Wednesday, Oct 22, 2025 // (IG): BB // GITHUB // SN R&D
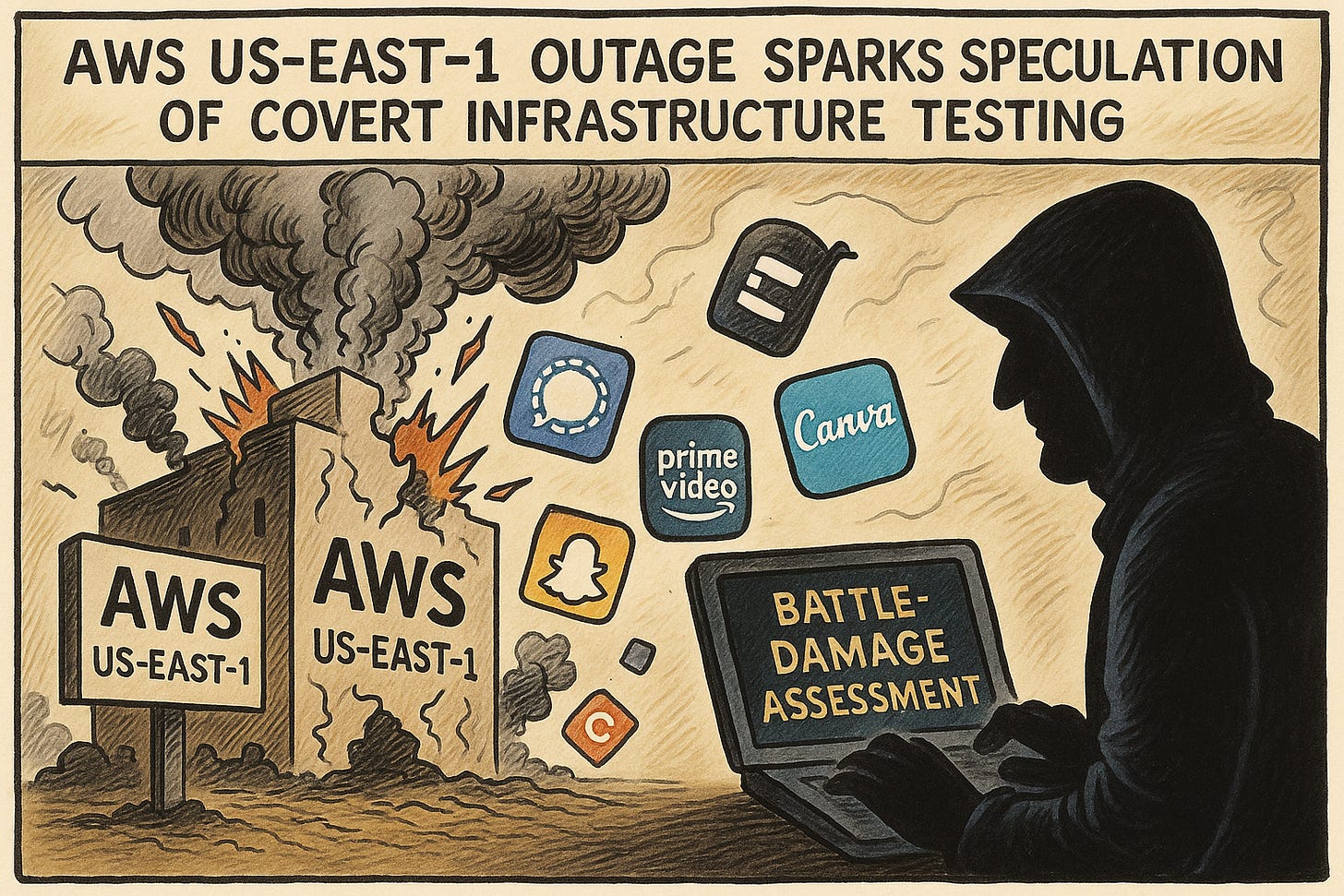
AWS US-East-1 Outage Sparks Speculation of Covert Weapons Testing
Bottom Line Up Front (BLUF): AWS’s US-East-1 region experienced a widespread service disruption, officially blamed on internal DNS misconfiguration affecting DynamoDB. However, the outage’s scale, the high-value region targeted, and its ripple effects across global services suggest a potential battle-damage assessment (BDA) by a capable adversary. While there’s no proof of cyber intrusion, the incident aligns with gray-zone tactics used in digital resilience probing — raising red flags for defenders of cloud-reliant systems.
Analyst Comments: AWS’s incident report cited “a configuration error in a DNS resolution path that supports DynamoDB” as the root cause. The error caused cascading failures across services, including EC2, S3, Lambda, and IAM, affecting applications like banking apps, airline check-in systems, and government platforms. The outage lasted nearly three hours. No external threat actor was acknowledged, but the region targeted — US-East-1 in Northern Virginia — handles more traffic and sensitive workloads than any other AWS region. It’s also adjacent to critical fiber and government infrastructure. Previous cyber-wargame models have noted that inducing failure in this zone can offer real-time visibility into global service dependencies and self-healing behavior — key objectives in BDA-style operations.
READ THE STORY: Freebuf
SSB View of Alleged NSA Orchestrated on National Timing Center
Bottom Line Up Front (BLUF): Chinese cybersecurity officials have publicly accused the U.S. National Security Agency (NSA) of executing a sustained cyberespionage campaign against the National Time Service Center (NTSC). The multi-phase operation—traced between August 2023 and mid-2024—allegedly involved advanced malware, including variants resembling the NSA’s DanderSpritz platform. According to China’s national emergency response team (CNCERT), attackers maintained long-term access, stole sensitive data, and used foreign-branded mobile device exploits to surveil NTSC staff.
Analyst Comments: Chinese state-affiliated security researchers, the cyberattack began in mid-2023 and evolved through several stages: initial access using early versions of Back_Eleven, expansion via lateral movement, and full compromise using stealthy implants. Malware was embedded in critical NTSC systems, with some implants disguised as legitimate Windows services and using hijacked InprocServer32 registry keys for persistence. One implant—New_Dsz_Implant—was described as nearly identical to DanderSpritz but updated with features to simulate human behavior to evade detection. CNCERT claims the campaign used 42 different payloads and attributes it directly to the NSA’s infrastructure.
READ THE STORY: CCTV NEWS
Anthropic Tailors Claude for Biotech: AI Model Targets Genomics, Clinical Trials, and Lab Workflows
Bottom Line Up Front (BLUF): Anthropic is moving aggressively into the life sciences sector, integrating its Claude AI models with biomedical platforms and lab tools used in genomics, clinical documentation, and drug discovery. Companies like Novo Nordisk and Sanofi are already deploying Claude for use cases like slashing clinical study paperwork from 10 weeks to 10 minutes. The shift marks a growing trend toward domain-specialized AI and signals intensified competition between Anthropic, OpenAI, and Google in healthcare R&D.
Analyst Comments: As the hype around general-purpose AI tapers off, biotech offers a grounded, high-impact vertical with a real need for automation. Claude’s success in scientific environments hinges on its low hallucination rate, citation-traceable outputs, and compatibility with tools researchers use. That gives it an advantage over LLMs focused on casual productivity or consumer use. However, the challenge will be proving clinical and regulatory reliability at scale—a bar no model has cleared yet. The fact that no AI-discovered drugs have yet passed approval underscores just how long the road still is, despite flashy announcements.
READ THE STORY: FT
Google Tracks Rapid Evolution of COLDRIVER Malware Arsenal: New ROBOT Family Targets High-Value Intel
Bottom Line Up Front (BLUF): Google’s Threat Intelligence Group has linked three new malware families—NOROBOT, YESROBOT, and MAYBEROBOT—to the Russian state-sponsored APT group COLDRIVER. The group’s shift in tooling and tactics reflects a marked increase in operations tempo, with malware iterating rapidly following public disclosure of earlier implants like LOSTKEYS. The new strains are designed for stealth, modularity, and intelligence collection from compromised high-value targets.
Analyst Comments: The new ROBOT malware suite showcases aggressive development, with YESROBOT likely a stopgap and MAYBEROBOT emerging as the more scalable implant. These tools exploit user interaction via fake CAPTCHA prompts to launch PowerShell payloads, mimicking “ClickFix”-style delivery chains. Python installation artifacts in early variants suggest a fast-moving dev cycle where stealth improves with each iteration. The emphasis on DLL sideloading, C2 evasion via HTTPS, and selective targeting points to an intel-gathering mission, not mass exploitation. This campaign reinforces the importance of behavioral detection and DLL sideloading visibility for defenders.
READ THE STORY: THN
Veeam Acquires Securiti AI for $1.73B to Tighten Cloud Data Security and AI Governance
Bottom Line Up Front (BLUF): Veeam Software will acquire Securiti AI for $1.73 billion in a significant push to consolidate data protection, privacy, and governance in the cloud—especially where AI workloads are concerned. The move aims to position Veeam ahead of competitors like Rubrik and Commvault by integrating Securiti’s Data Command Center with Veeam’s backup and recovery suite. The deal is expected to close in Q4 2025.
Analyst Comments: Veeam will integrate Securiti AI’s flagship Data Command Center—designed to manage fragmented cloud data environments—into its existing portfolio. The company says the combined offering will help clients not only recover from ransomware and data loss but also proactively safeguard and govern sensitive data used in AI applications. Insight Partners, Veeam’s majority stakeholder, continues to expand the firm’s valuation post-acquisition, following a $2B secondary stake sale in 2024. JPMorgan is financing the deal; Morgan Stanley advised Securiti AI.
READ THE STORY: Reuters
CISA Goes Dark During F5 Breach Fallout, Threat Sharing Disrupted Amid Layoffs and Legal Friction
Bottom Line Up Front (BLUF): In the wake of a nation-state breach targeting F5’s BIG-IP product line, U.S. federal threat-sharing channels have largely gone silent. Axios reports that the Cybersecurity and Infrastructure Security Agency’s (CISA) Stakeholder Engagement Division—responsible for public-private coordination—has halted routine outreach, leaving defenders in the dark during an active threat campaign. The disruption coincides with a wave of government layoffs, a shutdown, and the expired liability protections that previously enabled private-sector info-sharing.
Analyst Comments: A live exploitation campaign is hitting widely deployed infrastructure (F5’s BIG-IP), yet one of the core mechanisms for alerting critical infrastructure operators has gone offline. The fact that CISA is hosting some internal calls doesn’t offset the broader collapse in outbound threat coordination. Between restructuring, loss of talent, and legal chilling effects post-liability lapse, defenders are flying partially blind. If CISA can’t reliably act as a clearinghouse during major breaches, expect industry trust—and cooperation—to degrade quickly. The F5 incident is a stress test, and the system isn’t passing so far.
READ THE STORY: Axios
OpenAI Launches ChatGPT Atlas, an AI-Powered Browser to Challenge Chrome’s Dominance
Bottom Line Up Front (BLUF): OpenAI has officially entered the browser wars with the launch of ChatGPT Atlas, an AI-first web browser built around its flagship chatbot. Atlas includes an embedded ChatGPT assistant capable of summarizing, analyzing, and interacting with websites, positioning the tool as both a browser and a personal agent. Initially released on macOS, Atlas will soon roll out to Windows, iOS, and Android.
Analyst Comments: By combining assistant functionality, web automation (agent mode), and native integration with OpenAI’s models, Atlas shifts the user experience from “find information” to “get tasks done.” This move could create new surface areas for defenders and security architects: AI-driven automation introduces risks from autonomous browsing, sensitive data handling, and spoofed site interactions. Expect browser threat models to evolve rapidly—especially around session hijacking, prompt injection, and extension-layer exploits. On the commercial side, this raises the stakes for data privacy, as persistent AI agents increasingly observe and act on user behavior across the web.
READ THE STORY: Reuters
Army Expands Cyber Adviser Role to Cover Electronic Warfare, Information Advantage
Bottom Line Up Front (BLUF): The U.S. Army has expanded the role of its Principal Cyber Adviser (PCA), Brandon Pugh, to include oversight of electronic warfare (EW) and information superiority efforts. This move, directed by Army Secretary Daniel Driscoll, aims to unify oversight across increasingly converging domains on the modern battlefield, ensuring EW and information operations receive the same level of strategic attention as cyber.
Analyst Comments: By consolidating cyber, EW, and information advantage under a single civilian adviser, the Army acknowledges what operators have known for years: these domains are operationally inseparable. The expanded role influences Pugh over cross-domain investment strategies, including defensive and offensive cyber capabilities. The office is also evaluating new “cyber toolkit options” with a likely emphasis on active defense and precision strike-enabling tech. This signals a more integrated approach to spectrum dominance and strategic communications—something China and Russia have already institutionalized in their doctrine. Civilian-military alignment will be key to maintaining operational readiness in multi-domain operations (MDO).
READ THE STORY: Executive Gov
Geopolitics in Flux: U.S., China, and Middle East Realign as Russia Loses Ground
Bottom Line Up Front (BLUF): As Russia’s influence wanes under prolonged conflict and economic isolation, the U.S., China, and key Middle Eastern powers are actively redrawing regional power structures—both in physical geography and digital infrastructure. In an essay for RealClearDefense, Irina Tsukerman argues that the current great-power struggle is increasingly fought not just with tanks and sanctions, but through networks, data flows, and digital platforms, including China’s expanding Digital Silk Road initiative.
Analyst Comments: While Russia stagnates under sanctions and military attrition, China is exporting telecom infrastructure, surveillance tech, and cloud ecosystems to strategic partners under the guise of development. The U.S. is countering through complex security alliances and emergent digital coalitions. Still, many Middle Eastern states are now playing both sides—hosting Chinese platforms while deepening military ties with Washington. The collapse of Russian clout opens the door to new cyber partnerships, disinformation battlegrounds, and a scramble for data sovereignty. Expect intensified competition over digital standards, internet governance, and AI-enabled influence operations in the Global South.
READ THE STORY: RealClearDefense
China-Linked Salt Typhoon Breaches European Telecom via Citrix Exploit, Deploys Stealth Backdoor
Bottom Line Up Front (BLUF): China-backed APT group Salt Typhoon (aka Earth Estries/GhostEmperor) compromised a European telecom provider in July 2025 by exploiting a Citrix NetScaler Gateway vulnerability. The attackers deployed a stealthy backdoor (SNAPPYBEE/Deed RAT) using DLL sideloading via trusted antivirus software and evaded detection using SoftEther VPN and LightNode VPS infrastructure. Darktrace detected and contained the intrusion before a significant impact.
Analyst Comments: This incident shows Salt Typhoon evolving its tradecraft precisely: abusing Citrix for initial access, masquerading behind SoftEther VPN traffic, and deploying malware via trusted AV binaries to slip past defenses. Using SNAPPYBEE, LightNode VPS for C2, and IE-style POST requests underscores high operational security (OPSEC) and obfuscation. With Citrix appliances repeatedly exploited by state actors, organizations still exposing them to the internet without segmentation or MFA are tempting targets. For defenders, this reinforces the need for behavioral analytics and anomaly detection—signature-based tools alone are blind to staged lateral movement and AV sideloading tricks.
READ THE STORY: Security Affairs
Myanmar Military Raids Notorious Scam Hub, Seizes Starlink Gear—But Motives Questioned
Bottom Line Up Front (BLUF): Myanmar’s military junta claims to have raided and seized control of KK Park, a major cyber scam complex near the Thai border, confiscating 30 Starlink terminals and detaining over 2,000 workers. The operation follows growing pressure from China and Thailand to crack down on transnational scam syndicates targeting Chinese nationals. However, satellite imagery and local reports suggest scam operations continue, raising doubts about the junta’s motives and the raid’s authenticity.
Analyst Comments: With the U.S., China, and Thailand all increasing scrutiny on borderland scam networks, Myanmar’s junta appears to be staging partial enforcement—possibly with tacit agreements from militia allies—to maintain foreign relationships while retaining local power structures. Starlink’s presence is particularly concerning: with no license in Myanmar, hundreds of terminals have reportedly been smuggled in to support isolated, illicit operations. This raises questions about satellite internet’s role in enabling closed-network cybercrime across conflict zones. Starlink and other LEO providers will likely face mounting pressure to enforce geographic controls and user vetting in high-risk regions.
READ THE STORY: The Diplomat
Items of interest
AWS Outage Becomes a Cyber Training Ground for China, Warns Former NSA Chief
Bottom Line Up Front (BLUF): Monday’s widespread AWS outage—triggered by a database issue—crippled digital services worldwide and is now being studied by nation-state adversaries, particularly China, as a blueprint for future cyber sabotage. Admiral Mike Rogers, former head of U.S. Cyber Command and the NSA, warned in an interview with The Sydney Morning Herald that such events expose “single points of failure” and create a playbook for how to replicate or escalate digital disruption at scale.
Analyst Comments: This wasn’t just a tech glitch but a global stress test. And adversaries were watching closely. When a single cloud provider incident brings down banking apps, smart devices, and core communications globally, it validates concerns about infrastructure monoculture. China’s cyber forces are likely dissecting this failure to identify exploitable dependencies in Western networks. The real danger isn’t the outage—it’s what comes next: hostile replication, supply chain poisoning, or systemic takedowns during future geopolitical flashpoints. Rogers’ point about adversaries using AI more aggressively than defenders should hit hard. We’re in a race for autonomous cyber dominance, and the lead may be slipping.
READ THE STORY: SMH
“Trust, Not Permissions, Will Define Cyber Security” — Samir Saran on the Future of Digital Safety (Video)
FROM THE MEDIA: Some 71% of respondents to the World Economic Forum’s Global Cybersecurity Outlook report an increase in cyber risks driven by geopolitical tensions, supply chain complexity, rapid AI deployment and other factors.
What Is Battle Damage Assessment (BDA) And How Is It Performed? - Tactical Warfare Experts (Video)
FROM THE MEDIA: What Is Battle Damage Assessment (BDA) And How Is It Performed? This informative video will take a closer look at Battle Damage Assessment (BDA) and its significance in military operations. BDA plays a vital role in determining the effectiveness of military strikes by evaluating the damage inflicted on enemy targets. Understanding how this assessment is conducted can provide valuable context for military strategies and decision-making processes.
The selected stories cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not endorse any third-party claims made in its original material or related links on its sites; the opinions expressed by third parties are theirs alone. For further questions, please contact InfoDom Securities at dominanceinformation@gmail.com.