Daily Drop (881): TAT | OpenAI: Canvas | iOS 18.0.1 | 3.8 Tbps DDoS | TW: Gray Zone | Submer | TSMC & Amkor: US Plant | Cartel Guns | Israel: Cyber-Kinetic | BabyLockerKZ | Telegram’s Exodus |
10-05-24
Saturday, Oct 05 2024 // (IG): BB // ScraperDaddy // Cloud Email Harvester
Cyber-Kinetic Warfare: Israel’s Pager Attack and India's Growing Vulnerabilities
Bottom Line Up Front (BLUF): Israel's recent pager-based cyber attack on Hezbollah, killing and injuring thousands, marks a significant escalation in cyber-kinetic warfare. This incident, which combined cyber techniques with physical destruction, raises concerns for countries like India, where dependence on foreign, particularly Chinese, communication technology could expose critical infrastructure to similar threats.
Analyst Comments: The use of cyber-kinetic warfare represents a dangerous evolution in electronic sabotage, as seen in Israel’s attacks on Hezbollah. India's reliance on Chinese-made technology in communication networks and surveillance systems could expose it to similar risks. The potential for these devices to be remotely weaponized poses significant security concerns. Moving forward, India must prioritize building indigenous technologies to minimize reliance on foreign equipment, alongside strengthening cybersecurity protocols for critical infrastructure.
FROM THE MEDIA: On September 17, Hezbollah’s pager devices exploded in a coordinated attack across Lebanon, allegedly orchestrated by Israel’s Defense Forces (IDF) and Mossad. This unprecedented attack killed 11 and injured over 2,700. The following day, similar explosions affected Hezbollah’s walkie-talkies, further escalating the conflict. The sophisticated nature of the cyber-kinetic attack highlights the growing threat of cyberattacks that result in physical destruction. Indian experts have raised alarms over vulnerabilities in the country's telecom and surveillance infrastructure, which relies heavily on Chinese hardware, urging the government to take immediate action to secure these systems.
READ THE STORY: India Today
Submer Secures $55.5M Funding for Sustainable AI Datacenter Cooling
Bottom Line Up Front (BLUF): Submer, a liquid cooling specialist for data centers, has raised $55.5 million to expand operations. With data centers consuming massive amounts of energy and water due to AI workloads, Submer’s immersion cooling technology promises a more sustainable solution by reducing energy use and eliminating water consumption in cooling systems.
Analyst Comments: As AI data center infrastructure expands rapidly, sustainability has become a critical concern, with traditional cooling methods increasingly inadequate. Submer’s liquid cooling technology offers a scalable solution, especially as demands on power and water resources grow. The global focus on AI-driven computing and the environmental toll of data centers make liquid cooling an essential growth area, as evidenced by the expanding use of these systems by major players like Supermicro and Equinix.
FROM THE MEDIA: Submer, headquartered in Barcelona and with manufacturing in Houston, Texas, raised $55.5 million in a funding round led by M&G, with support from Planet First Partners and Norrsken VC. This capital injection will help the company meet the rising demand for sustainable data center cooling solutions, particularly as AI workloads intensify. Traditional air cooling consumes significant energy, and immersion cooling reduces the need for air conditioning by using non-conductive fluids, which also conserve water. AI data center projects worldwide, including Blackstone’s $13.4 billion venture in Northumberland, UK, are driving the push for more efficient and environmentally friendly cooling methods.
READ THE STORY: The Register
Tech Platforms Urged to Act Against Hamas and Hezbollah’s Online Propaganda
Bottom Line Up Front (BLUF): The UN-affiliated Tech Against Terrorism (TAT) initiative has called on social media platforms to take decisive action against online propaganda from Hamas and Hezbollah. Recent attacks in Israel, including a deadly rocket strike in Jaffa, have sparked concerns about terrorist content fueling further violence. Platforms must enhance content moderation to prevent extremist material from escalating conflict.
Analyst Comments: The spread of terrorist propaganda via social media has become a key tool for groups like Hamas and Hezbollah, exacerbating violence and inspiring further attacks. Despite increased pressure on platforms to regulate such content, the ability of these groups to maintain an online presence demonstrates the limitations of current moderation efforts. As conflicts in the Middle East intensify, swift action from both governments and tech companies is essential to curbing the influence of extremist content that could lead to greater regional instability and international threats.
FROM THE MEDIA: Following an attack claimed by Hamas in Tel Aviv, the Tech Against Terrorism initiative warned that online platforms were being exploited to spread extremist content. Hezbollah’s military wing also operates a growing propaganda network online, intensifying since the Israel-Palestine conflict escalated in 2023. TAT has urged governments, tech companies, and civil society to collaborate on moderating this content to prevent further violence and protect communities worldwide. The initiative predicts a high likelihood of additional attacks inspired by the spread of terrorist material online.
READ THE STORY: The Record
TSMC and Amkor Partner to Bring Advanced Chip Packaging to the US
Bottom Line Up Front (BLUF): Taiwan’s TSMC and US-based Amkor Technology have signed a Memorandum of Understanding to establish an advanced semiconductor packaging facility in Peoria, Arizona. This partnership strengthens the US chip supply chain and aligns with the CHIPS Act's goals of boosting domestic semiconductor infrastructure, reducing dependency on overseas operations.
Analyst Comments: The collaboration between TSMC and Amkor is a strategic move to localize advanced semiconductor packaging capabilities in the US, a sector historically dominated by Asia. As geopolitical tensions in East Asia heighten concerns over global supply chain security, this development mitigates risks and ensures the US can handle critical stages of chip production domestically. The move also signals an accelerated push for advanced packaging, crucial for AI and high-performance computing, as traditional transistor scaling nears its limits.
FROM THE MEDIA: TSMC and Amkor Technology’s new facility in Arizona will focus on advanced packaging techniques like fan-out wafer level and 3D chip-on-wafer-on-substrate (CoWoS). Advanced packaging is key to improving chip performance, combining multiple silicon dies into single modules. This partnership supports the US government’s CHIPS Act initiative, a $52 billion package aimed at strengthening US semiconductor manufacturing. With Amkor’s proximity to TSMC’s $40 billion Phoenix fab, the US is positioning itself as a leader in high-tech chip production.
READ THE STORY: The Register
U.S. Wiretap Systems Breached in China-Linked Salt Typhoon Cyberattack
Bottom Line Up Front (BLUF): A sophisticated cyberattack, attributed to China's Salt Typhoon hacking group, compromised the network infrastructure of major U.S. broadband providers, potentially gaining access to U.S. government wiretap systems. This breach represents a significant national security risk, as attackers may have accessed sensitive data from court-authorized wiretaps and other critical communications traffic.
Analyst Comments: This breach underscores the increasing threat posed by nation-state cyber actors, particularly those linked to China, targeting critical U.S. infrastructure. The intrusion into wiretap systems raises serious concerns about the security of sensitive government operations, given the potential for compromised legal surveillance and intelligence data. Salt Typhoon's continued efforts to infiltrate major networks align with broader trends of Chinese cyber espionage targeting critical sectors. The hack highlights the urgent need for enhanced cybersecurity measures in telecommunications and other industries responsible for managing sensitive national security infrastructure.
FROM THE MEDIA: A Chinese-linked hacking group, Salt Typhoon, successfully breached networks of multiple U.S. broadband providers, including AT&T, Verizon, and Lumen Technologies, potentially accessing systems used for lawful government wiretaps. The hackers infiltrated the network infrastructure supporting court-authorized communications intercepts, posing a major national security risk. The breach, which may have lasted for months, also allowed attackers access to broader internet traffic, impacting businesses and individuals across the U.S. and potentially other countries. The U.S. government, alongside private-sector investigators, is currently assessing the extent of data exfiltration and intrusion. Salt Typhoon has been linked to espionage campaigns targeting North America and Southeast Asia since 2020, often focusing on intelligence collection from critical systems.
READ THE STORY: WSJ
Taiwan Faces Rising Financial and Cybersecurity Risks Amid China's Coercion Strategy
Bottom Line Up Front (BLUF): A recent tabletop exercise led by the Foundation for Defense of Democracies (FDD) in Taiwan simulated how China could use economic, cyber, and energy coercion to destabilize the island. The findings highlight Taiwan's vulnerabilities in its financial sector, critical infrastructure, and energy supplies, which China could exploit to compel reunification without resorting to direct military confrontation.
Analyst Comments: The shift in focus from military conflict to nonmilitary "gray zone" tactics mirrors China's broader geopolitical strategy. By targeting Taiwan's economy, cybersecurity, and energy infrastructure, Beijing may seek to weaken Taiwan's society from within, leveraging these disruptions to sway public opinion toward reunification. This approach could be more effective than a military invasion, as it minimizes the risk of triggering a global military response. Taiwan’s government will need to address these vulnerabilities by bolstering its financial resilience, reinforcing cybersecurity defenses, and securing energy independence.
FROM THE MEDIA: In August 2024, a tabletop exercise conducted in Taipei by the FDD and Taiwan Academy of Banking and Finance simulated scenarios in which China applied economic and cyber-coercion to destabilize Taiwan. The simulation demonstrated how Chinese tariffs, disinformation, and cyberattacks could lead to financial instability and widespread outages of Taiwan's banking network and electric grid. One of the more aggressive scenarios involved Chinese civilian vessels severing Taiwan's undersea internet cables, leading to a major communications disruption. Participants also explored the possibility of military drills effectively blockading the island. The exercise's recommendations include securing Taiwan’s energy infrastructure, repatriating financial assets from Hong Kong, and collaborating with the U.S. to build resilience in Taiwan’s financial systems.
READ THE STORY: FP
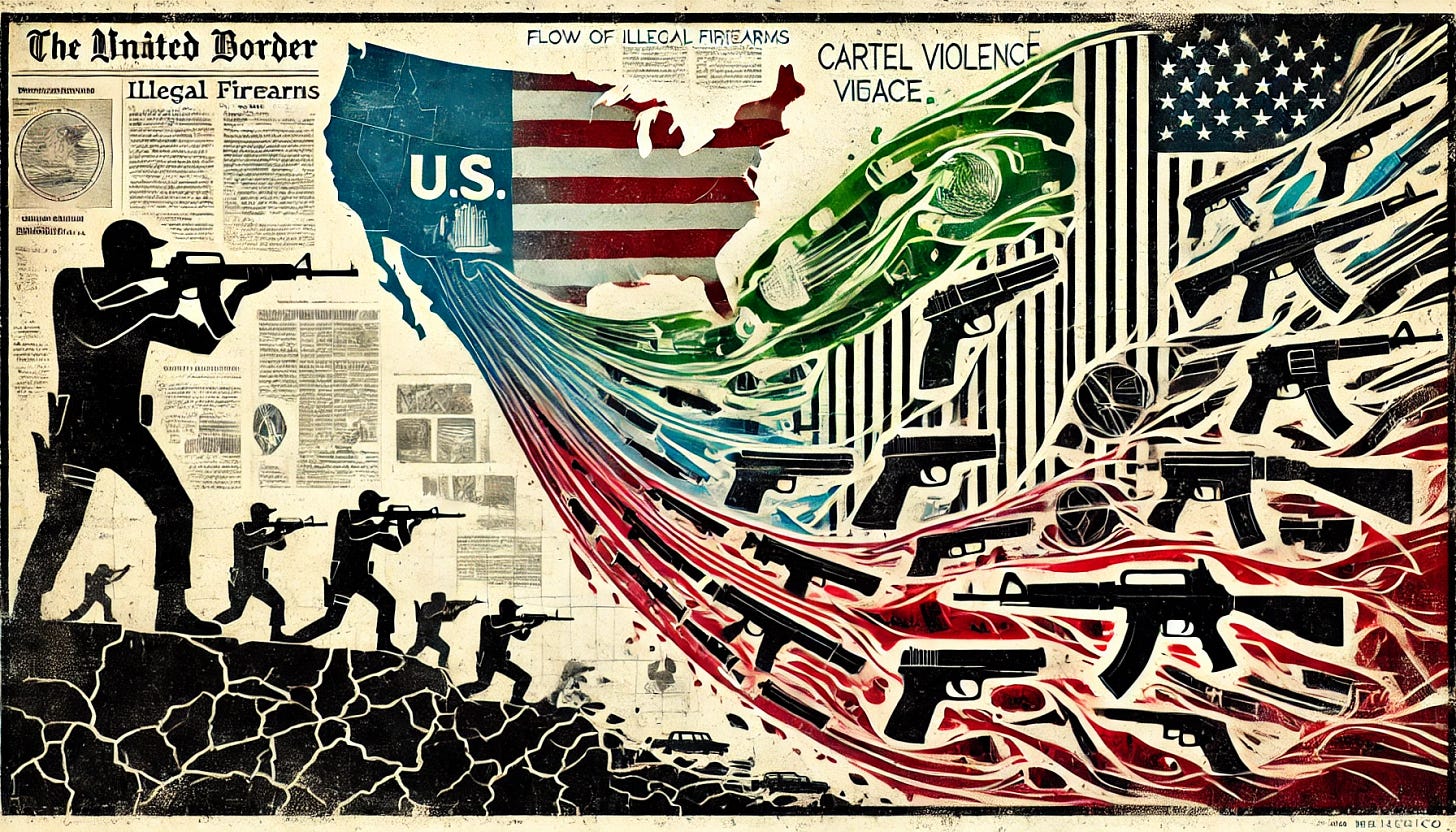
The American Guns Fueling Mexico's Cartel Violence: A Look at Smuggling and Cartel Coveted Weapons
Bottom Line Up Front (BLUF): U.S.-sourced firearms are a major factor in Mexico's escalating cartel violence. Powerful and military-grade weapons, smuggled across the border, are increasingly used by Mexican drug cartels to gain the upper hand against rivals and government forces. Mexico's government has seized over 186,000 weapons since 2006 but estimates 200,000 weapons are smuggled in yearly from the U.S.
Analyst Comments: The cross-border smuggling of firearms into Mexico has become a critical issue, intensifying cartel violence and complicating Mexico's efforts to combat organized crime. Cartels are increasingly turning to high-caliber and military-grade weapons such as Barrett rifles and Miniguns, sourced primarily from the U.S., to maintain dominance. The lawsuit by Mexico against American gun manufacturers underscores the need for more stringent controls over the gun trade. However, the complex legal framework around firearms in the U.S. may challenge the effectiveness of such efforts. If unchecked, this flow of arms will likely exacerbate violence in Mexico and fuel instability in the region.
FROM THE MEDIA: Mexican drug cartels are sourcing increasingly powerful weapons from the U.S., creating a lethal arms race. Firearms such as the Minigun, capable of shooting thousands of rounds per minute, and the Barrett rifle, which can penetrate armored vehicles, are being used in cartel turf wars, according to Mexican authorities. These weapons are often smuggled across the U.S.-Mexico border, with some custom-made for cartel leaders as status symbols. On October 4, 2024, the U.S. Supreme Court agreed to hear a case in which Mexico alleges that American gun manufacturers like Smith & Wesson and Beretta have fueled this violence by negligently flooding Mexico with firearms.
READ THE STORY: WSJ
OpenAI Introduces Canvas for ChatGPT, Enabling Seamless Code Translation and Document Collaboration
Bottom Line Up Front (BLUF): OpenAI has launched a new feature called Canvas, designed to enhance collaboration on coding and writing projects within ChatGPT. Canvas allows users to work on code or text in a side-by-side interface, making it easier to manage complex projects. The feature also includes automatic code translation between languages and customizable document editing tools.
Analyst Comments: Canvas represents a significant advancement in AI-assisted development environments, streamlining workflows for both coders and writers. The ability to translate code between multiple languages instantly could prove a game-changer for developers working across different programming ecosystems. This update brings ChatGPT closer to being an essential tool for professionals in software development, content creation, and education. As OpenAI refines Canvas based on user feedback, this tool becomes a standard feature in collaborative digital workspaces, offering productivity boosts while reducing friction in multi-lingual and multi-task workflows.
FROM THE MEDIA: On October 4, 2024, OpenAI introduced Canvas, a new feature for ChatGPT designed to help users collaborate on writing and programming projects. Canvas allows users to edit code or documents in a dedicated window that sits alongside the AI chat interface, offering real-time collaboration. The tool includes shortcuts for common coding tasks such as debugging, adding comments, and translating code into different programming languages like Python, Java, and C++. Additionally, users can adjust the complexity of the text or code they are working on using sliders for detail and difficulty levels. The feature is available now to ChatGPT Plus and Team users, with plans to roll it out to all users after the beta phase ends.
READ THE STORY: arsTechnica
Apple Patches Critical VoiceOver Vulnerability in iOS 18.0.1 Exposing Saved Passwords
Bottom Line Up Front (BLUF): Apple has patched two security flaws in iOS 18.0.1 and iPadOS 18.0.1, one of which allowed the VoiceOver screen reader to reveal users’ saved passwords audibly. The flaw, tracked as CVE-2024-44204, is especially concerning for those relying on accessibility tools, and users are advised to update immediately.
Analyst Comments: This vulnerability highlights the growing intersection between accessibility and security, as tools meant to aid users can inadvertently expose sensitive information if not properly vetted. Apple's quick response underscores its commitment to user privacy, though this incident may dent confidence, especially with the simultaneous launch of its first password manager. The flaw also raises concerns about how rapidly new features are integrated into iOS without fully considering edge-case vulnerabilities. Future vulnerabilities in critical accessibility features could have far-reaching implications, particularly for users who depend on them daily.
FROM THE MEDIA: On October 4, 2024, Apple released iOS 18.0.1 and iPadOS 18.0.1, addressing two key security bugs, including a critical flaw affecting the VoiceOver screen reader. Tracked as CVE-2024-44204, this issue caused saved passwords to be spoken aloud, posing a privacy risk, especially for visually impaired users. This comes less than a month after iOS 18's release, which introduced the Passwords app—Apple's first built-in password manager. A second vulnerability, CVE-2024-44207, affecting iPhone 16, was also patched. This issue caused iPhones to record audio briefly before notifying users. Apple has advised all users to install the updates immediately to avoid potential exploitation.
READ THE STORY: The Register
Cloudflare Mitigates Record-Breaking 3.8 Tbps DDoS Attack
Bottom Line Up Front (BLUF): Cloudflare successfully mitigated the largest-ever distributed denial-of-service (DDoS) attack, peaking at 3.8 terabits per second (Tbps). The attack targeted multiple sectors, including finance and telecommunications, originating from a global botnet exploiting a critical ASUS router vulnerability (CVE-2024-3080).
Analyst Comments: The record-breaking scale of this DDoS attack highlights a growing trend of increasingly sophisticated and large-volume cyberattacks. The use of compromised IoT devices, including ASUS routers, emphasizes the ongoing risk of insufficiently secured consumer-grade hardware being weaponized in cyber campaigns. The surge in DDoS incidents against critical infrastructure, alongside the use of botnets with advanced command-and-control (C2) techniques, reflects an evolving threat landscape. Organizations will need to invest heavily in scalable, cloud-based defenses to mitigate such hyper-volumetric attacks.
FROM THE MEDIA: On October 4, 2024, Cloudflare revealed it had thwarted the largest known DDoS attack, which reached 3.8 Tbps and persisted for 65 seconds. This attack was part of a broader campaign of hyper-volumetric L3/4 attacks that began in early September, targeting financial services, internet providers, and telecommunications. The attack traffic primarily originated from compromised ASUS routers, DVRs, and other devices in countries such as the U.S., Vietnam, and Russia. The attackers exploited CVE-2024-3080, a critical flaw in ASUS routers, impacting over 157,000 devices. The goal was to overwhelm targeted networks, consuming both bandwidth and CPU resources, and making defense efforts complex. Notably, Cloudflare compared the scale of this incident to the previous record-holding DDoS attack of 3.47 Tbps in 2021 against a Microsoft Azure customer.
READ THE STORY: THN
Election Deepfakes Trigger State Crackdowns, Raising First Amendment Concerns
Bottom Line Up Front (BLUF): A new California law targeting AI-generated political deepfakes has sparked legal challenges over free speech violations. A federal judge has temporarily blocked the law after satirists argued it infringes on First Amendment protections, highlighting tensions between election integrity and free speech rights as AI deepfakes proliferate.
Analyst Comments: The rapid spread of AI technology has outpaced legal frameworks, forcing states like California to act against deepfakes that could distort election outcomes. While the law aims to protect voters from manipulation, its broad language risks overreaching into satire and parody, key elements of political discourse. The legal battles in California and other states are likely to set important precedents regarding the balance between regulating AI misuse and safeguarding free speech, particularly during elections.
FROM THE MEDIA: California’s newly signed deepfake law, which allows individuals to sue over AI-generated election content, has faced its first legal test. Conservative YouTuber Christopher Kohls and the satirical news site The Babylon Bee have filed lawsuits, claiming the law violates the First Amendment. Kohls posted an AI-generated video mimicking Vice President Kamala Harris, which went viral after Elon Musk promoted it on X (formerly Twitter). Governor Gavin Newsom cited the video as an example of harmful deepfakes. However, a federal judge has issued a preliminary injunction against the law, suggesting it could overstep constitutional free speech protections, even as states grapple with growing concerns over AI’s impact on elections.
READ THE STORY: WSJ
New MedusaLocker Ransomware Variant "BabyLockerKZ" Deployed Globally
Bottom Line Up Front (BLUF): A new variant of MedusaLocker ransomware, dubbed "BabyLockerKZ," has been identified targeting organizations worldwide. The threat actor behind this financially-motivated campaign has been active since 2022, focusing on European and South American nations. The variant shares similarities with MedusaLocker but features distinct changes in key management and attack tools.
Analyst Comments: The emergence of BabyLockerKZ as a MedusaLocker variant underscores the adaptive nature of ransomware actors. By modifying key components such as the autorun key and leveraging tools that streamline attack processes, these groups continue to evade detection and enhance efficiency. The shift in target geography, from Europe to South America, could indicate an evolving focus on regions with less robust cybersecurity defenses. Organizations should bolster defenses, particularly against credential theft and lateral movement, and ensure that endpoint detection and response (EDR) solutions are resilient against these attacks.
FROM THE MEDIA: Cisco Talos identified the BabyLockerKZ ransomware variant in a recent report. Active since late 2023, this variant uses similar infrastructure to the original MedusaLocker, such as chat and leak sites, but with altered autorun keys and key storage mechanisms. Initially targeting European nations, the threat actor shifted its focus to South America in 2023, nearly doubling the number of monthly victims. The group utilizes tools like HRSword for disabling antivirus software and Advanced Port Scanner for network mapping, storing attack tools in user folders like Music and Documents. Cisco assesses the group as financially motivated, possibly working as an initial access broker or affiliate of a ransomware cartel.
READ THE STORY: INFOSEC MAG
Telegram’s Cybercriminal Exodus Stalls Amid Regulatory Crackdown
Bottom Line Up Front (BLUF): Following Telegram founder Pavel Durov's arrest and his promise to combat illegal activities on the platform, cybercriminals have discussed migrating to alternative platforms. However, despite these discussions, most are likely to remain on Telegram due to its large user base and extensive functionality. Platforms like Signal, Discord, and Tox have been considered as alternatives, but none offer the same range of tools.
Analyst Comments: The slow exodus of cybercriminals from Telegram highlights the platform’s unique appeal to underground groups, despite increasing law enforcement pressure. Telegram’s bot support, large group chat capabilities, and customization options make it indispensable for many cybercriminal activities. While smaller groups like Bl00dy and RipperSec have set up backup channels elsewhere, the majority are expected to continue using Telegram due to its scale and convenience. Law enforcement agencies are likely to take advantage of Telegram’s renewed cooperation, focusing on the most dangerous actors.
FROM THE MEDIA: Telegram's regulatory challenges began following Pavel Durov’s August 2024 arrest by French authorities for complicity in running an online platform supporting illegal activities. In response, Durov pledged to strengthen cooperation with law enforcement by sharing IP addresses and phone numbers linked to dangerous criminals. Despite concerns from cybercriminals, a mass shift away from Telegram has not occurred. Platforms like Jabber and Tox have been discussed as alternatives, but none provide the combination of tools and reach available on Telegram.
READ THE STORY: The Record
Items of interest
Iranian Missiles Overwhelm Israeli Defenses, Raising Concerns Over Civilian Infrastructure
Bottom Line Up Front (BLUF): A large-scale Iranian ballistic missile attack on Israel briefly overwhelmed some air defenses, highlighting the vulnerability of critical infrastructure. Although damage was limited, experts warn that future strikes could target densely populated areas, increasing the potential for serious harm.
Analyst Comments: The attack demonstrates Iran's growing missile capabilities and their ability to overwhelm even advanced air defense systems like Israel’s Arrow 2 and Arrow 3. While the current damage was minimal, the potential for Iranian missiles to strike more critical targets—such as power plants or residential areas—raises the stakes for Israel’s defensive strategy. As Israel prepares its counterstrike, its primary targets may include Iran’s missile production facilities and stockpiles. This escalation signals a volatile phase in regional conflict, with potential repercussions for civilian populations.
FROM THE MEDIA: On October 3, 2024, Iran launched one of the largest ballistic missile barrages in recent history, firing 180 missiles at various Israeli sites, including the Nevatim and Tel Nof air bases. Independent analysts using satellite imagery confirmed that 32 Iranian missiles hit the Nevatim air base, overwhelming Israeli defenses in some areas. Although damage to military assets was limited, this event has raised alarms about the future vulnerability of civilian infrastructure. Israel’s Prime Minister Benjamin Netanyahu has promised a strong response, while Iran has warned it could target Israeli energy facilities in future strikes.
READ THE STORY: WSJ
Israel's Iron Dome explained by Professor Michael Clarke (Video)
FROM THE MEDIA: The Iron Dome is part of a multi-layer air-defence system which is understood to be one of the most effective in the world.
Did Israel’s Iron Dome Fail Against Iran’s Missiles? (Video)
FROM THE MEDIA: The Iranian military has claimed that 90% of its missiles hit Israeli targets. Pictures from Israel suggest Iran’s attack caused more physical damage than the attack in April. Did Israel’s air defense systems fail? Palki Sharma tells you.
The stories selected cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not endorse any third-party claims made in their original material or related links on their sites; the opinions expressed by third parties are theirs alone. For further questions, please contact InfoDom Securities at dominanceinformation@gmail.com.