Daily Drop (1158)
10-17-25
Friday, Oct 17, 2025 // (IG): BB // GITHUB // SN R&D
Claude Gets Agent Skills: Anthropic Enables Custom Task Modules for Enterprise AI
Bottom Line Up Front (BLUF): Anthropic has released Agent Skills for its Claude AI model—modular, programmable task-specific capabilities that users can add to extend Claude’s functionality. Skills allow Claude to interact with external tools, perform domain-specific tasks (e.g., filling PDFs, managing spreadsheets), and execute code in a secure, filesystem-based virtual environment. Enterprise customers can now create, manage, and deploy custom Skills across Claude.ai, the Claude API, and Claude Code—effectively giving Claude persistent, on-demand memory and “function calling”-like capabilities with security guardrails.
Analyst Comments: This is Anthropic’s answer to OpenAI’s “tools” and “function calling”—but more Unix-flavored. The filesystem-based design with progressive disclosure is clever, limiting token bloat by loading instructions only when needed. That efficiency comes at a price: real file execution, which means real attack surface. Giving Claude access to bash is a double-edged sword. A malformed or malicious Skill could leak data, alter files, or execute logic with unintended consequences. Please think of this as installing a shell script from GitHub into a production container every time Claude triggers it. Organizations should treat Skills like software deployments: review, test, and sandbox. And no, your AI doesn’t need sudo.
READ THE STORY: The Register
Trump Floats Tomahawk Sales to Ukraine — Longer Reach, Higher Stakes
Bottom Line Up Front (BLUF): President Trump has proposed supplying Ukraine with U.S.-made Tomahawk cruise missiles. If delivered, Tomahawks would give Kyiv a much longer-range, precision-strike option (conventional warheads, likely range ~1,600 km) that could hit strategic Russian military and energy infrastructure previously out of reach. The capability is tactically valuable but limited by likely small initial quantities, launcher constraints, and significant escalation risks — including Moscow’s political, military, and nuclear rhetoric responses. Washington will tightly control any transfer and, therefore, as much a political signal as a military capability.
Analyst Comments: Tomahawks would give Ukraine a potent precision-strike capability at deeper ranges — strategically advantageous but not a silver bullet. The value gained depends on quantity, targeting discipline, launcher availability, and integrated ISR. The transfer is as much a political lever as a military one; manage it with tight rules of engagement, clear escalation management plans, and realistic expectations about operational impact and Russian response.
READ THE STORY: FT
Silk Lure Espionage Campaign Targets Chinese FinTech Firms with Malicious Resume LNKs Delivering ValleyRAT
Bottom Line Up Front (BLUF): Seqrite Threat Labs has uncovered “Operation Silk Lure,” a targeted cyber espionage campaign aimed at Chinese fintech and cryptocurrency companies. Threat actors impersonated job seekers and sent malicious LNK shortcut files disguised as resumes to HR and technical recruiting teams. These LNK files triggered multi-stage payloads that culminated in the deployment of the ValleyRAT remote access trojan. The attack employed scheduled tasks for persistence, DLL injection, and anti-analysis techniques, and is suspected to be linked to East Asian espionage groups.
Analyst Comments: This is not generic phishing—it’s precision-engineered social engineering tailored to a specific region and industry. Complete with fabricated academic and work history, the Chinese-language resume was crafted to bypass initial HR screening. While the LNK + PowerShell + DLL combo is well-known, it remains effective due to user habits and endpoint visibility gaps. Notably, ValleyRAT has been updated to uninstall Chinese AV products like 360 Total Security and Huorong, indicating regional targeting. This campaign blurs the line between cybercrime and state-aligned APT operations in tactics and infrastructure.
READ THE STORY: Freebuf
North Korean Hackers Weaponize Blockchain to Evade Detection, Steal Crypto in EtherHiding Campaign
Bottom Line Up Front (BLUF): New research from Cisco Talos and Google’s Threat Intelligence Group reveals that North Korean threat actor UNC5342 is deploying EtherHiding, a technique that embeds malware in public blockchains, enabling decentralized, resilient command-and-control (C2) infrastructure. Paired with evasive malware strains like BeaverTail, OtterCookie, JADESNOW, and INVISIBLEFERRET, these campaigns target developers and cryptocurrency platforms through fake job offers. The combination of blockchain-based C2 and multi-stage malware represents a significant evolution in DPRK’s tradecraft—blending cybercrime and espionage with a persistent, low-cost infrastructure immune to takedown.
Analyst Comments: This is state-sponsored malware with startup-grade innovation. North Korea has effectively created next-gen bulletproof hosting by hijacking the blockchain’s immutability and decentralization. The EtherHiding technique uses read-only blockchain queries to pull payloads—leaving no transaction trace, avoiding gas fees, and bypassing traditional network detection.
READ THE STORY: CS // GBhackers
LinkPro Rootkit Uses eBPF to Evade Detection on Linux: Persistent, Fileless Backdoor Targets Cloud Workloads
Bottom Line Up Front (BLUF): Researchers from Synacktiv have uncovered LinkPro, a highly advanced Linux rootkit that leverages eBPF to stealthily establish backdoor access and hide malicious activity on cloud workloads. The intrusion began via a vulnerable Jenkins server (CVE-2024-23897) and targeted Amazon EKS environments using malicious Docker containers. LinkPro uses a dual-layer stealth strategy: eBPF-based syscall hijacking and fallback userland hooks via ld.so.preload. It supports magic packet activation, port redirection, and multiple communication protocols, making it nearly invisible to standard tools.
Analyst Comments: LinkPro was deployed in containerized cloud environments, specifically Kubernetes (EKS), which raises red flags for any org running Linux workloads in production. The rootkit uses eBPF to hook low-level syscalls (like getdents, kill, readdir), showing deep familiarity with kernel internals. Its ability to hide not only files and processes, but also its own eBPF programs, severely undermines traditional forensics tools, including bpftool. When eBPF-based hiding fails, it gracefully shifts to modifying ld.so.preload and injecting a shared library (libld.so) to hook libc functions—an elegant multi-stage evasion chain.
READ THE STORY: GBhackers
Zero-Click NTLM Credential Leak Resurfaces: CVE-2025-50154 Bypasses LNK Patch to Deliver Hashes Silently
Bottom Line Up Front (BLUF): Cymulate Labs has disclosed a new zero-click vulnerability, CVE-2025-50154, that bypasses Microsoft’s patch for CVE-2025-24054 and enables NTLM hash leaks via specially crafted .LNK files. Even fully patched systems remain vulnerable. Attackers can extract NTLM hashes without user interaction, opening the door to relay attacks, privilege escalation, and lateral movement in Windows environments.
Analyst Comments: NTLM strikes again—this time, without a single user click. Microsoft’s April patch aimed to block UNC path-based icon loading, but researchers found it didn’t go far enough. By tweaking .LNK files to embed a remote binary (rather than just an icon path), attackers can still force explorer.exe to fetch the binary and trigger NTLM authentication. The hash is sent out—silently. While this doesn’t execute the payload immediately, it plants a foothold for credential cracking or stealth delivery of malicious binaries. Security teams relying solely on Microsoft’s patch are likely exposed. This reinforces the need for layered defense, outbound traffic controls, and stricter .LNK handling policies.
READ THE STORY: Freebuf
Scattered LAPSUS$ Hunters Dox Hundreds of U.S. Federal Agents in Mass Leak
Bottom Line Up Front (BLUF): A loosely organized hacker collective calling itself Scattered LAPSUS$ Hunters has leaked the personal information of hundreds of U.S. government officials across DHS, ICE, FBI, and DOJ. The data, posted on Telegram, includes home addresses, phone numbers, and email credentials—posing immediate risks of physical threats, harassment, and social engineering. The group claims cartel-related motivations and has referenced bounties offered for doxing agents. The data source remains unclear, but the leak marks one of the most significant direct exposure events targeting U.S. domestic security agencies since 2016.
Analyst Comments: Names, phone numbers, and residential addresses were posted—information that, when weaponized, creates both physical and digital risk vectors for U.S. federal personnel. It also indicates a growing trend: decentralized threat actor communities like the Com blending gaming culture, cybercrime, and harassment into fluid, loosely accountable attack groups. While the group’s Telegram rhetoric is chaotic (“Where’s my 1M?” “Mexico pay me”), the impact is profound. The potential for abuse extends beyond harassment: these details can be used for phishing, SIM swapping, identity theft, or to facilitate physical intimidation, especially in the context of politically sensitive enforcement roles (e.g., ICE and DHS operations under the Trump administration).
READ THE STORY: 404
Spring Flaws Expose Secrets and Break WebSocket CSRF Protections (CVE-2025-41253 / CVE-2025-41254)
Bottom Line Up Front (BLUF): VMware Tanzu’s Spring team has released patches for two critical vulnerabilities affecting Spring Cloud Gateway and the Spring Framework. The first (CVE-2025-41253) allows remote attackers to abuse exposed actuator endpoints and SpEL injection to leak sensitive environment data. The second (CVE-2025-41254) enables CSRF bypasses in WebSocket-based STOMP messaging, allowing unauthorized message injection in real-time applications.
Analyst Comments: CVE-2025-41253 effectively turns misconfigured actuator endpoints into data exfiltration interfaces, especially in cloud-native apps relying on Spring Cloud Gateway. If SpEL expressions are exposed to untrusted input, attackers can dump API keys, tokens, or database credentials without breaching the app’s core logic.
READ THE STORY: Freebuf
Chinese APT ‘Jewelbug’ Quietly Compromised Russian IT Firm Using Living-off-the-Land Tactics
Bottom Line Up Front (BLUF): Symantec researchers have attributed a stealthy five-month intrusion into a Russian IT service provider to Jewelbug—a Chinese state-aligned APT also tracked as Earth Alux, CL-STA-0049, and REF7707. The attackers exploited a renamed version of Microsoft’s Console Debugger to execute shellcode and deploy payloads while maintaining persistent access via scheduled tasks and credential dumping. The group also deleted Windows event logs and abused Microsoft Graph API for stealth and lateral movement. This marks a rare Chinese intrusion into a Russian target and reflects Jewelbug’s broader pattern of targeting governments and IT firms in APAC and Latin America.
Analyst Comments: Chinese APTs continue to evolve beyond malware-heavy campaigns, leaning into LotL, cloud service abuse, and stealth persistence. Jewelbug’s tactics align with this evolution, emphasizing stealth and modularity. Organizations—especially IT service providers and government entities—should review telemetry for renamed or misused native tools, audit use of Graph API, and monitor for anomalous scheduled task creation or event log manipulation. This campaign also reinforces the reality that nation-state espionage ignores political alliances when intelligence priorities dictate.
READ THE STORY: SC MEDIA
F5 Breach Exposes Source Code: Company Releases 44 Patches to Address Post-Intrusion Vulnerabilities
Bottom Line Up Front (BLUF): F5 Networks confirmed a targeted breach by a state-sponsored actor in August 2025 that resulted in the theft of BIG-IP source code and internal vulnerability data. While there is no sign of software supply chain tampering, the incident raises concern over undisclosed zero-days in adversary hands. In response, F5 released patches for 44 CVEs across BIG-IP, F5OS, APM, and Kubernetes Next platforms, including critical SCP/SFTP vulnerabilities (CVE-2025-53868, CVE-2025-61955) with CVSS scores up to 8.7.
Analyst Comments: The patch dump isn’t your usual quarterly cleanup — it’s an emergency overhaul covering vulnerabilities likely known to the attackers. While there’s no public indication of widespread exploitation (yet), that window is shrinking. Enterprises running BIG-IP or F5OS, especially in government, telecom, or cloud infrastructure, should treat this as a post-compromise hardening event.
READ THE STORY: Freebuf
Items of interest
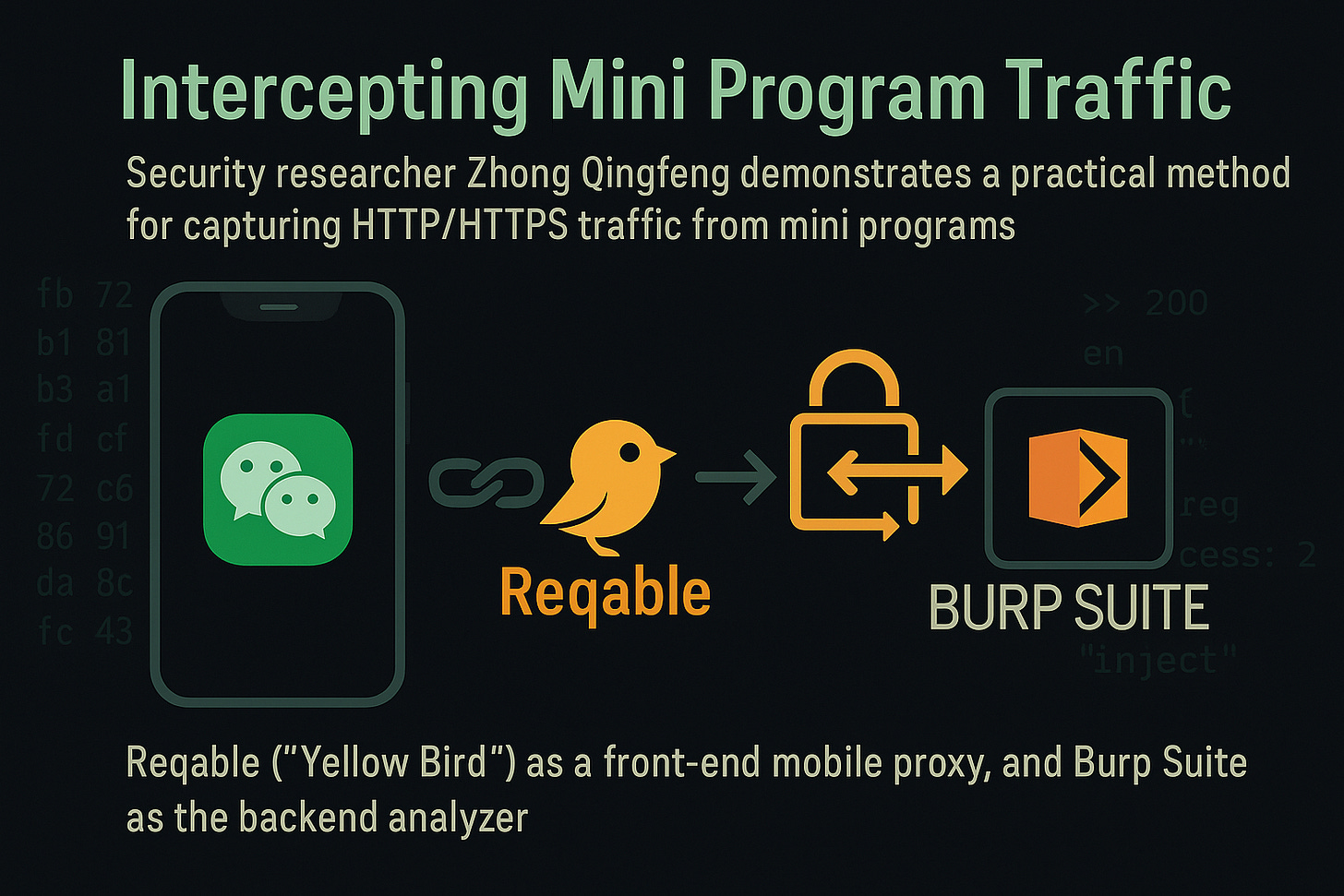
Intercepting Mini Program Traffic with Burp Suite + Reqable (a.k.a. “Yellow Bird”)
Bottom Line Up Front (BLUF): Security researcher Zhong Qingfeng demonstrates a practical method for capturing HTTP/HTTPS traffic from mini programs (e.g., WeChat mini apps) using a chained proxy setup: Reqable (“Yellow Bird”) as a front-end mobile proxy, and Burp Suite as the backend analyzer. This configuration enables complete visibility into mini program API calls, even over TLS, by routing traffic through a trusted certificate chain and reverse proxy. The technique is highly effective for mobile security testing and reverse engineering.
Analyst Comments: Capturing encrypted mini program traffic is difficult due to certificate pinning, app sandboxing, and platform-specific restrictions. This guide shows how tools like Reqable can bridge that gap by acting as a trusted middle layer, intercepting mobile traffic and passing it to Burp Suite for analysis. The technique doesn’t require rooting or jailbreaking, making it safer and more accessible for authorized testing. It’s especially valuable for appsec teams, bug bounty hunters, or red teamers targeting mobile or hybrid app backends. While the approach doesn’t bypass all advanced protections (like certificate pinning in native apps), it’s an essential method in any mobile pentester’s toolkit.
READ THE STORY: Freebuf
How to Capture React Native API Requests with Reqable | Emulator Root + Network Sniffing (Video)
FROM THE MEDIA: In this step-by-step tutorial, learn how to capture API/network requests from a React Native app using Reqable on a rooted Android emulator.
Intercepting Android requests using Burp Suite (Video)
FROM THE MEDIA: Py Guru demonstrates a simple, step-by-step method to intercept an Android device’s browser requests in Burp by (1) enabling a Burp proxy listener on your PC, (2) pointing the Android Wi-Fi proxy to that PC: port, and (3) exporting + installing Burp’s CA certificate on the Android device so HTTPS traffic can be decrypted.
The selected stories cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not endorse any third-party claims made in its original material or related links on its sites; the opinions expressed by third parties are theirs alone. For further questions, please contact InfoDom Securities at dominanceinformation@gmail.com.