime crackdown. Conducted across 95 countries, this operation targeted various online criminal activities, including phishing, ransomware, and banking malware operations, with assistance from significant cybersecurity firms.
Analyst Comments: Operation Synergia II highlights the power of international coordination in tackling cybercrime's cross-border nature. Interpol's efforts hindered cybercriminals' capabilities and disrupted ongoing attacks by seizing critical infrastructure, like servers used for malicious operations in multiple countries. This crackdown demonstrates the potential for public-private partnerships to bolster global cybersecurity and underscores cyber criminals' persistent adaptability. Continuous international collaboration will be essential to maintain these preventive measures and to monitor emerging cyber threats.
FROM THE MEDIA: As part of its global cybercrime campaign, Interpol, in collaboration with cybersecurity firms Group-IB, Trend Micro, Kaspersky, and Team Cymru, targeted cybercriminal infrastructure and operators in 95 countries. In Hong Kong, law enforcement identified 1,037 servers engaged in cybercrime, which were subsequently shut down. Police in Macao took down 291 more servers, while a raid in Mongolia led to the arrest of 93 individuals suspected of cybercrime involvement. Additionally, law enforcement in Estonia seized 80GB of data linked to phishing and banking malware. Neal Jetton, head of Interpol's Cybercrime Directorate, commended the operation, stating it successfully prevented cyberattacks and safeguarded thousands of potential victims.
READ THE STORY: The Register
Schneider Electric Investigates Cyberattack Following Alleged Data Theft by Hacker Group
Bottom Line Up Front (BLUF): Schneider Electric has investigated a cyberattack after hackers claimed to have accessed over 40GB of critical data. The company confirmed the affected system was isolated, preventing the spread of operational technology (OT). The hackers have demanded a $125,000 ransom, though Schneider has not commented on whether they will pay.
Analyst Comments: This breach highlights the heightened vulnerability of the manufacturing sector to cyberattacks, especially targeting project data or internal platforms that can yield detailed insights into corporate operations. Although Schneider Electric reported no impact on operational technology, this incident could pose secondary risks if the stolen data reveals information about the company’s project plans, customer specifications, or employee access levels. As manufacturing companies increasingly face targeted ransomware, safeguarding IT and OT environments has become imperative for business continuity. The data could be an asset for adversaries targeting Schneider or its clients.
FROM THE MEDIA: Schneider Electric disclosed that it is investigating a cyber incident after the hacker group “Hellcat” claimed to have stolen 40GB of data. According to a spokesperson, the breach occurred on an internal project-tracking platform located within a contained system, which prevented the spread of malware to other critical areas. The attackers, using an X account under the handle “greepy,” demanded $125,000 and released some data on a site associated with Hellcat. This is Schneider’s second known cyber incident in 2024; earlier, its sustainability division was compromised by ransomware. Notably, ransomware attacks targeting industrial and manufacturing sectors surged in 2024, with 303 attacks in the second quarter alone.
READ THE STORY: WSJ
UK Orders Chinese Owners to Divest from Scottish Semiconductor Firm FTDI
Bottom Line Up Front (BLUF): The UK government has mandated that Chinese investors divest their 80.2% stake in Glasgow-based semiconductor company FTDI, citing national security concerns under the National Security and Investment Act. This decision aims to prevent sensitive semiconductor technology and intellectual property from potentially being exploited in ways that could compromise UK national security.
Analyst Comments: This move reflects the UK's increasingly assertive stance on foreign ownership of critical technology assets. By invoking the National Security and Investment Act, the UK is prioritizing control over semiconductor technology—a sector vital to national security and economic resilience. As global semiconductor supply chains remain a focal point of geopolitical tension, more restrictive actions like this are likely to continue in Western nations, especially given the UK's recent measures to limit Chinese access to strategic technologies. Such actions might prompt Chinese firms to seek alternate markets for tech acquisitions, though Western nations may follow suit in tightening foreign investment scrutiny.
FROM THE MEDIA: UK ordered Chinese investors to divest their holdings in Future Technology Devices International (FTDI), a semiconductor company based in Scotland, due to national security concerns. The ruling by the Chancellor of the Duchy of Lancaster follows an assessment under the National Security and Investment Act, which allows the UK to block or unwind acquisitions that could threaten national interests. The mandate requires the holding company with Chinese ties to sell its 80.2% stake within a specified timeframe. FTDI’s products are used in sensitive infrastructure, and officials expressed concerns that control by Chinese interests could pose risks to critical UK infrastructure. This action aligns with prior decisions, such as the forced sale of Newport Wafer Fab in 2022 after it was acquired by a Chinese-owned firm, Nexperia, amid rising scrutiny of China’s involvement in Western technology industries.
READ THE STORY: The Record
Critical Vulnerability in Cisco URWB Access Points Enables Root Command Execution
Bottom Line Up Front (BLUF): Cisco has disclosed a critical vulnerability (CVE-2024-20418) in specific Ultra-Reliable Wireless Backhaul (URWB) access points. The vulnerability allows remote attackers to execute commands with root privileges by sending crafted HTTP requests to the device’s web interface. The flaw affects certain Catalyst models, and no workaround is currently available.
Analyst Comments: Cisco’s URWB access points reflects the increasing cybersecurity risks faced by industrial IoT and wireless automation systems. Unauthorized root access on these devices could allow attackers to manipulate or disable network traffic, compromising connected devices in industrial environments. With no workaround, organizations using these models must prioritize firmware updates and evaluate network access controls to mitigate unauthorized access. The potential implications of this flaw may extend beyond isolated system control, impacting broader operational technology (OT) infrastructure if exploited.
FROM THE MEDIA: Cisco announced a high-risk vulnerability (CVE-2024-20418) affecting the web-based management interface of its Unified Industrial Wireless Software for URWB access points, specifically the Catalyst IW9165D, IW9165E, and IW9167E models. The vulnerability is caused by improper input validation in the web interface, allowing attackers to inject commands as root. Cisco advises customers to verify vulnerability by checking the device’s “URWB mode” status via the CLI command show mpls-config. Cisco's PSIRT noted that no active exploitation of the vulnerability has been observed yet. However, they recommend immediate patching as no workarounds are currently available.
READ THE STORY: SA
Intel Faces Class-Action Lawsuit Over Voltage Issues in Raptor Lake Processors
Bottom Line Up Front (BLUF): Intel is being sued in federal court over alleged voltage instability in its 13th and 14th-generation Raptor Lake processors, which claimed to cause instability and performance issues in affected devices. Despite acknowledging the problem and releasing multiple patches, Intel now faces accusations of fraud and breach of warranty for not disclosing the defect sooner.
Analyst Comments: This lawsuit against Intel highlights the risks technology companies face when product flaws affect user experience. With Intel admitting to voltage instability only in mid-2024, despite earlier signs of the issue, the case underscores the need for transparent communication to maintain customer trust. If the lawsuit gains traction, it could prompt stricter regulatory scrutiny and consumer protection measures for high-performance tech products. Such a high-profile suit may also proactively influence other manufacturers to address hardware and software vulnerabilities.
FROM THE MEDIA: Plaintiff Mark Vanvalkenburgh filed a class-action lawsuit in California against Intel, alleging that Raptor Lake processors have defects leading to voltage instability and system crashes. According to the complaint, Intel knew of these issues by early 2023 but continued marketing the chips as high-performance products. The plaintiff claims his Intel Core i7-13700K processor caused frequent screen blackouts and random restarts, even after Intel’s patch attempts. Intel acknowledged in July 2024 that "elevated operating voltage" in the affected processors led to "Vmin Shift Instability." Since then, Intel has issued three patches to mitigate the issue, adjusted the processors' voltage requests, and extended the warranty on affected units.
READ THE STORY: The Register
UAE Outpaces China and U.S. in African Investments, Dominating Key Sectors
Bottom Line Up Front (BLUF): The United Arab Emirates (UAE) has become a dominant foreign investor in Africa, committing nearly $97 billion over recent years, far surpassing China and the U.S. The UAE strategically invests in mines, ports, agriculture, and renewable energy, positioning itself as a key player in Africa’s resource and infrastructure sectors. This shift underscores the UAE's drive to diversify its economy and expand its African influence.
Analyst Comments: The UAE’s assertive investments reflect a new wave of international competition for influence in Africa, signaling a shift in the region’s geopolitical landscape. While China traditionally led in Africa’s infrastructure projects, the UAE's focus on energy, mining, and agriculture presents a fresh approach to securing resources vital for future energy transitions. This strategic pivot enables the UAE to secure supply chains and access valuable minerals for its clean energy initiatives, potentially reshaping regional alliances and creating economic dependencies on the Gulf state. U.S. and Chinese interests in Africa may need to adapt, as UAE's targeted investments redefine the competitive dynamics.
FROM THE MEDIA: The UAE has rapidly expanded its investments in Africa, with new stakes in sectors such as mining, renewable energy, and agriculture. Last year, UAE-backed International Resources Holding (IRH) outbid China’s Zijin Mining for a 51% stake in Zambia's Mopani Copper Mines. IRH, linked to UAE’s national security leadership, is increasing copper production and exploring other African mining projects, including Angola’s Kassala Kitungo and Burundi’s Musongati nickel mine. In Uganda, the UAE has gained influence with high-profile donations and investments, including a $4.5 billion oil refinery fund. However, UAE's presence is not without controversy, as reports have surfaced linking the UAE to arms shipments in regional conflicts, leading to pushback from local communities and criticism over alleged interference in African affairs.
READ THE STORY: WSJ
Ukrainian University Bans Telegram Amid Growing Cybersecurity Concerns
Bottom Line Up Front (BLUF): Taras Shevchenko National University of Kyiv has banned Telegram for official communications, citing national security risks associated with the Russian-founded messaging app. The decision aligns with broader restrictions on Telegram for the Ukrainian government and critical infrastructure staff due to concerns over potential data access by Russian intelligence.
Analyst Comments: This restriction underscores Ukraine's proactive approach to limiting digital vulnerabilities in the context of ongoing cyber threats from Russia. By banning Telegram, a widely used app with significant data-sharing risks, Ukrainian institutions safeguard against potential espionage and data interception. However, denying such a popular communication tool may disrupt established information-sharing practices among students and faculty. As Ukraine strengthens cybersecurity efforts, similar measures may spread across other universities and public institutions, though the challenge of balancing security with practicality remains.
FROM THE MEDIA: Ukraine’s largest university, Taras Shevchenko National University of Kyiv (KNU), prohibited faculty from using Telegram for official purposes. The move follows recent government mandates restricting Telegram use for state officials and critical infrastructure staff, a response to warnings from Ukrainian intelligence that Russian entities could access personal data and conversations on the app. A decree from KNU’s chancellor mandates that all university-affiliated Telegram accounts, bots, and channels be deleted. This announcement prompted students to vote on alternative platforms, with Instagram and WhatsApp emerging as preferred replacements. Although Telegram is still allowed for personal use, many students expressed concerns about connectivity on university Wi-Fi and the app's importance for real-time alerts on security threats. Other Ukrainian universities, including National Aviation University, have publicly supported the restriction, and further national-level actions against Telegram remain possible.
READ THE STORY: The Record
China’s Elite Hackers Expand Targets to European Union Using VPN Tactics
Bottom Line Up Front (BLUF): Chinese state-backed hackers, including the group MirrorFace, are expanding cyber-espionage operations beyond East Asia, now targeting European Union organizations. Notably, these hackers are deploying the open-source SoftEther VPN tool to evade detection, blending in with legitimate traffic to maintain network access.
Analyst Comments: The strategic expansion of Chinese cyber operations into the EU indicates a likely shift toward broader intelligence gathering and an adaptable approach to circumvent traditional defenses. These hackers avoid detection by substituting VPN tools for traditional backdoors, complicating network defense efforts. The persistence of such tactics underscores a rising challenge for organizations to monitor for legitimate software misuse—a task made more complex when malicious actors imitate benign traffic.
FROM THE MEDIA: In a recent report, ESET researchers disclosed that MirrorFace, a cyber-espionage group often associated with Chinese interests in Japan, recently targeted an EU diplomatic organization. The attack reportedly involved a spearphishing email themed around Expo 2025 in Osaka, suggesting a continuing interest in Japan-focused events. ESET’s investigation also confirmed that CloudSourcerer, another Chinese-linked group, has likely been active in EU-focused attacks since early 2022, contradicting earlier assessments. Meanwhile, groups like Flax Typhoon, dismantled in part by the FBI, and Webworm are leveraging SoftEther VPN for persistence, as this legitimate software avoids traditional threat detection, making it an ideal tool to blend in with routine network traffic. ESET advised EU organizations to treat SoftEther VPN instances cautiously and monitor deployments for unauthorized access attempts.
READ THE STORY: CyberScoop
Russia's Tech-for-Troops Deal with North Korea Sparks Concerns of Military Escalation
Bottom Line Up Front (BLUF): U.S., EU, and South Korean officials are expressing alarm over Russia's alleged transfer of military technology to North Korea in exchange for deploying 10,000 North Korean troops to support Russian forces in Ukraine. The deal potentially raises the risk of advanced military capabilities in North Korea, including ballistic missile and nuclear technology.
Analyst Comments: This exchange highlights the desperation in Russia's ongoing military struggle in Ukraine and marks a rare alignment with North Korea for direct military aid. Should North Korea gain new technology from Russia, it could accelerate Pyongyang's military programs, presenting a destabilizing factor in East Asia and beyond. The move signals an intensifying global dimension to the Ukraine conflict as strategic resources and alliances come into play. Monitoring this alliance's developments is critical, as technological support to North Korea could trigger further international sanctions and increase regional tensions.
FROM THE MEDIA: In response to Russia's alleged request for troops, the U.S., EU, and South Korea released statements of concern regarding the reported technology transfers. Secretary of State Antony Blinken disclosed that around 10,000 North Korean soldiers may soon be active in Ukraine, trained for frontline combat tasks such as trench warfare and UAV operations. While specifics on the technology Russia may provide are unclear, experts worry about potential transfers that would strengthen North Korea’s missile and nuclear programs. Secretary of Defense Lloyd Austin indicated that such support could destabilize regional consequences. The transfer would also violate international sanctions to limit North Korea’s military expansion.
READ THE STORY: The Register
China Detains Senior AstraZeneca Executive Amid Broader Investigation
Bottom Line Up Front (BLUF): Leon Wang, AstraZeneca's Executive Vice President for China and Asia, is currently detained as Chinese authorities investigate the pharmaceutical company’s employees for alleged unauthorized imports of cancer drugs and mishandling of patient data. This development signals heightened scrutiny on multinational corporations operating in China and may lead to increased compliance and risk management challenges for foreign businesses in the region.
Analyst Comments: Wang’s detention underscores the elevated risks facing foreign companies in China, especially within regulated sectors like pharmaceuticals. Chinese authorities appear focused on tightening control over the import and distribution of medical products, aligning with broader efforts to centralize sensitive data collection. Companies conducting business in China may need to further bolster compliance mechanisms, especially regarding data management and product handling. AstraZeneca’s case may encourage other multinationals to reassess their operational policies in China and prepare for more assertive regulatory enforcement.
FROM THE MEDIA: AstraZeneca confirmed on Wednesday that Leon Wang, head of its China and Asia operations, is under detention as part of a Chinese government probe into company activities. Chinese authorities are reportedly examining allegations that AstraZeneca employees illegally imported breast cancer treatment Enhertu and liver cancer drug Imjudo from Hong Kong before they were approved on the mainland. Additionally, authorities are investigating possible unauthorized collection of patient data. The probe also involves other AstraZeneca executives, including Eva Yin, a former AstraZeneca official now with BeiGene. AstraZeneca’s stock has dropped significantly since news of the investigation, losing over 12% in the past week.
READ THE STORY: WSJ
AT&T Settles FCC Subsidy Fraud Case for $2.3 Million, Agrees to New Compliance Measures
Bottom Line Up Front (BLUF): AT&T has settled with the FCC for $2.3 million over allegations of improperly claiming funds from pandemic-era broadband subsidy programs. As part of the settlement, AT&T admitted to submitting inaccurate information, leading to fraudulent enrollments in low-income assistance programs. The agreement mandates implementing compliance measures and a dedicated compliance officer to prevent future violations.
Analyst Comments: This settlement underscores the FCC's efforts to enforce accountability in subsidy programs to support underserved communities. AT&T's admission marks a significant instance of a major telco facing repercussions for misusing federal assistance. While the new compliance protocols could help prevent similar incidents, AT&T's involvement in the fraud raises concerns over corporate transparency and responsibility in public benefit programs. This case may prompt the FCC to heighten oversight of subsidy programs to safeguard taxpayer funds.
FROM THE MEDIA: Between May 2021 and the end of 2023, AT&T allegedly enrolled over 3,900 subscribers in federal subsidy programs using invalid information, including repeated use of one person’s credentials to qualify multiple accounts. Additional violations involved unauthorized representatives enrolling users and improper claims for inactive subscribers. The FCC's investigation into these issues concluded with a settlement in which AT&T agreed to pay $2.3 million and appointed a compliance officer to oversee adherence to subsidy program requirements. While AT&T acknowledged some facts in the case, it has maintained that it takes federal compliance seriously and quickly implemented the programs to expand access to affordable internet options during the pandemic.
READ THE STORY: The Register
Canada Orders ByteDance to Wind Down TikTok Operations Over Security Concerns
Bottom Line Up Front (BLUF): Canada has ordered ByteDance to close its Canadian operations for TikTok, citing security risks linked to data handling practices and potential ties to the Chinese government. While the app remains available for personal use, Canadian officials have taken decisive action to mitigate potential national security threats by ByteDance’s local business activities.
Analyst Comments: Canada’s move to force the shutdown of ByteDance's Canadian operations is a bold step in ongoing global scrutiny of TikTok’s data privacy and national security implications. This order could set a precedent, signaling to other nations that more aggressive measures against foreign technology firms with controversial data practices may be considered. The decision reflects Canada’s prioritization of data security and hints at a rising trend of Western governments reducing tolerance for tech firms with perceived government affiliations from adversarial nations. It may further strain Canada-China relations and prompt Canadian TikTok users and businesses to reevaluate their engagement with the platform.
FROM THE MEDIA: Canada’s order, announced November 7, 2024, requires ByteDance to wind down its Canadian business, TikTok Technology Canada Inc., following a national security review under the Investment Canada Act. This decision aligns with previous actions in February 2023 when Canada banned TikTok from government devices. Canadian officials cited the need to address security risks tied to ByteDance’s Canadian presence. Notably, the government clarified that it is not prohibiting Canadians from using TikTok and that the decision to use the app remains a personal choice. A TikTok representative has since responded, asserting the company’s intent to challenge the order legally and warning that the shutdown will impact hundreds of Canadian jobs. TikTok’s parent company, ByteDance, has faced similar scrutiny globally, with the U.S. and EU enacting partial bans over privacy concerns.
READ THE STORY: SA
Cybersecurity Providers See Strong Demand but Hold Back on IPOs Amid Market Uncertainty
Bottom Line Up Front (BLUF): Cybersecurity firms are experiencing high demand for products and increased funding, but only some are pursuing public listings due to volatile market conditions. While M&A activity in the sector is active, only one significant IPO occurred in 2024, reflecting hesitation in entering public markets.
Analyst Comments: Despite robust customer demand and steady growth in cybersecurity investments, industry players are cautious about public listings, mainly due to fluctuating market valuations and recent mixed IPO performances. Increased compliance and security demands have led to solid annual growth projections, but companies remain wary of short-term economic headwinds that could impact market reception. The rise in mergers and acquisitions signals alternative growth strategies, and companies appear more inclined to stay private while preparing for a potential listing if favorable conditions arise.
FROM THE MEDIA: Since 2021, cybersecurity IPOs have slowed, with only one significant listing, Rubrik, in April 2024, raising $752 million. Cybersecurity firms like Darktrace, CyberArk, and Dragos are instead pursuing mergers and acquisitions, including Darktrace's $5.3 billion acquisition by Thoma Bravo and CyberArk's $1.5 billion purchase of Venafi. Mastercard also announced a $2.65 billion acquisition of Recorded Future. Some companies are preparing for IPOs, such as Wiz, aiming to list upon reaching $1 billion in recurring revenue. Despite market hesitancy, the cybersecurity sector is projected to grow 11-12% annually due to increased compliance and cyber risk pressures.
READ THE STORY: WSJ
Items of interest
Chinese Hackers Breach U.S. Telecom Networks, Access Millions of Call Detail Records
Bottom Line Up Front (BLUF): Chinese-backed hacking group "Salt Typhoon" breached U.S. telecommunications networks, accessing potentially millions of Americans’ Call Detail Records (CDRs) — detailed logs containing communication metadata and precise location data. This intrusion allows for extensive surveillance capabilities, raising national security concerns about potential impacts on government, military, and private citizens.
Analyst Comments: This breach represents a significant escalation in cybersecurity threats, with implications for individual privacy and national security. Access to CDRs could enable hostile intelligence operations by revealing the locations and contacts of high-profile figures, military personnel, and other sensitive individuals. The infiltration of legacy telecom infrastructure underscores the challenges of securing older, complex networking systems that may need more modern security patches. As 5G infrastructure expands, such incidents underscore the need for enhanced protections for core national telecom networks, potentially prompting new cybersecurity mandates for telecom providers.
FROM THE MEDIA: Earlier this year, Salt Typhoon, a Chinese hacking group, infiltrated networks of at least ten major U.S. telecom providers, including Verizon and AT&T. Investigators reported that the hackers accessed CDRs, which reveal who users communicate with, when, and where. These records provide a wealth of information, especially with 5G networks’ ability to pinpoint locations within meters, thus offering granular insight into users’ movements. Although officials remain uncertain about the exact volume of data taken or the duration of the hackers’ presence, this intrusion likely began over eight months ago and has proven challenging to mitigate fully. Embedded within older network equipment like routers and switches, Salt Typhoon’s persistence in the system has complicated forensics and containment efforts.
READ THE STORY: POLITICO
Call Detail Record | What is a CDR? (Video)
FROM THE MEDIA: Call Detail Record (CDR) is the detailed record of all the telephonic calls that pass through a telephone exchange or any other telecommunications equipment. The record is maintained by the concerned service provider.
How to make call summary of CDR in Excel | CDR Analyzer (Video)
FROM THE MEDIA: Welcome to [PAK Data Tracker], where every call tells a story! We specialize in unraveling the hidden narratives within call data records (CDRs). Our team of expert analysts transforms raw data into actionable insights, helping you uncover patterns, optimize resources, and make informed decisions.
The selected stories cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not endorse any third-party claims made in its original material or related links on its sites; the opinions expressed by third parties are theirs alone. For further questions, please contact InfoDom Securities at dominanceinformation@gmail.com.