Daily Drop (1137)
09-17-25
Wednesday, Sep 17, 2025 // (IG): BB // GITHUB // SN R&D
Projects:
News:
AI Coding Assistants Open New Attack Surface for Backdoor Injections via Prompt Manipulation
Bottom Line Up Front (BLUF): Threat actors exploit AI-powered code assistants like GitHub Copilot to inject backdoors and exfiltrate data through indirect prompt injections and credential abuse. These attacks manipulate context inputs or steal session tokens to bypass safeguards, enabling malicious code generation within developer environments.
Analyst Comments: As context-aware coding assistants become more autonomous, adversaries can exploit indirect prompts or hijack sessions to inject malware without user awareness. Expect increased targeting of LLM-powered developer tools as attackers refine their techniques. Mitigating this risk will require hardened development practices, secure API access, and heightened awareness among developers using AI tooling.
FROM THE MEDIA: These tools, which integrate into IDEs to provide code suggestions and completions, are being manipulated via indirect prompt injection—where malicious instructions are hidden in external context like public APIs or social media data. Sometimes, simply adding contaminated files or URLs can lead the assistant to insert malicious code automatically. Also, stolen credentials allow attackers to invoke models directly ("LLMJacking"), bypassing interface safeguards. One simulation showed an AI assistant embedding a backdoor that fetched commands from an attacker-controlled server, executed in the user’s environment. Researchers stress the importance of context validation, manual code review, and API monitoring as critical defenses.
READ THE STORY: GBhackers
CrowdStrike npm Packages Compromised in “Shai-Hulud” Supply Chain Attack
Bottom Line Up Front (BLUF): Several npm packages published under the CrowdStrike namespace were compromised in a new wave of the "Shai-Hulud" supply chain attack. The malicious code, embedded in bundle.js, exfiltrated secrets by executing TruffleHog and creating rogue GitHub Actions workflows. Affected versions have since been removed from the npm registry.
Analyst Comments: By repurposing legitimate tools like TruffleHog for credential harvesting, the attackers evaded basic detection while gaining deep access to developer environments and CI/CD pipelines. CrowdStrike’s swift response mitigated broader exposure, but the reuse of known attack techniques across packages suggests attackers are automating propagation. Organizations must treat third-party packages as untrusted by default and enforce dependency integrity checks, including lockfile audits and strict version pinning.
FROM THE MEDIA: The affected packages, including @crowdstrike/commitlint, @crowdstrike/falcon-shoelace, and @crowdstrike/foundry-js, contained a malicious bundle.js script. Upon installation, it downloaded and executed TruffleHog to scan for developer secrets and CI tokens, which were then exfiltrated to a hardcoded webhook endpoint. Additionally, the malware injected unauthorized GitHub Actions workflows to maintain persistence. The npm registry removed the malicious packages, and CrowdStrike confirmed the Falcon platform was unaffected. The company also rotated exposed keys and is collaborating with npm to conduct a full investigation.
READ THE STORY: GBhackers
Apple CVE-2025-43300 Exploited in Zero-Day Spyware Campaign Targeting Older Devices
Bottom Line Up Front (BLUF): Apple has patched CVE-2025-43300, a zero-day vulnerability in the ImageIO framework, after evidence emerged it was exploited in advanced surveillance operations. The fix was recently backported to older devices like the iPhone 8 and iPad Pro 1st Gen, weeks after being addressed on newer models.
Analyst Comments: The chaining of this Apple flaw with a WhatsApp bug (CVE-2025-55177) suggests coordinated exploitation across platforms. Civil society figures, including journalists and activists, appear to be among the targets, raising concerns about digital rights and state-sponsored monitoring. Expect increased scrutiny of OS-level image parsing vulnerabilities and vendor response timelines.
FROM THE MEDIA: Apple issued a security update backporting a patch for CVE-2025-43300—a critical out-of-bounds write vulnerability in the ImageIO framework—to older devices, including iPhone 8, iPhone X, and various iPads. The flaw, which allows memory corruption via a malicious image file, was patched on August 20 for newer Apple devices. Apple acknowledged that the issue "may have been exploited in an extremely sophisticated attack against specific targeted individuals." Meta also issued an alert in August, indicating that the bug may have been used alongside WhatsApp vulnerability CVE-2025-55177 in spyware attacks. Amnesty International's Security Lab is actively investigating cases involving civil society targets. Around the same time, Samsung patched a similar Android vulnerability (CVE-2025-21043), which was also exploited in the wild.
READ THE STORY: The Register
Global Cybersecurity Systems Struggle to Keep Pace with Expanding Digital Threats
Bottom Line Up Front (BLUF): Cyberattacks on healthcare, finance, energy, and government sectors are escalating worldwide, exposing outdated infrastructure and fragmented defenses. As the digital ecosystem becomes more interconnected, the global response remains slow and uneven, with significant legislation, enforcement, and institutional capacity gaps across regions like Latin America, Eastern Europe, and Asia.
Analyst Comments: Countries face distinct challenges: North America’s regulatory lag, Eastern Europe’s uneven enforcement of GDPR, and Latin America’s underinvestment in cyber defense. Meanwhile, threat actors—especially state-sponsored groups—adapt rapidly, targeting legacy systems and exploiting geopolitical instability. Without stronger international cooperation, shared threat intelligence, and unified policy standards, the global cyber landscape will continue to fragment, allowing attackers to exploit the weakest links across borders.
FROM THE MEDIA: From ransomware attacks on hospitals to GPS jamming and energy grid sabotage, the consequences of under-secured infrastructure are mounting. In North America, landmark breaches like the Colonial Pipeline incident revealed the vulnerabilities of outdated operational technologies. Though advanced in data protection via GDPR, Europe struggles with enforcement disparities between Western and Eastern member states. In the Middle East, cyber capabilities are growing in Gulf nations, while conflict zones remain digitally unstable. Latin America faces a cybercrime surge amidst low investment and skill shortages, and in Asia, China’s centralized controls contrast sharply with India’s fragmented approach. Torres Landa calls for a unified global cybersecurity strategy—bridging legal, technological, and institutional gaps to secure the future of the digital economy.
READ THE STORY: The Globalist
Japan to Subsidize NEC’s Subsea Cable Fleet to Counter Global Rivals, Boost National Security
Bottom Line Up Front (BLUF): Japan is set to subsidize NEC’s acquisition of subsea cable-laying vessels, aiming to enhance national security and close the gap with U.S., French, and Chinese rivals who already own their own fleets. The move reflects growing concerns over the vulnerability of global undersea communications infrastructure amid rising geopolitical tensions.
Analyst Comments: Subsea cables form the backbone of global internet and financial systems, and their strategic significance has drawn increasing attention from national security planners. Japan’s decision to support NEC’s fleet acquisition highlights a broader Indo-Pacific trend: militarizing and hardening digital infrastructure against sabotage, surveillance, and coercion. With China-linked attacks on cables in the Matsu Islands and the Baltic Sea as recent examples, sovereign control over cable-laying capacity is now seen as essential. Expect more countries to follow suit, particularly those reliant on foreign or leased infrastructure.
FROM THE MEDIA: NEC currently dominates cable installations in Asia and has laid over 400,000 km of fiber globally, but relies on leased ships, including one from a Norwegian group under a four-year contract. By contrast, major rivals such as SubCom (U.S.), Alcatel Submarine Networks (France), and HMN Tech (China) all operate their own cable fleets, giving them strategic autonomy. Japan’s support aims to bolster NEC’s ability to deploy armored, sabotage-resistant cables across the Indo-Pacific, aligning digital infrastructure with national defense priorities.
READ THE STORY: Submarine Telecoms Forum
Europe Urged to Adopt Subversive Strategy Against Russia Amid NATO Tensions
Bottom Line Up Front (BLUF): Amid renewed Russian drone incursions into NATO territory and a shifting U.S. stance under President Trump, European leaders are being called to reassess their Russia strategy. A Foreign Affairs article by Veronica Anghel and Sergey Radchenko argues that Europe must confront Moscow not only with military readiness but through economic pressure, elite defection incentives, and long-term post-Putin planning.
Analyst Comments: The proposal to subvert the Kremlin from within—by encouraging capital flight and elite defection—echoes Cold War-era playbooks but is reframed for the digital and economic landscape of the 2020s. Notably, the article suggests that sanctions alone are insufficient and that Europe must embrace calculated pragmatism, even considering channels of influence post-conflict. With signs of internal dissent in Russia and regional instability rising, the effectiveness of such a strategy may hinge on Europe’s ability to act independently and cohesively.
FROM THE MEDIA: They argue that Europe’s overreliance on U.S. support and diplomatic marginalization—especially under Trump’s unpredictable foreign policy—has left the continent strategically adrift. Despite robust sanctions and $200 billion in aid to Ukraine, the EU lacks consensus on Russia's long-term threat. The authors advocate for a sharper, more subversive approach: offering “exit ramps” to disaffected Russian elites, incentivizing skilled emigration, and using economic tools to destabilize Kremlin power networks. They also call for future-oriented planning, suggesting Europe must not only counter aggression now but prepare for post-conflict engagement with a transformed Russia.
READ THE STORY: Foreign Affairs
China Opens Antitrust Probe Into Nvidia Amid U.S. TikTok Negotiations
Bottom Line Up Front (BLUF): As the U.S. and China near a deal to keep TikTok operational in the U.S., Beijing has launched a surprise antitrust probe into Nvidia, signaling it intends to leverage American tech giants in future trade talks. The move comes amid ongoing U.S. export controls and high tariffs, with China pressing for wider concessions beyond the TikTok agreement.
Analyst Comments: While the probe may have limited commercial impact given Nvidia’s reduced dependency on China, the gesture carries symbolic weight: China wants to show it still holds cards in the tech standoff. This signals a shift from defensive posturing to active counter-leverage, particularly as Beijing seeks to pressure Washington on export controls targeting AI and semiconductor sectors. It also hints at a future where U.S.-China tech competition is entangled in a broader geopolitical chess match, with regulatory pressure becoming a recurring tactic.
FROM THE MEDIA: The move is widely seen as a power play to remind Washington of China’s regulatory influence over U.S. tech firms. While Nvidia has reduced its reliance on Chinese sales—from 20% of global revenue to 6%—Chinese industries still depend on Nvidia’s AI chips. Meanwhile, the TikTok deal is expected to involve a U.S. consortium (including Oracle) taking majority control of a new U.S. entity, with China open to licensing the core algorithm. Still, Beijing is pushing to remove export restrictions, which Washington has rebuffed.
READ THE STORY: WSJ
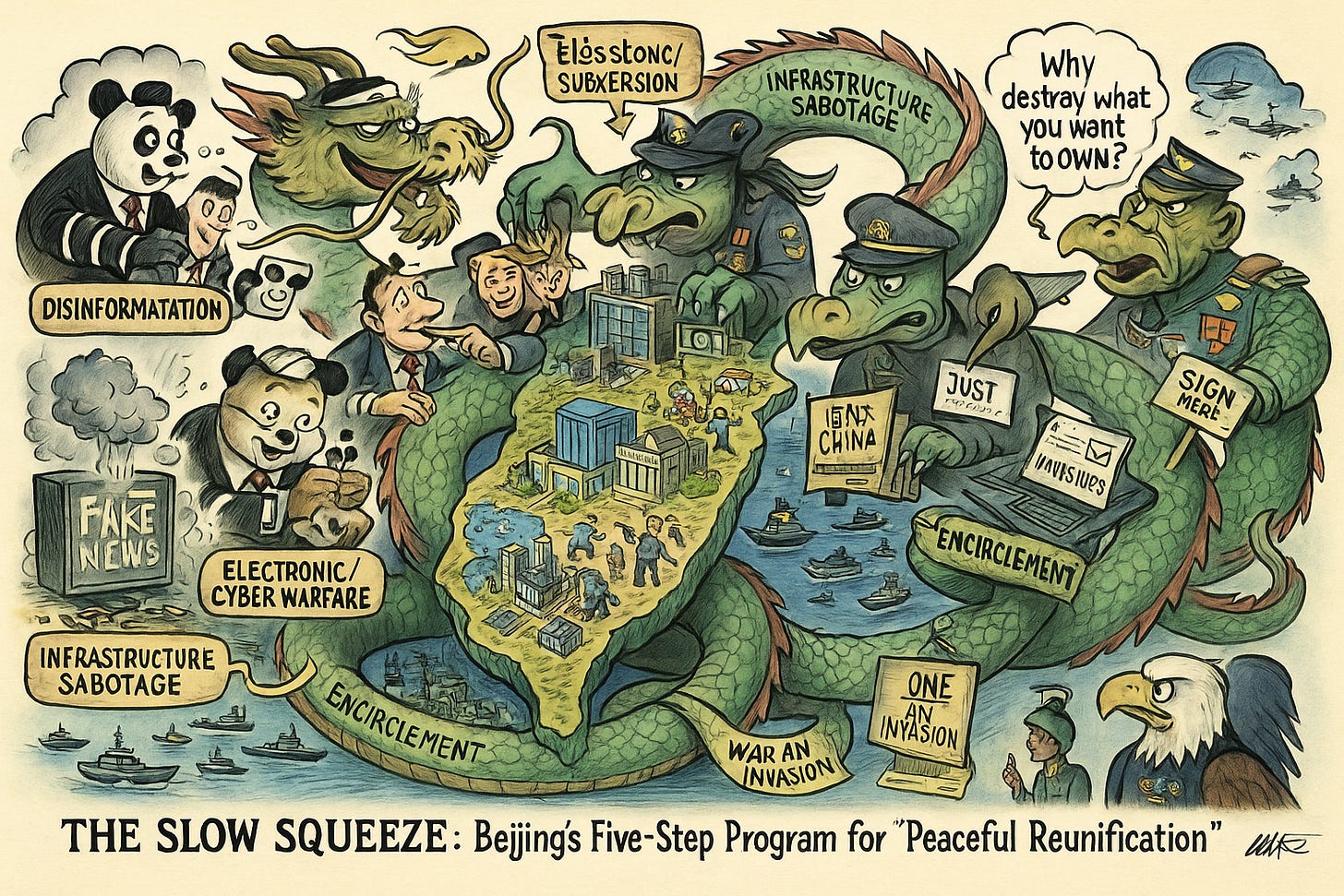
“War Without Harm”: China’s Five-Phase Hybrid Warfare Strategy to Subdue Taiwan
Bottom Line Up Front (BLUF): China is actively deploying a five-phase hybrid warfare strategy against Taiwan designed to achieve political subjugation without full-scale invasion or physical destruction. Through infrastructure sabotage, disinformation, electronic warfare, military encirclement, and political subversion, Beijing seeks to destabilize Taiwan while preserving its economic and strategic value.
Analyst Comments: The hybrid model enables plausible deniability, complicates international responses, and risks undermining Taiwan’s defense readiness before a single shot is fired. While Taiwan has taken steps to bolster resilience—from EW upgrades to counter-disinformation efforts—its lack of independent satellite infrastructure and internal vulnerability to subversion remain critical weaknesses. Expect further refinement of this approach in future PLA planning and cyber operations targeting other strategic democracies.
FROM THE MEDIA: China’s hybrid warfare playbook against Taiwan is built around a five-phase strategy aimed at subduing the island without direct military invasion. These phases include sabotage of undersea cables and critical infrastructure, as seen in the 2023 and 2025 attacks; cognitive warfare using AI-driven disinformation campaigns during Taiwan’s 2024 elections; escalation into electronic warfare through GPS and radar jamming; full-scale military encirclement mimicking a blockade; and activation of long-established subversion networks within Taiwan. Chinese institutions have cultivated ideological allies in Taiwan via scholarships, while the United Front Work Department has increased espionage efforts. The report warns that this "war without harm" model could enable China to seize control of Taiwan through systemic disruption and political collapse, not conventional war.
READ THE STORY: Geopolitical Monitor
Paraguay’s Pro-Israel and Pro-Taiwan Foreign Policy Rooted in Cold War Conservatism
Bottom Line Up Front (BLUF): Paraguay defies global trends by maintaining strong diplomatic support for Israel and Taiwan—stances rooted in Cold War-era alliances, anti-communist ideology, and domestic conservatism. President Santiago Peña has reaffirmed this alignment, linking the nation’s foreign policy to religious and ideological values, despite facing cyberattacks allegedly linked to these positions.
Analyst Comments: Its unwavering support for Israel and Taiwan aligns with a conservative political legacy and religious nationalism, rather than short-term economic or geopolitical calculus. As major powers court Latin America, Paraguay may leverage this principled alignment to attract investment from like-minded states—but risks increasing cyber and diplomatic pressure from adversaries. Expect Paraguay to remain a diplomatic outlier in the Global South as ideological loyalty continues to trump pragmatism.
FROM THE MEDIA: Paraguay is one of just 12 countries that maintain full diplomatic ties with Taiwan and has supported Israel in key international votes, including the recent UN resolution on Palestinian statehood. President Santiago Peña attributed recent cyberattacks on Paraguay to its pro-Israel and pro-Taiwan positions. These stances trace back to the Cold War, particularly under the long rule of dictator Alfredo Stroessner, who formed strong anti-communist alliances with both Israel and Taiwan. The article highlights Paraguay’s religious conservatism, historical political continuity through the Colorado Party, and ideological solidarity as key drivers of this enduring foreign policy direction.
READ THE STORY: LAR
Keep reading with a 7-day free trial
Subscribe to Bob’s Newsletter to keep reading this post and get 7 days of free access to the full post archives.