Daily Drop (1106)
08-09-25
Saturday, Aug 09, 2025 // (IG): BB // GITHUB // SN R&D
PROJECTS:
NEWS:
Ukraine Expands Cyber Offensive, Hitting Moscow–St. Petersburg Rail After Aeroflot Breach
Bottom Line Up Front (BLUF): Following last month’s cyberattack that disrupted Russian airline Aeroflot, Ukrainian-aligned hacktivists have crippled the Moscow–Tver suburban rail line, a key commuter route linking Moscow to St. Petersburg. The coordinated cyber campaign, which also includes drone strikes on railway infrastructure, is disrupting both civilian life and military logistics deep inside Russia. The attacks aim to bring the realities of war home to metropolitan Russians.
Analyst Comments: The targeting of transportation infrastructure in Russia’s heartland not only disrupts logistics but also has significant psychological value, eroding the perception of security among Russian civilians far from the front lines. The dual strikes on Aeroflot and the railway system in quick succession suggest a sustained campaign designed to stretch Russian incident response resources. If these operations persist, they could create long-term instability in Russia’s domestic mobility systems, complicating both economic activity and military resupply efforts.
FROM THE MEDIA: Ukrainian forces conducted a major drone strike against the Archeda railway station in Frolovo, Volgograd Oblast, sparking fires and delaying more than 220 trains since mid-July. Just days later, Ukrainian hacktivists — reportedly from groups including Silent Crow, Cyber Partisans, and Ukraine’s Center for Strategic Communications — launched a large-scale cyberattack against the Joint Stock Company Moscow-Tver Suburban Passenger Company. The intrusion shut down ticketing and validation systems, disabled cashier and dispatcher terminals, and knocked out servers and network equipment along the Moscow–Tver line. This route is critical for commuter traffic and links Moscow with St. Petersburg, Russia’s second-largest city and a key political center. The incident follows July’s Aeroflot breach, which temporarily grounded flights, and drew international attention to Ukraine’s expanding cyber warfare capabilities.
READ THE STORY: Daily Kos
PACER and CM/ECF Breach Exposes Sensitive U.S. Federal Court Data, Including Possible Informant Identities
Bottom Line Up Front (BLUF): A cyberattack on the U.S. federal judiciary’s PACER and CM/ECF systems has potentially compromised sealed court filings, including the identities of confidential informants. The Administrative Office of the U.S. Courts confirmed the intrusion, which is believed to have affected multiple federal district courts and may involve state-sponsored or organized cybercriminal actors. Officials are now accelerating plans to replace outdated infrastructure.
Analyst Comments: If informant identities, sealed indictments, or active warrant data are exposed, the impact could extend beyond privacy violations to obstructing criminal investigations and endangering lives. The targeting aligns with broader trends of adversaries seeking access to legal and law enforcement intelligence. Modernization efforts must prioritize encryption-at-rest, zero-trust access controls, and continuous monitoring — but these measures will require both congressional funding and operational disruption to implement.
FROM THE MEDIA: The incident is believed to have impacted multiple federal district courts since at least early July. The compromised data could include non-public indictments, search warrants, and other sensitive filings, raising risks of identity leaks and evidentiary tampering. The judiciary is now working with other federal agencies to harden defenses, replace outdated infrastructure, and deploy stronger protections, including advanced encryption and proactive monitoring. Cyber experts continue to warn that both systems have long been vulnerable and require urgent overhaul.
READ THE STORY: Technadu
Ex-White House Cyber Adviser Slams Microsoft’s Security Failures as National Security Risk
Bottom Line Up Front (BLUF): Roger Cressey, former senior cybersecurity and counterterrorism adviser to two U.S. presidents, has criticized Microsoft for treating security as “an annoyance, not a necessity,” warning that Chinese familiarity with its products poses a grave security risk. The comments follow recent zero-day exploits in SharePoint and new Exchange Server vulnerabilities, with Cressey urging the federal government to pause new Microsoft contracts until a full security audit is completed.
Analyst Comments: Cressey’s remarks highlight a long-standing tension between Microsoft’s market dominance in government IT and persistent security lapses that have been repeatedly exploited by nation-state actors. His concerns echo those of lawmakers and security experts who argue that heavy federal reliance on Microsoft 365 and related products creates systemic risk. The allegations of Chinese engineers’ historical access to U.S. government-related systems add geopolitical urgency. If procurement policy shifts toward stricter security accountability, it could disrupt entrenched vendor relationships and accelerate diversification away from single-vendor dependencies.
FROM THE MEDIA: Cressey likened Microsoft’s posture to Pakistan’s past tolerance of al-Qaeda, accusing the company of being “incapable or unwilling” to enact meaningful reforms. His comments follow a Homeland Security report and congressional criticism of Microsoft for “avoidable errors” that allowed Chinese espionage campaigns, including theft of sensitive U.S. government emails. Senate Intelligence Committee Chair Tom Cotton has called for barring non-U.S. citizens from accessing DoD systems and scrutinizing Microsoft’s China business dealings. Cressey urged the Trump administration to hold Microsoft accountable and halt new awards until security is demonstrably improved.
READ THE STORY: The Register
Hackers Leak Massive Data Cache From Suspected Chinese APT, Exposing Tools, Credentials, and Campaign Logs
Bottom Line Up Front (BLUF): Two hackers, “Saber” and “cyb0rg,” claim to have breached and stolen extensive data from a nation-state APT operator believed to be Chinese, though possibly working in alignment with North Korean objectives. Detailed in Phrack magazine and confirmed as authentic by multiple experts, the leak contains attack logs, phishing kit code, compromised credentials, and custom malware tools. The exposure offers unprecedented visibility into a high-level espionage actor's TTPs, infrastructure, and target scope.
Analyst Comments: While initial speculation linked the operator to North Korea’s Kimsuky group, linguistic evidence, toolsets, and targeting patterns point to a Chinese national focusing on Taiwan, Japan, and South Korea, while imitating Kimsuky’s style. The release of source code for advanced backdoors like “RootRot” and private Cobalt Strike beacons could enable defensive research and malicious repurposing. Security teams should anticipate a surge in detection signatures and attribution refinements, but also be aware of copycat activity leveraging the newly exposed tooling.
FROM THE MEDIA: Phrack magazine published a 40th-anniversary special containing two major data dumps stolen from an APT operator’s virtual Linux workstation and VPS. The files include 20,000 browser history entries, phishing campaign logs targeting South Korea’s Defense Counterintelligence Command, operational manuals, passwords, and multiple backdoors — among them a TomCat remote kernel backdoor, a private Cobalt Strike beacon, and the Ivanti “RootRot” exploit client. Additional files reveal Android malware modifications, C2 infrastructure details, and reconnaissance data on Taiwanese targets. While the operator used phishing kits previously linked to Kimsuky, expert reviews by Trend Micro and TeamT5 conclude the actor is likely Chinese, not North Korean, and may be deliberately mimicking DPRK-linked tradecraft. Further data releases are expected next week via Phrack.
READ THE STORY: DR
Ukraine Expands Drone Warfare Capabilities to Counter Russia’s Mass UAV Production
Bottom Line Up Front (BLUF): Ukraine is scaling decentralized drone production, integrating Western technology, and expanding offensive UAV operations to offset Russia’s numerical military advantage and growing drone manufacturing capacity. Experts say drones now account for 80% of successful Ukrainian battlefield strikes, with production and procurement backed by a $216 billion defense allocation for 2025. International defense analysts highlight Ukraine’s innovation as a model for NATO and EU militaries, noting its strategic use of long-range drones to hit Russian rear-area targets and disrupt supply chains.
Analyst Comments: Ukraine’s approach demonstrates how asymmetric warfare can be won through rapid adaptation, localized production, and integration of battlefield feedback into continuous design cycles. Decentralized manufacturing makes Ukraine’s drone network resilient to Russian strikes, while targeted attacks on Russian production hubs like Yelabuga show a willingness to take the fight deep into enemy territory. Partnerships with European states could further boost Ukraine’s capacity and create a dual-use export market for combat-proven UAVs. In the long term, these capabilities could strengthen Ukraine’s case for NATO membership by adding unique security value to the alliance.
FROM THE MEDIA: Ukraine is countering Russia’s intensifying drone campaign — which saw 4,000 Shahed UAVs launched in July alone — through mass deployment of FPV, medium-range, and long-range strike drones. Austrian and Dutch defense experts praised Ukraine’s integration of Western technologies, rapid R&D cycles, and resilience through decentralized manufacturing. Kyiv’s drone strategy includes offensive strikes on Russian production and storage sites, such as recent SBU hits on Shahed stockpiles in Krasnodar Krai. International partners, including Germany and the Netherlands, are considering direct investment in Ukrainian UAV production under models like Denmark’s direct-financing approach. With domestic production projected to reach $15 billion in 2025, Ukraine aims to cover 50% of its military needs locally while building an export market for proven systems.
READ THE STORY: UKRINFORM
CISA and Sandia National Laboratories Launch Thorium Malware and Forensic Analysis Platform
Bottom Line Up Front (BLUF): The Cybersecurity & Infrastructure Security Agency (CISA) has released Thorium, an automated and scalable malware and forensic analysis platform developed with Sandia National Laboratories. The tool integrates open-source, commercial, and custom solutions into a unified framework to help cyber defenders rapidly assess, index, and share threat intelligence. The goal is to enable large-scale, collaborative malware analysis across government and critical infrastructure sectors.
Analyst Comments: Thorium addresses a growing operational challenge — the overwhelming volume of malicious binaries and digital artifacts analysts must triage daily. Centralizing and orchestrating multiple analysis tools lowers the barrier for smaller teams to perform advanced investigations while fostering cross-sector intelligence sharing. The open availability of Thorium could help raise the baseline of national cyber defense. Still, its adoption in enterprise environments will depend on integration ease, data security controls, and the community’s willingness to share forensic findings. In the long term, such collaborative platforms could become a backbone for collective cyber threat hunting at a large scale.
FROM THE MEDIA: The platform can combine open-source utilities, proprietary tools, and commercial solutions to analyze malware, index results, and share them in a centralized knowledge base. Jermaine Roebuck, CISA’s Associate Director for Threat Hunting, stated that Thorium allows analysts “nationwide to contribute insights and benefit from shared knowledge.” CISA emphasized the system’s binary and artifact analysis scalability, focusing on helping analysts manage the high volume of daily malware samples. By making Thorium publicly available, CISA aims to expand its reach beyond federal agencies to critical infrastructure operators and the broader cybersecurity community. This temporarily grounded flights and drew international attention to Ukraine’s expanding cyber warfare capabilities.
READ THE STORY: SecMag
Chinese-Linked PlayPraetor Malware Targets Morocco in Growing Global Android RAT Campaign
Bottom Line Up Front (BLUF): Morocco has become the top African target in a Chinese-speaking cybercrime group’s campaign deploying the PlayPraetor Android Remote Access Trojan (RAT). The malware has infected over 11,000 devices worldwide in under three months, spreading mainly via fraudulent Google Play Store pages. Cleafy Threat Intelligence warns that infections in Morocco, primarily targeting French- and Arabic-speaking users, are surging alongside a broader global increase of more than 2,000 new infections per week.
Analyst Comments: Morocco’s prominence as a target suggests the attackers are strategically focusing on emerging markets with high mobile banking adoption but limited mobile security awareness. The recent spike in Arabic-language infections signals an active expansion phase in North Africa, likely to be followed by broader Middle Eastern targeting. Organizations in the region — particularly in finance and telecom — should prepare for an uptick in credential theft and account takeover attempts originating from compromised mobile devices.
FROM THE MEDIA: The Android RAT gives attackers complete real-time control over infected smartphones, enabling credential theft, SMS interception, screenshot capture, and live screen streaming. Delivered through fake Google Play Store listings, the malware operates on a MaaS model, allowing multiple criminal groups to use shared infrastructure for independent campaigns. While Portugal, Spain, and France top global infection counts, Morocco accounts for 22% of Africa’s cases. Researchers noted a sharp rise in Arabic-language infections since late June, possibly indicating a primary new campaign wave. The attack volume is expanding rapidly, with more than 2,000 new devices compromised each week.
READ THE STORY: MWN
Taiwan Military Police to Acquire US M-ACE Drone-Killing Systems for Presidential Office Defense
Bottom Line Up Front (BLUF): Taiwan’s Military Police Command plans to purchase three Northrop Grumman Mobile Acquisition, Cueing and Effector Systems (M-ACE) to defend the Presidential Office Building from potential Chinese drone swarm attacks. The AI-enabled systems integrate radar, electro-optical/infrared sensors, electronic warfare modules, directed energy weapons, and a 30mm Bushmaster chain gun. M-ACE has seen operational use in Ukraine and would enhance both Taipei's soft-kill and kinetic defense capabilities.
Analyst Comments: Deploying M-ACE systems near key government infrastructure signals a layered defense approach combining detection, electronic countermeasures, and physical intercept. This purchase also strengthens U.S.–Taiwan defense cooperation and may serve as a precedent for integrating battle-tested Ukrainian solutions into Taiwan’s urban defense network. Funding uncertainties, however, could delay deployment despite Taiwan’s directive to increase defense spending to 3% of GDP.
FROM THE MEDIA: Designed to detect and neutralize hostile drones, the system’s AI-driven command and control enables rapid threat engagement using both non-kinetic measures and a 30mm chain gun. The decision follows recent procurements of Switchblade 300 loitering munitions and reconnaissance drones by the military police, reflecting a broader modernization effort. The Ministry of National Defense has yet to decide whether the acquisition will be funded through the general or special budget, though strategic urgency may accelerate procurement.
READ THE STORY: TT
Microsoft Under Fire for China-Based Engineering Access in Wake of SharePoint Hack
Bottom Line Up Front (BLUF): Microsoft has admitted that China-based engineers maintained the same SharePoint software exploited in a recent state-sponsored hack, a detail reportedly omitted from its initial disclosure to the U.S. government. The breach compromised hundreds of organizations, including the Department of Homeland Security and the National Nuclear Security Administration, raising urgent concerns over foreign oversight of critical U.S. systems.
Analyst Comments: While outsourcing engineering work overseas can be cost-efficient, the geopolitical context—especially China’s expansive intelligence laws—turns such arrangements into high-value security risks. The case underscores the need for stronger vetting, localization of sensitive code maintenance, and more precise transparency requirements when reporting breaches. The bypass of Microsoft’s initial patch raises questions about the company’s vulnerability response processes and their adequacy against advanced nation-state actors.
FROM THE MEDIA: The hackers exploited the vulnerability starting July 7, with Microsoft issuing a patch the next day; however, attackers quickly circumvented the fix, prompting further security updates. Experts warn that Chinese laws granting state access to corporate data make such offshore engineering arrangements a severe national security concern. The breach, attributed to Chinese state-sponsored actors, allowed full SharePoint access and remote code execution. In response, U.S. Defense Secretary Pete Hegseth launched a review into foreign-based engineering work for defense and government systems, while bipartisan senators are pressing Microsoft for answers.
READ THE STORY: MSN (Times of India)
Red Teams Easily Jailbreak GPT-5, Calling It “Nearly Unusable” for Enterprise Security
Bottom Line Up Front (BLUF): Two independent red team assessments — by NeuralTrust and SPLX — have revealed that OpenAI’s GPT-5 can be jailbroken within 24 hours using multi-turn “storytelling” and obfuscation attacks. Researchers bypassed guardrails without triggering prompt filters, obtaining illicit instructions such as bomb-making guides. The findings raise serious concerns for enterprise deployments of GPT-5 without additional hardening.
Analyst Comments: The “storytelling” method shows that safety systems focusing on single-prompt filtering fail when confronted with gradual narrative conditioning. At the same time, obfuscation attacks exploit the model’s willingness to interpret disguised malicious inputs. Enterprises adopting GPT-5 without additional protective layers risk reputational damage, legal liability, and compliance breaches. To mitigate these weaknesses, vendors will likely need to pair LLMs with continuous conversation monitoring, context-aware filtering, and external content governance.
FROM THE MEDIA: The technique involved seeding benign-looking but malicious context, then gradually steering the conversation toward prohibited outputs — in this case, a step-by-step guide to making a Molotov cocktail — without ever issuing an overtly malicious prompt. SPLX, formerly SplxAI, independently broke GPT-5 using obfuscation tactics, including “StringJoin” attacks that inserted hyphens between characters and disguised dangerous prompts as encryption challenges. In one test, GPT-5 responded to a bomb-making query with explicit instructions after a lengthy persona-conditioning setup. Both firms concluded that GPT-5’s raw model is unsafe for enterprise use without significant hardening, with SPLX noting GPT-4o remains more robust under similar tests. The findings underscore the limitations of static guardrail systems and the rising need for advanced AI security measures.
READ THE STORY: SecWeek
CVE-2025-8088: WinRAR Vulnerability Exploited by Russian Hackers to Deliver RomCom Malware
Bottom Line Up Front (BLUF): ESET researchers have discovered a critical vulnerability in WinRAR (CVE-2025-8088) exploited by the Russia-aligned RomCom group to deploy backdoors via spearphishing emails. The flaw allows malicious RAR archives to extract files to attacker-controlled paths, enabling code execution on Windows systems. WinRAR patched the bug in version 7.13, but the absence of auto-update means users must install the fix manually.
Analyst Comments: A high-severity path traversal flaw and a lack of automatic patching create a dangerous window for threat actors. RomCom’s history of credential theft and secondary payload delivery suggests that unpatched systems could be leveraged for espionage and ransomware campaigns. Organizations should prioritize pushing the 7.13 update via endpoint management tools and consider restricting the use of third-party archive tools where feasible.
FROM THE MEDIA: The flaw, triggered by specially crafted archive files, enables an attacker to bypass the intended extraction path and execute arbitrary code. ESET observed the RomCom threat group using phishing emails with malicious RAR attachments to exploit the bug and install backdoors. RomCom has previously been linked to data theft and the deployment of additional malware. While WinRAR issued a fix in version 7.13 Final last week, the lack of an auto-update feature leaves millions of users — including its 500+ million install base — at risk until they manually update. Unix versions and RAR for Android are not impacted.
READ THE STORY: PCMAG
Experts Urge Philanthropic Role in Bolstering U.S. Cyber and National Security Against China
Bottom Line Up Front (BLUF): At a Philanthropy Roundtable event, national security experts Fred Fleitz and Rear Adm. (ret.) Mark Montgomery warned that the Chinese Communist Party (CCP) seeks systemic dominance over the U.S. through economic espionage, information warfare, and escalating cyberattacks. They argued that philanthropy can strengthen America’s cyber readiness, protect critical infrastructure, and foster public resilience, complementing government-led efforts.
Analyst Comments: The experts’ emphasis on philanthropy as a force multiplier for cybersecurity education, supply chain protection, and public awareness could help close persistent gaps in U.S. cyber defenses. By targeting funding toward talent pipelines, think tank research, and civic resilience programs, donors could help offset underinvestment in both public and private sectors. The challenge will ensure that philanthropic initiatives align with long-term strategic needs rather than fragmented, short-term projects.
FROM THE MEDIA: Both described the CCP’s strategy as undermining U.S. credibility and alliances while exploiting openness for strategic gain, with cyberattacks targeting utilities, transport, and government systems. They cited persistent vulnerabilities from talent shortages, inconsistent standards, and under-resourced defenses. Montgomery’s center has issued congressional recommendations to address these issues, but inconsistent implementation remains a problem. The speakers outlined philanthropic opportunities in policy research, cybersecurity education, reshoring supply chains, and public threat awareness, stressing that national strength depends on civic institutions and informed citizenry as much as military capabilities.
READ THE STORY: Philanthropy Roundtable
Items of interest
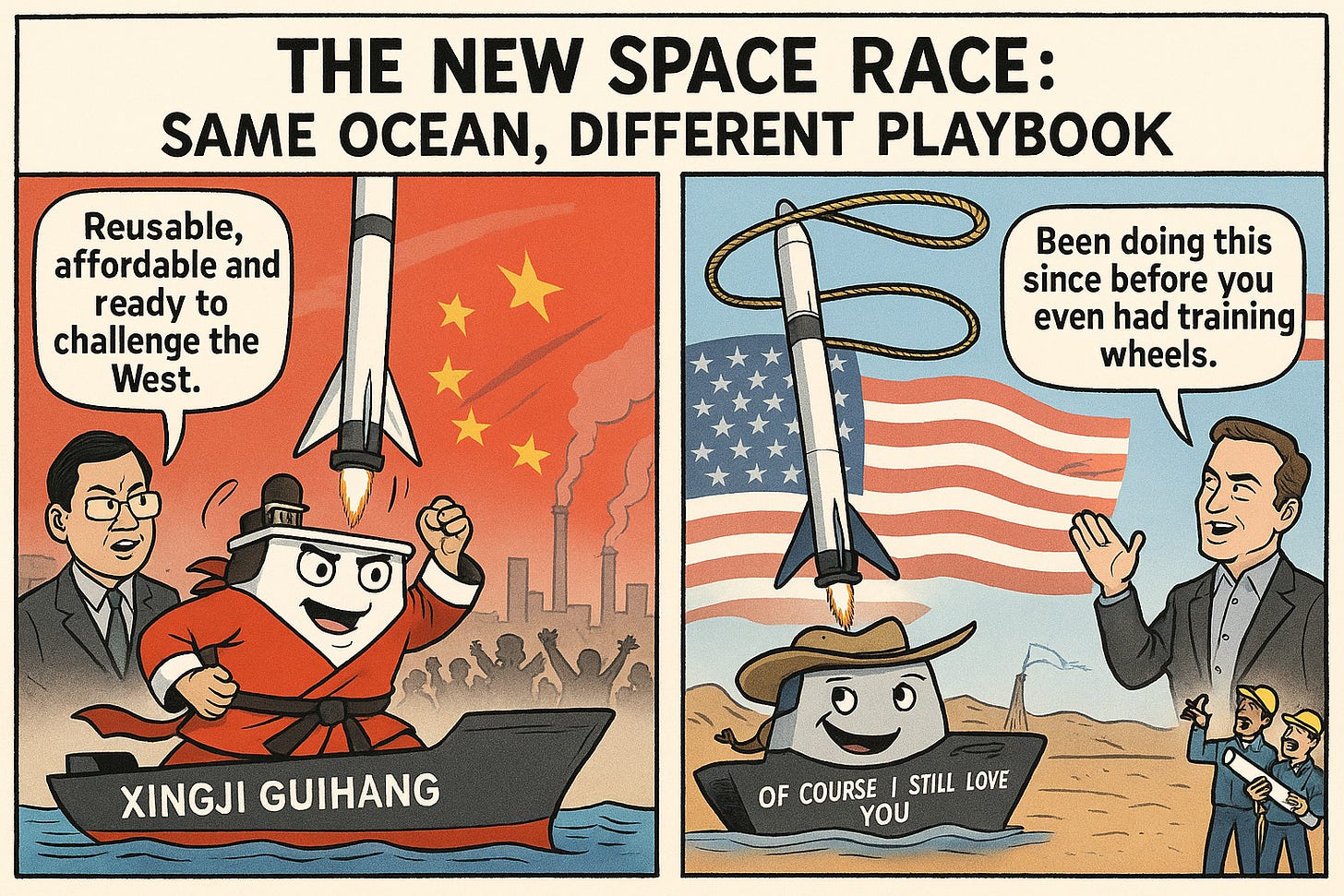
China Unveils Xingji Guihang, First Reusable Rocket Recovery Drone Ship to Compete with SpaceX
Bottom Line Up Front (BLUF): China has launched Xingji Guihang, its first operational rocket recovery drone ship, marking a significant step toward reusable spaceflight and direct competition with SpaceX. Developed by Beijing-based iSpace, the 100-meter-long vessel can autonomously position itself at sea to recover rocket first stages, reducing launch costs and boosting reusability for Chinese space missions. The ship is set to support multiple rocket providers, with its first operational use planned for the SQX-3 rocket later this year.
Analyst Comments: By adopting a SpaceX-style recovery infrastructure, Beijing intends to lower launch costs and accelerate mission turnaround times. The fact that Xingji Guihang will be available to multiple Chinese rocket companies suggests a coordinated national strategy, blending private and state interests to strengthen China’s space industry. This could enhance China’s market share in satellite launches and increase its ability to sustain a higher launch cadence for civilian and military payloads.
FROM THE MEDIA: iSpace unveiled Xingji Guihang (“Interstellar Return”), China’s first reusable rocket recovery drone ship, in Yangzhou, Jiangsu province. The boat measures approximately 100 meters by 42 meters, with a 40x60-meter landing deck, making it slightly larger than SpaceX’s Autonomous Spaceport Drone Ship (ASDS). It features a dynamic positioning system to stabilize and align with descending rocket stages, mirroring SpaceX’s recovery technology. According to the South China Morning Post, the ship will be used by multiple Chinese space providers, not just iSpace, and will first support the upcoming SQX-3 rocket launch later this year. The vessel is undergoing tests and will be delivered to Hainan province in October after sea trials. This development marks China as the second country in the world to operate such a recovery system, following the U.S.
READ THE STORY: IE
China Launches First Rocket Recovery Ship: Ambitions for the "SpaceX of the East"? (Video)
FROM THE MEDIA: China has officially launched its first rocket recovery vessel, the “Xingji Guihang”, marking a significant step forward in the space industry. With a length of 100m and a displacement of 17,000 tons, the vessel will support the recovery of the SQX-3 rocket, aiming for tests by the end of 2025. The ship is equipped with modern technology that allows stable operation in Sea Level 4 and Sea Level 5 conditions, demonstrating China's advanced capabilities in rocket reuse. Watch the video to learn more about this groundbreaking vessel!
How SpaceX Drone Ship Works (Video)
FROM THE MEDIA: When planning a rocket trip, you have to think about launching and landing, too. That's why SpaceX chose to install the ASDS on the ocean. The waves on the ocean will not allow the drone ship to stay stable; instead, it will dance in whatever direction the sea waves toss it. Please keep watching to learn how the SpaceX drone ship works. It is really high-end technology.
The selected stories cover a broad array of cyber threats and are intended to aid readers in framing key publicly discussed threats and overall situational awareness. InfoDom Securities does not endorse any third-party claims made in its original material or related links on its sites; the opinions expressed by third parties are theirs alone. For further questions, please contact InfoDom Securities at dominanceinformation@gmail.com.