Daily Drop (1157)
10-16-25
Thursday, Oct 16, 2025 // (IG): BB // GITHUB // SN R&D
US Scales Back InfoOps Defenses as AI Supercharges Global Influence Warfare
Bottom Line Up Front (BLUF): The U.S. has downsized key government units responsible for countering foreign influence operations—even as AI-driven disinformation campaigns from adversaries like China, Russia, and Iran escalate. The Foreign Malign Influence Center (FMIC) and parts of the FBI’s Foreign Influence Task Force have been reduced or reorganized under the Trump administration’s directive to prevent perceived “censorship” of domestic speech. In their place, private-sector actors and unconventional influence operations are now filling the gap.
Analyst Comments: Disinformation is no longer just propaganda—it’s now AI-optimized psychological warfare, amplified through deepfake videos, impersonation bots, and micro-targeted influence. While adversaries scale up, the U.S. is pulling back. Shuttering or restructuring agencies like FMIC and cutting CISA’s budget weakens coordination just as midterms (2026) and the 2028 presidential race loom. Claims of politicization may have merit—but gutting institutional capability leaves a vacuum that Russia, China, and Iran are actively exploiting. The future of information warfare isn’t about broadcasting ideology—it’s about seeding confusion, mimicking trusted voices, and eroding civic cohesion. Without a well-funded, multi-sector response, the U.S. risks being outmaneuvered in its information domain.
READ THE STORY: NextGov
Ukrainian Cyber Unit Hits Russian ISP, Leaks Data, Disrupts Operations in Strategic Uranium City
Bottom Line Up Front (BLUF): Ukraine’s military intelligence (HUR) claims responsibility for a June 12 cyberattack that caused ₽66 million (~$800,000) in damages to Orion Telecom, a major Siberian internet provider. The attack disrupted service—including in a closed city tied to uranium extraction—and led to a leak of customer data, prompting Orion to file a criminal complaint in Russia. The ISP was reportedly used by Russian security services to support war-related operations.
Analyst Comments: Timed to Russia Day, this operation marks one of the most financially and operationally impactful cyberattacks attributed to Ukrainian intelligence. While the ₽66M figure is notable, the real strategic value lies in disrupting telecom infrastructure critical to Russia’s military-industrial complex, especially in restricted zones. Orion Telecom’s sole internet provider in a uranium facility zone adds geopolitical weight. If accurate, this signals a surgical strike on infrastructure supporting nuclear or defense operations, not a random DDoS stunt. The data leak and resulting legal liability compound the damage, highlighting how modern cyber warfare isn’t just about system disruption but also eroding trust in national infrastructure providers.
READ THE STORY: The Kyiv Independent
Chinese State Hackers Infiltrated UK Classified Networks for Over a Decade
Bottom Line Up Front (BLUF): Chinese state actors maintained persistent, unauthorized access to classified UK government systems for more than ten years, according to multiple former and current British officials. The intrusions allowed access to “official-sensitive” and “secret” level material—including policy documents, diplomatic cables, and private communications—but did not compromise “top secret” information, according to government sources. A London data center tied to the Chinese government was also cited as a security risk.
Analyst Comments: While officials stress that “top secret” data was untouched, the breach of “secret” material (which includes military plans, sensitive diplomatic traffic, and crime investigations) is far from benign. The revelation that a data center for storing government data was sold to a Chinese-linked entity underlines how deeply economic decisions can intersect with national security. The UK’s reluctance to officially name China as a national security threat—until now—likely contributed to the lack of formal deterrence or a unified defense posture. The broader concern is that this wasn’t an isolated breach, but long-term access to systems believed to be secure. That suggests segmentation, monitoring, and incident response maturity weaknesses across Whitehall networks. Any organization with legacy government contracts, shared infrastructure, or transnational diplomatic roles should consider this a supply chain risk multiplier.
READ THE STORY: Bloomberg
Zimbabwe and Russia Sign Cybersecurity Pact Focused on Training, Infrastructure, and Strategic Alignment
Bottom Line Up Front (BLUF): Zimbabwe has signed a cybersecurity Memorandum of Understanding (MoU) with a Russian-led consortium under the “CyberZIM” initiative. The agreement includes infrastructure investment, cyber skills training for Zimbabwean youth, and long-term collaboration on defensive capabilities. It was signed during the National Cyber Security Expo and Conference in Harare and reflects a deepening of tech-aligned geopolitical ties between Zimbabwe and Russia.
Analyst Comments: This MoU isn’t just a workforce development deal—it’s a strategic partnership that ties Zimbabwe’s cyber future to Russian technical and political influence. While the emphasis is on training and job creation, the real significance lies in infrastructure sharing and long-term digital alignment, especially as Russia seeks to build influence across Africa amid growing isolation from the West. CyberZIM’s focus on building local infrastructure, transferring skills, and promoting AI security awareness suggests an ambition beyond national defense—it’s about positioning Zimbabwe as a regional cybersecurity hub, with Russian backing. The inclusion of firms like Komi and CyberProse underscores that this is a state-aligned export of Russian cybersecurity doctrine, not just private sector engagement.
READ THE STORY: Herald
Windows Remote Access Connection Manager 0-Day Vulnerability Disclosed, Already Exploited in Attacks
Bottom Line Up Front (BLUF): A critical local privilege escalation vulnerability (CVE-2025-59230) in Windows’ Remote Access Connection Manager (RasMan) is being actively exploited in the wild. The flaw allows low-privileged users to gain SYSTEM-level access by manipulating insecure service permissions. Microsoft has issued a patch, and CISA has added the bug to its Known Exploited Vulnerabilities catalog. Immediate remediation is advised, particularly for enterprise environments.
Analyst Comments: RasMan, responsible for handling VPN and dial-up connections, runs with elevated privileges and has a long history of patch cycles. But attackers had already used the bug this time before a PoC was public. The vulnerability’s appeal lies in its simplicity: manipulate file permissions or inject code into RasMan’s process space, and you’re running as SYSTEM. That’s game over in most endpoint defense scenarios.
READ THE STORY: Freebuf
Windows Agere Modem Driver 0-Day Exploited in Active Privilege Escalation Attacks
Bottom Line Up Front (BLUF): Two zero-day vulnerabilities in the legacy Agere Modem driver (ltmdm64.sys)—CVE-2025-24052 and CVE-2025-24990—are being actively exploited for local privilege escalation (LPE) on Windows systems. Microsoft’s October 2025 update removes the vulnerable driver, effectively disabling fax modem hardware dependent on it. Proof-of-concept (PoC) code for one vulnerability is already public, accelerating the threat window for exploitation.
Analyst Comments: Tracked as CVE-2025-24052 and CVE-2025-24990, both vulnerabilities affect the Agere Modem driver (ltmdm64.sys). The first is a stack-based buffer overflow that can be exploited locally for kernel-mode code execution; the second is an untrusted pointer dereference. Both carry a CVSS score of 7.8 and require no user interaction. Microsoft’s patch removes the driver entirely, disabling any dependent fax hardware. The PoC exploit for CVE-2025-24052 is already public, increasing the risk of rapid weaponization in post-exploitation toolkits. Organizations using fax hardware in regulated environments face service interruptions unless they migrate to supported solutions. Microsoft urges admins to audit systems, remove dependencies, and disable modem functionality via Group Policy or endpoint controls.
READ THE STORY: GBhackers
CVE-2025-32463: Sudo Chroot Vulnerability Enables Local Privilege Escalation to Root
Bottom Line Up Front (BLUF): A critical vulnerability in the Sudo utility (versions 1.9.14 to 1.9.17) allows local attackers to escalate privileges to root via the --chroot option. Tracked as CVE-2025-32463 with a CVSS score of 9.3, the bug affects major Linux distributions and is being actively discussed with a working proof-of-concept (PoC) exploit now publicly available. All users and administrators should patch to Sudo 1.9.17p1 or later immediately.
Analyst Comments: The vulnerability lies in how sudo parses and handles chrooted paths, allowing an attacker to control shared library resolution via a crafted nsswitch.conf file and load arbitrary code as root. The risk is amplified in environments that rely on chrooted automation (e.g., containers, CI/CD pipelines, or development sandboxes) where users already have some local access. This isn’t just a theoretical problem: the PoC requires no special permissions, and once the exploit is run, the attacker gains a root shell.
READ THE STORY: Freebuf
Pixnapping Attack Bypasses Android Security to Steal 2FA Codes in Under 30 Seconds
Bottom Line Up Front (BLUF): Researchers have disclosed a critical Android side-channel vulnerability named Pixnapping that can extract sensitive screen content—including Google Authenticator 2FA codes—in as little as 30 seconds, without root or special permissions. The attack leverages GPU compression timing differences and Android’s UI overlay system to steal data from nearly all modern Android devices, including Pixel 6–9 and Galaxy S25. Google has assigned CVE-2025-48561, which is rated high severity.
Analyst Comments: Pixnapping is a deep cut into Android’s graphics stack—both clever and dangerous. Unlike traditional malware, this technique uses legitimate system behaviors to spy on screen content through semi-transparent overlays and GPU timing quirks—no screen capture permissions. No rooting. Just precision abuse of how Android renders pixels using SurfaceFlinger and GPU.zip compression. The implications are profound: OTP codes, Signal messages, transaction data, and even location history are now fair game for malicious apps. The researchers showed how malicious apps can infer pixel data by measuring subtle render-time changes in VSync callbacks—an indirect but effective side-channel.
READ THE STORY: Freebuf
Chongqing University | MDADroid: A Novel Malware Detection Approach by Building Functionality-API Mapping
Bottom Line Up Front (BLUF): Researchers at Chongqing University have introduced MDADroid. This novel Android malware detection method maps application behavior at the function level instead of relying solely on API calls. By creating a functionality-to-API mapping and using a heterogeneous graph-based learning model, MDADroid achieves high detection accuracy (up to 99.56%) while maintaining low resource consumption and strong resistance to Android API evolution—an issue causes traditional detection models to degrade over time.
Analyst Comments: MDADroid’s pipeline starts with constructing a curated, up-to-date set of permission-related APIs by combining Android documentation with historical tools like PScout and Axplorer. To handle evolving API versions, it uses ASCM, a dual-layer similarity check that leverages structural matching and semantic embeddings (via BERT) to map deprecated APIs to their AndroidX equivalents.
READ THE STORY: Freebuf
VS Code Extensions Leak Hundreds of Secrets, Raising Supply Chain Attack Risk
Bottom Line Up Front (BLUF): Security researchers at Wiz uncovered over 550 valid secrets embedded in public VS Code and Open VSX extensions—many tied to AI platforms, cloud providers, and databases. Over 100 of these secrets could’ve allowed attackers to push malicious updates, creating a high-risk supply chain threat. Microsoft has since implemented automated secret-scanning on its Visual Studio Marketplace to block vulnerable extensions.
Analyst Comments: Secrets like GitHub PATs, AWS tokens, GCP keys, and even AI platform credentials were found hardcoded into extension repos. With auto-update enabled by default, a compromised extension could silently deploy malware across thousands of developer environments. Worse, over 150,000 users could have been hit in one shot had these flaws been exploited. That’s not just theoretical—it’s near catastrophic when you consider how many developers unknowingly integrate extensions into CI/CD pipelines. The bigger problem: this reflects a systemic issue across software ecosystems. Developers are increasingly integrating third-party tools and AI features in a “vibe coding” rush—copy-pasting from ChatGPT, moving fast, and skipping security hygiene.
READ THE STORY: The Register
Multiple Vulnerabilities Disclosed in XXL-JOB: RCE, Default Credentials, and Deserialization Risks Expose Task Scheduler
Bottom Line Up Front (BLUF): Security researchers have compiled multiple reproducible vulnerabilities in XXL-JOB, a widely adopted distributed task scheduling platform. Issues include weak default credentials, unauthenticated API access, arbitrary command execution, insecure deserialization, and access token misuse. Most of these flaws are easily exploitable and could lead to complete system compromise, particularly in environments running outdated versions or default configurations.
Analyst Comments: XXL-JOB’s convenience and low barrier to entry have made it a go-to for backend task scheduling, but accessibility also introduces serious risks when security best practices are ignored. The findings here aren’t theoretical: these are practical, weaponizable flaws with working proof-of-concept code, and several require no authentication. Systems with default admin/123456 logins or unchanged accessToken values are trivially compromised.
READ THE STORY: Freebuf
Economist Roundtable: Boom or Bubble? AI, Tariffs, and the Real State of the U.S. Economy
Bottom Line Up Front (BLUF): The Economist’s editorial leadership convened a panel discussion to dissect the apparent strength of the U.S. economy under restrictive Trump-era trade and immigration policies. While GDP growth continues, much of it is attributed to AI-driven investment enthusiasm, raising questions about economic sustainability versus speculative exuberance. The panel stops short of calling it a bubble—but warns that structural risks and overhyped AI expectations could trigger a reckoning.
Analyst Comments: Zanny Minton Beddoes and Edward Carr led the panel through a sharp look at why America’s economy is outperforming expectations, despite policies that traditionally hinder labor mobility and global trade flows. The underlying driver? You guessed it: AI euphoria—from Wall Street to Silicon Valley. That enthusiasm is pushing corporate valuations and infrastructure investment into uncharted territory. The roundtable compares to the dot-com era, noting parallels in valuation inflation and debt-fueled expansion. The key takeaway isn’t that a crash is imminent, but that current growth masks vulnerabilities—including supply chain dependence, productivity gaps, and a narrow set of sectors (namely tech and defense) pulling ahead. It’s not all smoke—but it’s not all fireproof either.
READ THE STORY: The Economist
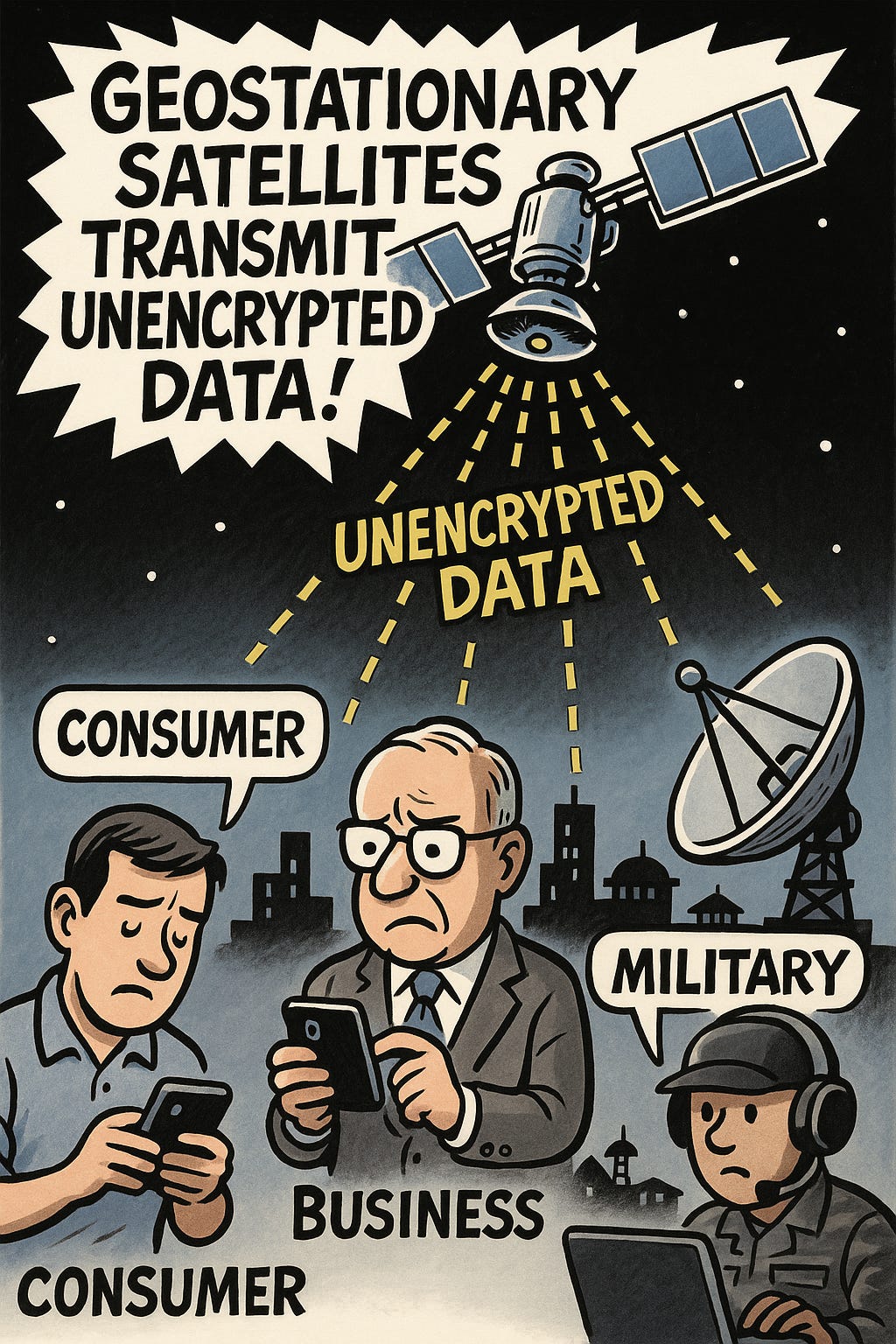
Nearly half of Geostationary satellites transmit unencrypted Data
Bottom Line Up Front (BLUF): A joint study by researchers at UC San Diego and the University of Maryland found that nearly 50% of geostationary satellites transmit unencrypted data, exposing sensitive communications, including in-flight Wi-Fi traffic, voice calls, text messages, and even military and infrastructure data. Using only an $800 satellite receiver, the team passively intercepted thousands of transmissions, highlighting a massive and largely ignored threat vector in satellite communications.
Analyst Comments: The fact that such a wide range of consumer, corporate, and military data is transmitted in plaintext—over satellite links covering 40% of the planet at once—is alarming. The accessibility of this data is even more concerning: the researchers didn’t need custom hardware or advanced hacking tools, just commercially available equipment and a clear line of sight. Satellite backhaul is often assumed to be inherently secure due to its complexity. That assumption is clearly false. Worse, the researchers found that major telecom operators—including T-Mobile, AT&T Mexico, and Telmex—routinely exposed unencrypted voice and data streams, with thousands of phone numbers and messages captured in hours: some even transmitted raw network data and decryption keys.
READ THE STORY: Freebuf
Chaining Path Traversals into RCE – Meta’s $111,750 Vulnerability
Bottom Line Up Front (BLUF): At Meta’s 2024 BountyCon, a researcher earned $111,750 for chaining a path traversal vulnerability in Facebook Messenger’s Windows client with DLL hijacking in third-party software to achieve remote code execution (RCE). The attack leveraged client-side weaknesses in Messenger’s handling of E2EE file attachments and exploited Windows’ DLL search behavior to execute attacker-controlled code without user interaction.
Analyst Comments: The Messenger client improperly validated attachment file names in end-to-end encrypted (E2EE) chats, allowing an attacker to write arbitrary files to unintended locations on a victim’s machine. However, the real breakthrough was understanding the Windows environment and targeting a nonexistent but expected DLL (qwave.dll) in Viber’s local folder. With precise traversal and a carefully crafted payload, the researcher landed a malicious DLL exactly where Viber would later load it—triggering execution under the victim’s context.
READ THE STORY: Freebuf
BlackSuit Ransomware Hits Manufacturer After Voice Phishing and VPN Credential Theft
Bottom Line Up Front (BLUF): A large manufacturing firm suffered a major ransomware attack after an employee fell for a voice phishing scam, leading to the theft of a single VPN credential. The attackers, identified as the Ignoble Scorpius group, gained network access, escalated privileges, exfiltrated 400 GB of data, and encrypted hundreds of ESXi-hosted virtual machines using BlackSuit ransomware. A $20 million ransom was demanded but not paid.
Analyst Comments: According to Unit 42’s post-incident analysis, the attackers began with a fake IT help desk call that tricked an employee into entering VPN credentials into a spoofed site. With network access, they quickly performed a DCSync attack to obtain domain admin credentials, mapped the network using Advanced IP Scanner, and deployed persistence via AnyDesk and a custom RAT configured as a scheduled task.
READ THE STORY: GBhackers
95% of ChatGPT Users Don’t Pay—And OpenAI Is Bleeding Billions
Bottom Line Up Front (BLUF): Despite ChatGPT dominating the generative AI market and driving about 70% of OpenAI’s revenue, only 5% of users are paying, according to The Financial Times. In the first half of 2025, OpenAI reportedly generated $4.3 billion in revenue but suffered a net loss of $13.5 billion, with over half attributed to convertible equity remeasurement. Meanwhile, the company is committing to over $1 trillion in compute infrastructure deals by 2030, fueled by circular investments from partners like Microsoft and Nvidia.
Analyst Comments: OpenAI’s dominance in AI usage doesn’t equal profitability—at least not yet. Its user base exceeds 800 million, but just 5% contribute to revenue through ChatGPT subscriptions ($20–$200/month tiers). That’s higher than the industry norm of 3% paying users, but it’s still a drop in free usage. The strategy appears to be: scale now, monetize later. But the scale comes with staggering infrastructure costs—$1T in upcoming datacenter commitments—and its finances increasingly resemble a tech bubble, propped up by GPU credits, equity swaps, and revenue projections that some investors openly question.
READ THE STORY: The Register
Microsoft, Nvidia, and Investors Drop $40B on Aligned Data Centers in AI Infrastructure Land Grab
Bottom Line Up Front (BLUF): A consortium including Microsoft, Nvidia, xAI, and BlackRock has agreed to acquire Aligned Data Centers for $40 billion, the largest datacenter buyout to date. The deal is the first investment under the AI Infrastructure Partnership (AIP) and marks a massive bet on scaling compute to meet generative AI demand. With plans to mobilize up to $100B in equity and debt, the move signals escalating capital commitment—and risk—across the AI supply chain.
Analyst Comments: The AIP consortium isn’t just buying datacenters; it’s buying leverage in the future of AI dominance. Aligned’s 5 GW portfolio is a big prize, especially in the North and South American markets, where power availability is becoming a bottleneck for AI scaling. But the underlying economics are sketchy. AI firms, including OpenAI and Microsoft, are entering massive long-term financial commitments without matching revenue. OpenAI is reportedly $13.5B in the red this year alone. Nvidia and AMD offer GPU credits like venture capital, while companies double down on datacenter real estate with borrowed capital and future revenue projections.
READ THE STORY: The Register
Items of interest
Trump Floats Cooking Oil Trade Ban with China Amid Soybean Spat
Bottom Line Up Front (BLUF): President Trump is threatening to cut trade ties with China over used cooking oil (UCO), calling Beijing’s soybean import cuts an “Economically Hostile Act.” But traders say the move is symbolic—U.S. imports of Chinese cooking oil have already dropped 65% this year due to tariffs and Chinese tax rebate cuts.
Analyst Comments: Trump claimed on social media that China’s soybean buying cuts hurt U.S. farmers and called used cooking oil “something we can easily produce ourselves.” However, according to Reuters, U.S. cooking oil imports from China dropped to 290,690 tons in Jan–Aug 2025, down from 1.27 million tons in 2024. Two Chinese traders said the U.S. market is no longer a focus, with most exports now going to Singapore and the EU. Analysts called Trump’s announcement “not escalatory,” with the UCO trade paling compared to the $12B soybean export market.
READ THE STORY: Reuters
Trump floats cooking oil ban over China’s soybean cut (Video)
FROM THE MEDIA: President Trump is threatening to block cooking oil imports from China after Beijing pulled back from buying US soybeans.
Why Soybeans & Cooking Oil Matter to U.S. (Video)
FROM THE MEDIA: China and U.S. trade tensions have continued into a 2nd straight week, with President Trump threatening a cooking oil embargo. Kevin Green joins Diane King Hall to make sense of the latest tensions taking shape, and what it means for market volatility in general. On the earnings front, KG sees some tailwinds for ASML (ASML), particularly for its smartphone and AI business segments.
The selected stories cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not endorse any third-party claims made in its original material or related links on its sites; the opinions expressed by third parties are theirs alone. For further questions, please contact InfoDom Securities at dominanceinformation@gmail.com.