Friday, July 15, 2022 // (IG): BB //Weekly Sponsor: The Fintel Brief
Chinese hackers targeted US reporters before Capitol attack and Russian invasion, report finds
FROM THE MEDIA: Chinese-aligned hackers targeted White House correspondents and other U.S. political reporters in the run-up to the January 6, 2021 attack on the U.S. Capitol as well as the Russian invasion of Ukraine, according to a new report from cybersecurity firm Proofpoint. The report highlights the cybersecurity risks facing journalists and other members of the news media, who have long been attractive targets for cyberspies.
The threat actor Proofpoint tracks as TA412 carried out a series of phishing attempts targeting U.S.-based journalists since early 2021, according to the report. Researchers believe the attackers are aligned with Chinese government interests. In 2020, Microsoft reported the threat actor, which it dubbed Zirconium, had targeted those connected to the U.S. presidential campaign as well as at think tanks that focused on international relations.
READ THE STORY: The Record
PayPal phishing kit added to hacked WordPress sites for full ID theft
FROM THE MEDIA: A newly discovered phishing kit targeting PayPal users is trying to steal a large set of personal information from victims that includes government identification documents and photos. Over 400 million individuals and companies are using PayPal as an online payment solution. The kit is hosted on legitimate WordPress websites that have been hacked, which allows it to evade detection to a certain degree.
Researchers at internet technology company Akamai found the phishing kit after the threat actor planted it on their WordPress honeypot. The threat actor targets poorly secured websites and brute-forces their log in using a list of common credential pairs found online. They use this access to install a file management plugin that allows uploading the phishing kit to the breached site.
READ THE STORY: Bleeping Computer
Tenet Health sued after affiliate hack, health data theft impacting 1.2M
FROM THE MEDIA: A lawsuit has been filed against Tenet Healthcare and its Texas affiliate Baptist Health System following Tenet's breach notification to 1.2 million patients that their data was stolen during a systems’ hack in March.
The patient who filed the lawsuit is seeking $1 million in monetary relief for the class action and claims his individual damages are less than $75,000.
Filed in the District Court of Dallas County, the suit claims the stolen data was not encrypted ahead of the cyberattack. It should be noted that under the Health Insurance Portability and Accountability Act data encryption is not required if the provider has a documented, alternative security mechanism in place.
READ THE STORY: SCMAG
North Korean Hackers Targeting Small and Midsize Businesses with H0lyGh0st Ransomware
FROM THE MEDIA: An emerging threat cluster originating from North Korea has been linked to developing and using ransomware in cyberattacks targeting small businesses since September 2021. The group, which calls itself H0lyGh0st after the ransomware payload of the same name, is being tracked by the Microsoft Threat Intelligence Center under the moniker DEV-0530, a designation assigned for unknown, emerging, or a developing group of threat activity. Targeted entities primarily include small-to-midsize businesses such as manufacturing organizations, banks, schools, and event and meeting planning companies.
READ THE STORY: THN
DHS board: No one used software inventories to find vulnerable Log4j deployments
FROM THE MEDIA: None of the nearly 80 organizations that the Cyber Safety Review Board canvassed for its first report, including many federal agencies, used software inventories to find vulnerable Log4j deployments. CSRB found not every organization even had software bills of materials (SBOMs), machine-readable inventories of components and how they relate because data formats haven’t been standardized.
The Department of Homeland Security tapped CSRB to review the U.S. response to the Log4j vulnerability, one of the most serious to date, publicly disclosed on Dec. 10. In its report released Thursday, CSRB recommended SBOM tooling and adoptability be improved to support faster software supply chain vulnerability response.
READ THE STORY: FEDSCOOP // CNET // DUO
Russian cyber threat to Canada worse than previously reported: CSE
FROM THE MEDIA: Russia’s cyber operations following its invasion of Ukraine have “almost certainly” been more extensive than what has been publicly reported, and Canada is among the targets, the Communications Security Establishment said.
The CSE’s Canadian Centre for Cybersecurity said in a threat bulletin issued Thursday “the scope and severity of cyber operations related to the Russian invasion of Ukraine has almost certainly been more sophisticated and widespread than has been reported in open sources.”
Christopher Parsons, a senior researcher at University of Toronto’s Citizen Lab, said the CSE’s warning should be taken seriously. “Anyone who has critical infrastructure under their control, or is interfacing with it, needs to take what they’re saying seriously. They’re not in the habit of trying to spook Canadians.”
READ THE STORY: National Post
Russia tried to spy on the US, NATO and Brazil
FROM THE MEDIA: Microsoft said in a statement this week that Russia is trying to spy on 42 countries, including Brazil. The operations come amid an espionage war between Russian intelligence agencies and America’s Cyber Command in the wake of the war in Ukraine. US-based Microsoft said Moscow hit 128 targets around the world, including governments, think tanks, humanitarian aid agencies, IT companies and companies responsible for critical infrastructure in countries.
In 29% of attacks, Russian hackers were able to break into their targets’ computers. However, Microsoft did not elaborate on which countries the data was stolen from or what kind of information the Russians were looking for. Moscow denies any espionage or cyber activity in the Ukraine war.
READ THE STORY: TCT
How China could follow Russia’s Ukraine playbook
FROM THE MEDIA: Amid the restructuring of the global order that has been accelerated by Russia’s invasion of Ukraine, the evolving position of China had been lost in the fog of war. The heads of the UK’s security service (MI5) and US Federal Bureau of Investigation sought to disperse this fog with a rare joint press conference warning of the “immense threat” from China.
Public speeches by heads of intelligence services are not as rare as they once were, but they are uncommon. The optics of a shared public platform was to underline the magnitude of the importance of the message. So, what is the realistic threat from China and how should we interpret it?
The MI5 director general Ken McCallum said in the briefing that they are now dealing with seven times the number of investigations involving China compared to 2018. He said: “The most game-changing challenge we face comes from the Chinese Communist Party. It’s covertly applying pressure across the globe.”
READ THE STORY: Asiantimes
Report says Alibaba's executives hauled in by Chinese officials over data heist
FROM THE MEDIA: The Wall Street Journal has reported that e-commerce giant Alibaba's executives, including Cloud vice president Chen Xuesong were hauled in by Chinese officials over a massive data heist. Following the release of the report, the company's shares slumped 5.7 per cent at the opening in Hong Kong. Previously, the personal information of more than 1 billion Chinese residents was hacked in a cyber attack as per the Shanghai police. Citing cybersecurity researchers, WSJ reported that a dashboard for managing the database was left open on the internet for over a year without a password.
Launching an inspection since the theft was discovered, the Shanghai police said that the data was hosted on Alibaba's cloud platform. If Alibaba indeed was connected to the alleged breach then it would be "at the mercy of Beijing's regulators," according to the chief investment officer at Kaiyuan Capital in Hong Kong, Brock Silvers.
READ THE STORY: WION
China-backed hackers targeted White House journalists before January 6
FROM THE MEDIA: Researchers at cybersecurity company Proofpoint said they have observed the China-backed advanced persistent threat group, TA412, also known as Zirconium, engaging in several reconnaissance phishing campaigns since early last year. Proofpoint says it witnessed five separate phishing campaigns in January and February 2021 targeting U.S.-based journalists, notably those covering U.S. politics and national security. However, the researchers noted a “very abrupt shift in targeting of reconnaissance phishing” in the days leading up to the January 6 attack on the U.S. Capitol, with the hackers focusing on Washington, D.C. and White House correspondents.
READ THE STORY: TechCrunch
China accuses India of a cyber attack on Pak using Chinese code name
FROM THE MEDIA: Cyber warfare is no longer merely the stuff of sci-fi movies such as The Matrix, Skyfall, and V for Vendetta, and is being practised by countries across the globe, as the most effective way to hobble the military and economic capabilities of their enemies and to create social and cultural strife.
The art of making war in the current century will be more than just massed attacks, deploying lethal fighter aircraft and tanks to conquer and occupy enemy territory.
With technology becoming the brain and brawn of modern states and their armies, war planners see cyber tools as the next generation of destructive weapons, capable of degrading the war-making capabilities of rivals.
READ THE STORY: News 9 Live
Scrutiny of Alibaba in Record Breach May Ensnare All China Tech
FROM THE MEDIA: Questions surrounding Alibaba Group Holding Ltd.’s role in China’s largest known cybersecurity breach may fuel Beijing’s resolve to clamp down on domestic tech giants and accelerate a move away from their private cloud services.
Researchers studying the leaked data of close to a billion Chinese residents earlier this month have noticed hallmarks of Alibaba’s cloud service, including the domain name of the hosting service. This week, executives of the company’s cloud division, known as Aliyun, were summoned by Shanghai authorities in relation to that data dump, the Wall Street Journal reported, citing sources familiar with the matter.
READ THE STORY: Bloomberg
Advanced tools, tactics required to defend latest attack variant — ‘DeepSea phishing’
FROM THE MEDIA: Phishing comes with a simple premise – lure someone to interact with a malicious link, file, or credentials-input, disguised as a legitimate email or website. The financial impact of phishing attacks quadrupled over the past six years, with the average cost for U.S. companies rising to $14.8 million in 2021, compared with $3.8 million in 2015. This is so, in part, because growing awareness has pushed hackers to create even more sophisticated means to plunder log-in information, or to lure employees to click on a malware-infected link – AKA next-gen, or “DeepSea” phishing.
These attacks use novel and rarely seen phishing techniques, often employing several layers of deception in parallel. Take this recent phishing attempt, which was identified by Perception Point’s Incident Response team: hackers first used an irregular URL structure to evade standard email threat detection systems, and sent users through a very convincing but fake two-factor authentication.
READ THE STORY: Security Boulevard
This serious firmware flaw affects a whole load of Lenovo laptops
FROM THE MEDIA: Three serious security vulnerabilities has been discovered, and patched, across a whole slew of Lenovo laptops. Cybersecurity experts from ESET uncovered the issue in the ReadyBootDxe driver used by some Lenovo notebooks, as well as two buffer overflow issues found in the SystemLoadDefaultDxe driver, potentially allowing threat actors to hijack the startup routine of Windows installations. The Yoga, IdeaPad, Flex, ThinkBook, V14, V15, V130, Slim, S145, S540, and S940 Lenovo lines are all affected, counting more than 70 endpoint(opens in new tab) models.
READ THE STORY: TechRadar
Counteracting Nation-State-Sponsored Cyberattack Groups
FROM THE MEDIA: The Russia-Ukraine war has put the world on high alert not just to the threat of physical attacks but the potential for highly-funded, sophisticated nation-state cyberattacks, as well. The worry is not only permeating government agencies but also businesses around the globe, and are not without merit. In light of recent geopolitical shifts, U.S. intelligence recommended organizations, both large and small, become more vigilant in their cybersecurity practices.
Routine testing of your organization’s attack surface can thwart random cybercriminals. But is this approach enough to prevent you from becoming the target of an advanced and dynamic state-sponsored attacker? While it is difficult to discern whether your organization was targeted as part of a concentrated hacking campaign, businesses equipped with threat intelligence and chronicled attack patterns can narrow down the list of suspects in the event of a security incident. With meaningful insights, executives can lead with confidence and notify appropriate parties such as law enforcement or legal teams.
READ THE STORY: Security Boulevard
NSO Prompts Apple To Add A ‘Lockdown Mode’ To Its Devices
FROM THE MEDIA: Israeli software developer NSO Group’s frequent targeting of iPhones has led to multiple rounds of patches, a federal lawsuit, and Apple instituting a notification program to inform customers their devices have been compromised. Apple’s next move in this particular arms race will help defend users against malware deployment by government agencies, many of which use exploits purchased from NSO Group and its competitors.
This addition won’t be difficult to deploy, making it much more user-friendly than other options. A single button press in the Options is all it takes. The phone reboots in “lockdown mode,” blocking most attachments contained in messages, preventing the phone from previewing web links, and — somewhat surprisingly — disabling wired connections to other devices.
READ THE STORY: TechDirt
Journalists Emerge as Favored Attack Target for APTs
FROM THE MEDIA: Targeted phishing attacks are traced to multiple threat actors who have each independently focused on stealing credentials and sensitive data and tracking the geolocation of journalists.
In a Thursday report by Proofpoint, researchers outline individual efforts by advance persistent threat (APT) groups who they say are aligned with China, North Korea, Iran and Turkey. Attacks began in early 2021 and are ongoing, researchers said.
According to the report, the APTs are acting independently of each other but share the same overall goal of targeting journalists. Tactics are also similar, with threat actors targeting email and social-media accounts as phishing inroads in cyberespionage campaigns.
READ THE STORY: Threatpost
Inside The Russian Cybergang Thought To Be Attacking Ukraine—The Trickbot Leaks
FROM THE MEDIA: Reports concerning the impact of cyber operations, directed at both Russian and Ukrainian targets, have been many and varied. While it's a step too far, in the eyes of most experts, to describe what has been happening as cyber warfare, it's certainly accurate to suggest that ongoing cyber incidents are a reality. Beyond the ever-present disinformation campaigns, a highly organized cybercrime group appears to have entered the field of conflict. In an apparent change of tactics from being a purely financially motivated criminal business, this Russian cybergang is thought to be Trickbot.
READ THE STORY: Forbes
Bandai Namco confirms hack by ransomware group; confidential information stolen
FROM THE MEDIA: Bandai Namco, a name the fighting game community knows well thanks to titles like Tekken, Dragon Ball FighterZ, and Soul Calibur, has confirmed that they've been hacked and had confidential information stolen by ransomware group ALPHV. First wind of this reached public ears back on Monday when vx-underground, which proclaims to be the largest collection of malware source code, samples, and papers on the internet, posted the news on Twitter. Bandai has since confirmed the hack with Video Game Chronicle and replied with statements on the situation.
READ THE STORY: Eventhubs
MaliBot malware quickly gaining traction
FROM THE MEDIA: The MaliBot banking trojan has become the third-most prolific malware targeting Android users in June, behind the AlienBot malware-as-a-service family and the Anubis banking trojan, despite only emerging last month, ZDNet reports. MaliBot has been spread through SMS hijacking like FluBot malware, which it had supplanted after being disrupted by law enforcement in May, a report from Check Point noted. "While it's always good to see law enforcement successful in bringing down cybercrime groups or malwares like FluBot, sadly it didn't take long for a new mobile malware to take its place," said Check Point Software Vice President of Research Maya Horowitz. The report also said that financial apps have been targeted by the AlienBot malware, while continued updates for Anubis have ensured its dominance despite being first identified six years ago.
READ THE STORY: SCMAG
Jewelers' Ransomware Dilemma
FROM THE MEDIA: Last year's cyberattack on Graff came as a stark reminder to the jewelry world that nobody's safety is guaranteed. Many months later it has emerged that the exclusive London jeweler handed over the Bitcoin equivalent of $7.5m to prevent the hackers who had already released details of many high-profile clients from releasing additional data.
Hackers stole their list of high-profile clients in October 2021, which included former US President Donald Trump is reportedly among those whose files have been stolen. Also on the list are Oprah Winfrey, Tom Hanks, Samuel L Jackson, Tony Bennett, Alec Baldwin, Ghislaine Maxwell, footballer David Beckham, Saudi Crown Prince Mohammed bin Salman and Tetra Pak billionaire Hans Rausing. The theft had the potential to cause huge damage, not least to anyone who had purchased an item of value for somebody other than their spouse or partner.
Any business that has a computer - that's to say any business of any description anywhere in the world - is vulnerable to ransomware attacks, when hackers threaten to publish data they've stolen, or permanently block the owner's access to it, unless a ransom is paid.
READ THE STORY: IndexOnline
Google ChromeOS Flex comes out of beta to help stop ransomware threats
FROM THE MEDIA: Today, Google announced that its free, chromium-based operating system, ChromeOS Flex, is coming out of beta. ChromeOS Flex will provide PC and MAC users with a cloud-driven secure operating system that they can deploy via USB, and manage alongside other Chrome OS devices. While Chrome OS Flex has the same codebase as Chrome OS, unlike the latter, ChromeOS Flex can be installed on Windows and Mac machines as well, opening the door to millions of potential new users.
Since Google made ChromeOS Flex available for early access users in February 2022, there are now over 400 devices that are now certified for Flex, and can be managed through the Google Admin console with the Chrome Enterprise Upgrade.
READ THE STORY: Venturebeat
Items of interest
State-Backed Hackers Targeting Journalists in Widespread Espionage Campaigns
FROM THE MEDIA: Nation-state hacking groups aligned with China, Iran, North Korea, and Turkey have been targeting journalists to conduct espionage and spread malware as part of a series of campaigns since early 2021. "Most commonly, phishing attacks targeting journalists are used for espionage or to gain key insights into the inner workings of another government, company, or other area of state-designated import," Proofpoint said in a report shared with The Hacker News.
The ultimate goal of the "sustained" intrusions, the enterprise security firm said, is to gain a competitive intelligence edge or spread disinformation and propaganda. Proofpoint said it identified two Chinese hacking groups, TA412 (aka Zirconium or Judgment Panda) and TA459, targeting media personnel with malicious emails containing web beacons and weaponized documents respectively that were used to amass information about the recipients' network environments and drop Chinoxy malware.
READ THE STORY: THN
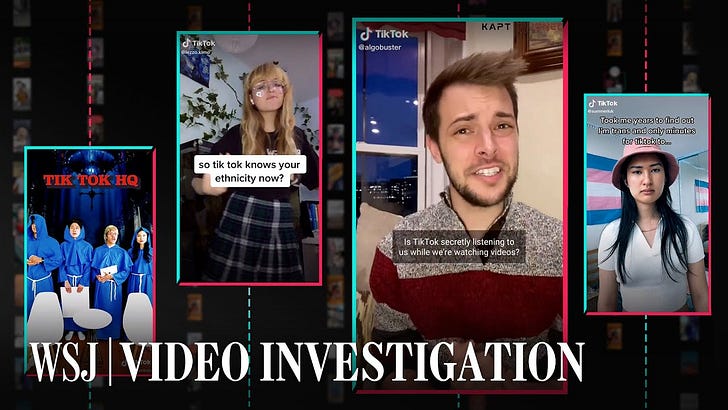
How TikTok's Algorithm Figures You Out (Video)
FROM THE MEDIA: The Wall Street Journal created dozens of automated accounts that watched hundreds of thousands of videos to reveal how the the TikTok algorithm knows you so well A Wall Street Journal investigation found that TikTok only needs one important piece of information to figure out what you want: the amount of time you linger over a piece of content. Every second you hesitate or rewatch, the app is tracking you.
Bluetooth Signals Can Be Fingerprinted And Used To Track Smartphones (Video)
FROM THE MEDIA: University of California San Diego scholars have discovered for the very first time ever that Bluetooth signals may be fingerprinted so that devices can be tracked (and, as a result, individuals). The identification is based on flaws in a Bluetooth chipset introduced during its manufacturing process, which results in a "unique physical-layer fingerprint."
These open source products are reviewed from analysts at InfoDom Securities and provide possible context about current media trends in regard to the realm of cyber security. The stories selected cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not specifically endorse any third-party claims made in their original material or related links on their sites, and the opinions expressed by third parties are theirs alone. Contact InfoDom Securities at dominanceinformation@gmail.com