Action Required
01-02-26
UPDATES: AIS_Tracker
This was put on the 28th, and we are just under 1k clones. All of you rock.
There is a lot to iron out, but at this point, even with the bugs, it's in a class of its own as a free maritime fusion platform.
Arsenal Ship Tracker
What is this?
“A free, open-source maritime intelligence fusion proof-of-concept that demonstrates capabilities typically found only in commercial systems.”
It’s a maritime gray-zone monitoring system for tracking vessels suspected of civilian-to-military conversion, containerized weapons systems, and dual-use activity.
Live Demo
View Static Demo on GitHub Pages
Screenshots
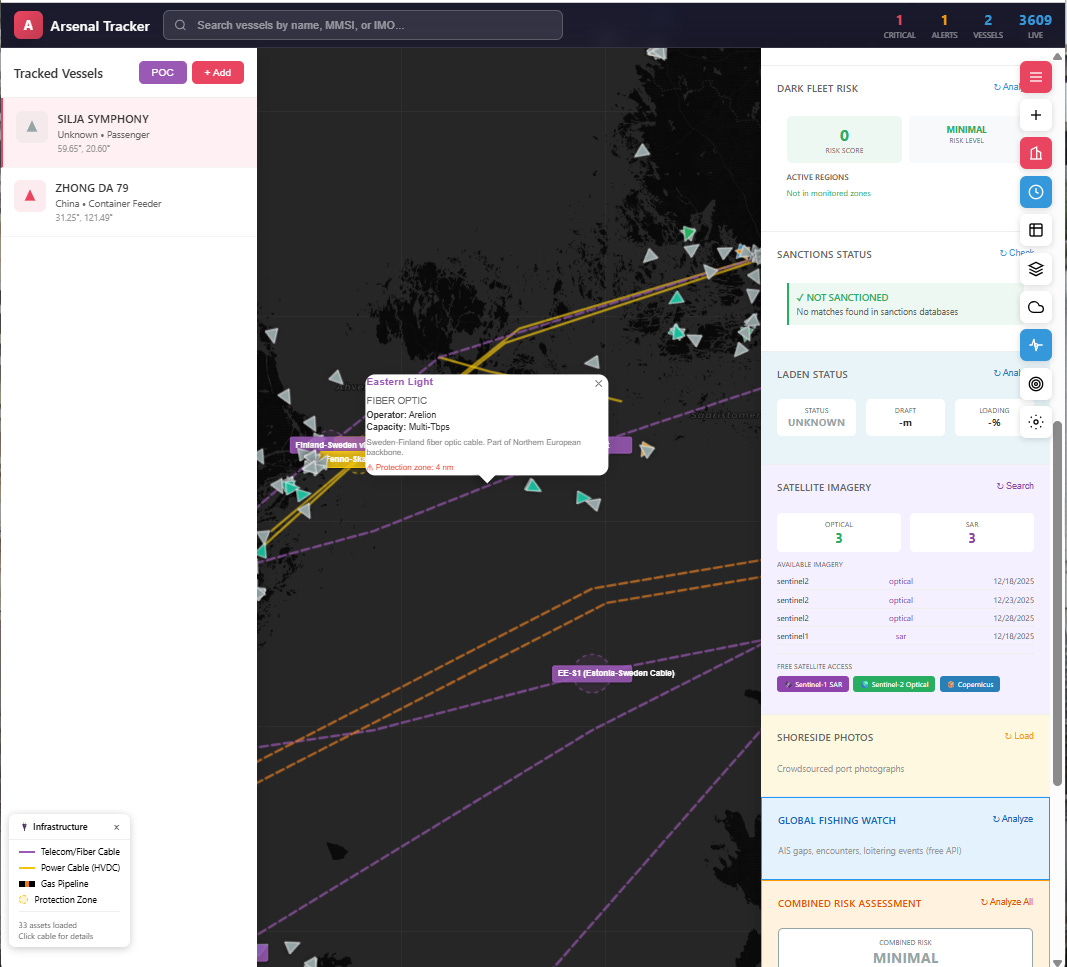
Dashboardual-use activity.
Main tracking interface with vessel markers, confidence scoring breakdown, and threat assessment panel
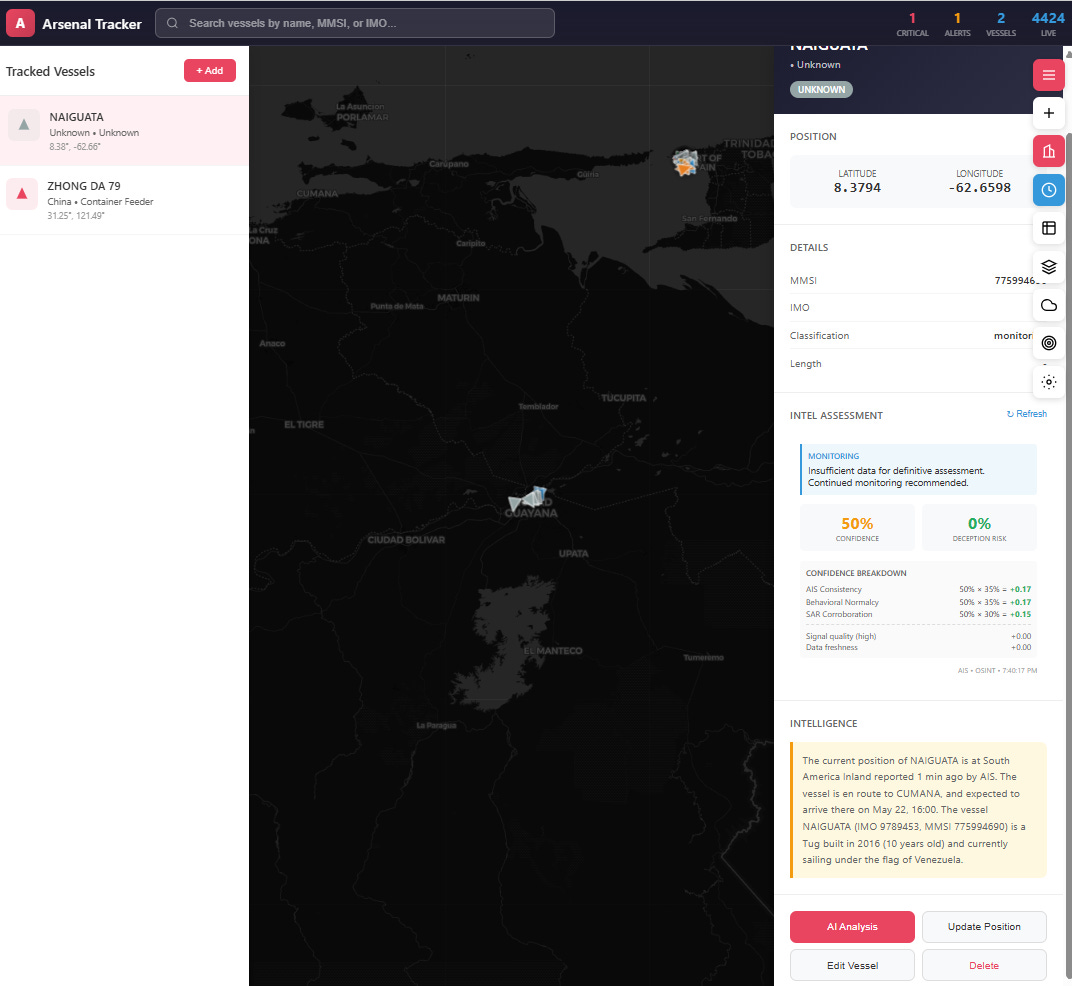
Track Live Vessel
Add any AIS vessel to your tracking database by MMSI
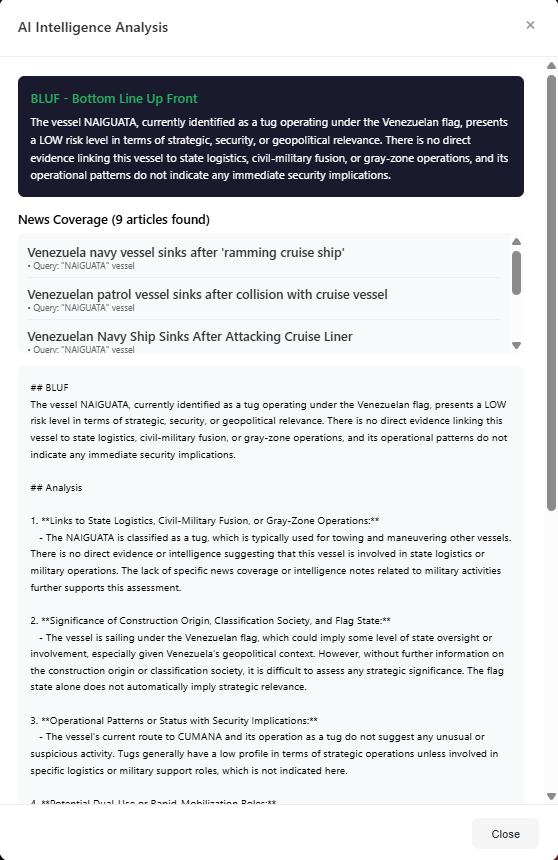
AI Intelligence Analysis
OpenAI-powered strategic intelligence with MMSI lookups and news correlation
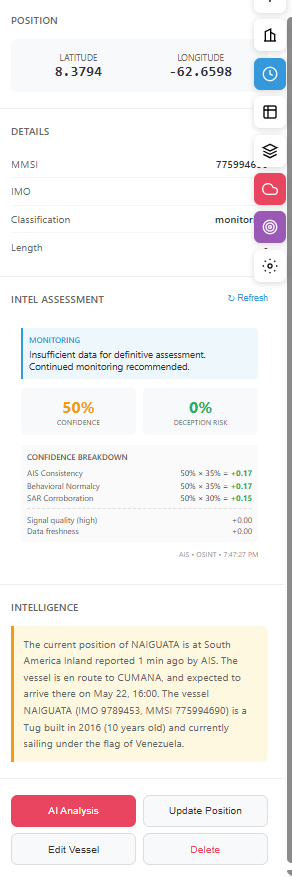
Intelligence Results
BLUF assessment with risk level, confidence breakdown, and analyst-visible indicators
Overview
This proof-of-concept tracker monitors vessels like ZHONG DA 79 - a Chinese container feeder converted to an arsenal ship carrying 60+ containerized missiles, CIWS, and radar while retaining civilian classification.
Features
Core Tracking
VesselFinder-style UI - Full-screen dark map with slide-in panels
Live AIS streaming - Real-time vessel positions via aisstream.io WebSocket
Multi-source AIS - Support for AISStream, AISHub, and Marinesia APIs
Ship markers with heading - Vessel icons rotate based on course
Vessel-type color coding - Different colors for cargo, tanker, passenger, military, etc.
Track with timestamps - Click vessel to see historical track with time markers
Green marker = track start, Red marker = latest position
Hover for timestamp, speed, and course at each point
Viewport-optimized rendering - Handles 10,000+ live vessels without browser lag
SQLite WAL mode - Better concurrent database access
Vessel Management
Add/Edit/Delete vessels - Full CRUD operations with UI forms
Track live vessels - Add any AIS vessel to your tracking database
Photo upload - Attach vessel images with base64 storage
Comprehensive vessel forms - Track weapons config, classification, threat levels
MMSI-based enrichment - Auto-populate vessel data from tracking databases
Intelligence Features
AI-powered vessel analysis - OpenAI integration for strategic intelligence
MMSI vessel lookups - Query VesselFinder, MarineTraffic, ITU MARS databases
Auto-update fields - Automatically populate flag, type, IMO from lookups
Targeted search queries - Uses exact vessel names and IMO for accurate results
BLUF assessments - Bottom Line Up Front risk analysis (LOW/MODERATE/HIGH/CRITICAL)
Analysis persistence - Save and retrieve AI analysis for each vessel
News correlation - Automated news search with relevance filtering
OSINT integration - Link to news articles and intelligence reports
Weather & Environment
Weather enrichment - Open-Meteo API integration (no API key required)
Marine conditions - Wave height, sea state, swell data
Vessel weather - Get weather at any vessel’s current position
Geospatial
Shipyard geofences - Monitor vessel proximity to facilities of interest
Position tracking - Historical vessel track display
Bounding box configuration - Define AIS streaming areas via UI
SAR Ship Detection (NEW)
ESA SNAP integration - Import ship detections from ESA Sentinel-1 SAR imagery
CSV/XML parsing - Parse SNAP Ship Detection toolbox output files
AIS correlation - Match SAR detections with AIS positions (configurable time/distance thresholds)
Dark vessel detection - Identify vessels visible on SAR but not transmitting AIS
Detection metadata - Track detection time, coordinates, estimated length, confidence
SAR layer toggle - View SAR detections on map (purple=matched, red=dark vessel)
EO Browser integration - One-click access to Sentinel-1 SAR imagery for the current map view
Satellite overlay - NASA daily satellite imagery with adjustable opacity
Vessel Confidence Scoring (NEW)
AIS consistency score - Analyze position reporting gaps and jumps
Behavioral normalcy score - Detect unusual speed/course changes
SAR corroboration score - Cross-reference with SAR detections
Deception likelihood - Calculate probability of AIS spoofing/manipulation
Overall confidence - Weighted composite score (0.0-1.0)
Cached scoring - Scores cached and refreshable on demand
UI confidence panel - Visual confidence display in vessel details with refresh button
Testing
173 unit tests - Comprehensive test coverage
Test runner -
python3 run_tests.pyto run all testsModule tests - Database, API, SAR import, confidence scoring, intelligence
Quick Start
# Install dependencies
pip install -r requirements.txt
# Initialize database with seed data
python3 server.py init
# Start live AIS streaming (in separate terminal)
python3 stream_area.py
# Start the web server
python3 server.py
# Open http://localhost:8080 in browserEnvironment Variables
# Required for AI intelligence features
export OPENAI_API_KEY=”your-openai-api-key”
# Required for live AIS streaming (primary source)
export AISSTREAM_API_KEY=”your-aisstream-api-key”
# Optional: AISHub community data sharing (register at aishub.net)
export AISHUB_USERNAME=”your-aishub-username”Components
FileDescriptionserver.pyREST API server with vessel intel, weather & news searchvessel_intel.pyAI-powered vessel intelligence with MMSI lookupsweather.pyWeather enrichment via Open-Meteo APIstream_area.pyLive AIS streaming from aisstream.ioschema.sqlSQLite database schema + seed datastatic/index.htmlVesselFinder-style interactive dashboarddocs/index.htmlStatic GitHub Pages demo versionrequirements.txtPython dependencies (gnews, openai)ais_ingest.pyAIS data ingestion moduleais_config.jsonAIS source configuration (auto-created)ais_sources/Multi-source AIS integration (AISStream, AISHub, Marinesia)osint/OSINT correlation and monitoring toolssar_import.pySAR ship detection import and AIS correlationconfidence.pyVessel confidence scoring and deception detectionintelligence.pyFormal intelligence output with analyst-visible breakdownbehavior.pyBehavior detection: loitering, AIS gaps, STS transfers, dark fleet scoringvenezuela.pyVenezuela dark fleet detection: zone monitoring, AIS spoofing, risk scoringsanctions.pySanctions database: FleetLeaks API, OFAC SDN, vessel compliance checkinginfra_analysis.pyInfrastructure threat analysis: anchor drag, cable proximity, incident correlationladen_status.pyLaden status detection: draft analysis, cargo operations, STS transfer detectionsatellite_intel.pySatellite imagery integration: Sentinel-1/2, vessel detection, storage monitoringshoreside_photos.pyCrowdsourced photography: port photos, vessel verification, intel collectiongfw_integration.pyGlobal Fishing Watch API: AIS gaps, encounters, loitering, vessel identityrun_tests.pyTest runner scripttests/Unit tests for database, API, SAR, confidence, intelligence, Venezuela, sanctions
API Endpoints
Vessel Operations
MethodEndpointDescriptionGET/api/vesselsAll vessels with latest positionGET/api/vessels/:idSingle vessel detailsGET/api/vessels/:id/track?days=90Position historyGET/api/vessels/:id/eventsEvent timelinePOST/api/vesselsAdd vesselPUT/api/vessels/:idUpdate vesselDELETE/api/vessels/:idDelete vesselPOST/api/vessels/:id/positionLog positionPOST/api/vessels/:id/eventLog eventPOST/api/track-vesselAdd live vessel to tracking
Intelligence Operations
MethodEndpointDescriptionGET/api/vessels/:id/intelFormal intelligence assessment with breakdownGET/api/vessels/:id/intel?summary=trueQuick intel summaryPOST/api/vessel-intelFull AI analysis with news searchPOST/api/vessel-blufQuick BLUF risk assessmentPOST/api/search-newsSearch Google News for vesselGET/api/osint?vessel_id=1OSINT reportsPOST/api/osintAdd OSINT report
Weather Endpoints
MethodEndpointDescriptionGET/api/weather?lat=31.2&lon=121.4Weather at coordinatesGET/api/vessels/:id/weatherWeather at vessel position
SAR Detection Endpoints
MethodEndpointDescriptionGET/api/sar-detectionsList SAR ship detectionsGET/api/dark-vesselsList dark vessels (SAR without AIS match)
Confidence Scoring Endpoints
MethodEndpointDescriptionGET/api/vessels/:id/confidenceGet cached confidence scoreGET/api/vessels/:id/confidence?refresh=trueCalculate fresh confidence score
Venezuela Dark Fleet Endpoints
MethodEndpointDescriptionGET/api/venezuela/configMonitoring zone configurationGET/api/venezuela/known-vesselsKnown dark fleet vessels databaseGET/api/vessels/:id/venezuelaFull risk analysis (zone, score, alerts)
Sanctions Database Endpoints
MethodEndpointDescriptionGET/api/sanctions/check?imo=XCheck vessel by IMOGET/api/sanctions/check?name=XCheck vessel by nameGET/api/sanctions/statsDatabase statisticsGET/api/vessels/:id/sanctionsVessel sanctions status
Other Endpoints
MethodEndpointDescriptionGET/api/shipyardsMonitored facilitiesGET/api/events?severity=critical&limit=50All events (filterable)GET/api/alertsUnacknowledged alertsGET/api/watchlistWatchlist with vessel detailsGET/api/statsDashboard statisticsGET/api/live-vesselsLive AIS streaming vesselsGET/api/vessels/:id/analysisGet saved AI analysisPOST/api/alerts/:id/acknowledgeAcknowledge alertPOST/api/config/bounding-boxSave AIS bounding box configPOST/api/vessels/:id/photoUpload vessel photo
Example API Calls
# Get all vessels
curl http://localhost:8080/api/vessels
# Full AI analysis for a vessel
curl -X POST http://localhost:8080/api/vessel-intel \
-H “Content-Type: application/json” \
-d ‘{”vessel”: {”name”: “ZHONG DA 79”, “mmsi”: “413000000”, “vessel_type”: “Container Feeder”, “flag_state”: “China”}}’
# Quick BLUF assessment
curl -X POST http://localhost:8080/api/vessel-bluf \
-H “Content-Type: application/json” \
-d ‘{”vessel”: {”name”: “ZHONG DA 79”, “classification”: “confirmed”, “threat_level”: “critical”}}’
# Add position update
curl -X POST http://localhost:8080/api/vessels/1/position \
-H “Content-Type: application/json” \
-d ‘{”latitude”: 31.24, “longitude”: 121.49, “source”: “manual”}’
# Update vessel
curl -X PUT http://localhost:8080/api/vessels/1 \
-H “Content-Type: application/json” \
-d ‘{”threat_level”: “critical”, “intel_notes”: “Updated intelligence”}’
# Get vessel confidence score
curl http://localhost:8080/api/vessels/1/confidence
# Get SAR detections
curl http://localhost:8080/api/sar-detections
# Get dark vessels (SAR without AIS)
curl http://localhost:8080/api/dark-vessels
# Get Venezuela monitoring config
curl http://localhost:8080/api/venezuela/config
# Get known dark fleet vessels
curl http://localhost:8080/api/venezuela/known-vessels
# Check vessel sanctions by name
curl “http://localhost:8080/api/sanctions/check?name=SKIPPER”
# Get sanctions database statistics
curl http://localhost:8080/api/sanctions/statsAI Intelligence Features
The vessel intelligence module (vessel_intel.py) provides:
MMSI-Based Vessel Lookups
When you run AI Analysis, the system queries multiple vessel tracking databases:
VesselFinder - Vessel details, IMO, flag
MarineTraffic - Comprehensive vessel data, dimensions, year built
ITU MARS - Official MMSI registry with owner information
MyShipTracking - Additional vessel data
Auto-Update Fields
After analysis, the system automatically updates the vessel record with:
Flag state, vessel type, IMO number
Callsign, owner, dimensions
Classification and threat level recommendations
Targeted Search Queries
Improved search accuracy with:
Exact vessel name searches:
"GRACEFUL STARS" vesselIMO-based searches:
IMO 9123456 shipRelevance filtering (only shows articles mentioning the vessel)
Strategic Analysis
Full vessel analysis with structured output:
State logistics and civil-military fusion assessment
Construction origin and flag state significance
Operational patterns and security implications
Dual-use and rapid-mobilization potential
News coverage analysis
Risk Levels
LOW - No significant concerns
MODERATE - Some factors warrant monitoring
HIGH - Significant security implications
CRITICAL - Immediate attention required
Analysis Persistence
AI analysis results are saved to the database
BLUF summaries are extracted and stored
Retrieve previous analysis via
/api/vessels/:id/analysis
SAR Ship Detection
The SAR import module (sar_import.py) enables integration with ESA Sentinel-1 SAR imagery:
Supported Formats
CSV - SNAP Ship Detection toolbox CSV export
XML - SNAP detection XML output
Detection Fields
FieldDescriptiondetection_timeTimestamp of SAR image acquisitionlatitude/longitudeDetection coordinatesestimated_lengthEstimated vessel length in metersdetection_confidenceAlgorithm confidence scorematched_mmsiAIS vessel if correlation found
AIS Correlation
Detections are correlated with AIS positions using configurable thresholds:
Time window: ±30 minutes (default)
Distance threshold: 5km (default)
Unmatched detections flagged as potential “dark vessels”
Usage
from sar_import import import_sar_file, get_dark_vessels
# Import SNAP detection file
results = import_sar_file(’detections.csv’, source=’sentinel-1’)
# Get vessels detected by SAR but not transmitting AIS
dark_vessels = get_dark_vessels(since=’2025-01-01’)Vessel Confidence Scoring
The confidence module (confidence.py) provides trust assessment for vessel data:
Score Components
ComponentWeightDescriptionAIS Consistency40%Position reporting regularity, gap analysisBehavioral Normalcy30%Speed/course change patternsSAR Corroboration30%Cross-reference with SAR detections
Scoring Algorithm
AIS Consistency: Penalizes large gaps (>1hr) and position jumps (>50nm)
Behavioral Normalcy: Flags unusual speed (>30kt) or rapid course changes
SAR Corroboration: Boosts score when SAR confirms vessel presence
Deception Likelihood: Combines factors indicating potential AIS manipulation
API Response
{
“vessel_id”: 1,
“overall_confidence”: 0.72,
“ais_consistency”: 0.85,
“behavioral_normalcy”: 0.65,
“sar_corroboration”: 0.50,
“deception_likelihood”: 0.15,
“calculated_at”: “2025-12-31T00:00:00Z”
}Behavior Detection & Dark Fleet Analysis
The behavior detection module (behavior.py) provides vessel behavior analysis based on peer-reviewed research:
Detection Capabilities
DetectionDescriptionReferenceAIS GapsIdentify vessels “going dark”Global Fishing Watch (2024)LoiteringDetect stationary behavior indicating STS transfersGFW Nature StudyPosition SpoofingFlag impossible vessel movementsMDPI (2021)STS TransfersShip-to-ship transfer detectionarXiv (2024)Dark Fleet ScoreMulti-factor risk assessmentMDPI (2023, 2025)
Dark Fleet Risk Scoring
Combines multiple indicators based on shadow fleet research:
Flag of Convenience (0-25 pts) - FOC and emerging shadow fleet flags
Vessel Age (0-20 pts) - Old vessels (>15-25 years) are common in shadow fleets
Ownership Opacity (0-15 pts) - Shell companies, hidden ownership
AIS Gaps (0-20 pts) - Primary shadow fleet tactic
Position Spoofing (0-15 pts) - Intentional deception
STS Transfers (0-15 pts) - Sanctions evasion indicator
Vessel Type (0-5 pts) - Tankers higher risk
Risk Levels
ScoreLevelAssessment70-100CriticalHigh probability of shadow fleet involvement50-69HighMultiple dark fleet indicators present30-49MediumSome concerning indicators detected15-29LowMinor risk factors present0-14MinimalNo significant dark fleet indicators
API Endpoints
MethodEndpointDescriptionGET/api/vessels/:id/behaviorFull behavior analysisGET/api/mmsi/validate?mmsi=XXXMMSI validationGET/api/mmsi/country?mmsi=XXXFlag country lookup
Venezuela Dark Fleet Detection (NEW)
Real-time monitoring for sanctioned vessel activity in Venezuelan waters, based on commercial intelligence methodologies (Kpler, Windward, TankerTrackers).
Background
920+ sanctioned tankers globally, ~40% serving Venezuela
95% YoY increase in high-risk tanker presence in Caribbean (2025)
Detection-to-interdiction transition: U.S. now physically seizing vessels
Monitoring Zones
LocationCoordinatesTypeRiskJose Terminal10.15°N, 64.68°WTerminalCriticalLa Borracha10.08°N, 64.89°WSTS ZoneCriticalBarcelona STS10.12°N, 64.72°WSTS ZoneHighAmuay Refinery11.74°N, 70.21°WRefineryHigh
Detection Capabilities
DetectionMethodBased OnAIS SpoofingSatellite-AIS position comparisonSkipper case studyCircle SpoofingGeometric pattern analysisGNSS manipulation researchGoing DarkAIS transmission gap detectionGFW methodologyIdentity LaunderingScrapped vessel database cross-reference”Zombie vessel” detectionSTS TransfersVessel proximity + loitering analysisarXiv 2024
Known Dark Fleet Vessels
VesselStatusNotesSkipperSeized80+ days AIS spoofing, Iran-Venezuela-China routeCenturiesSeizedDecember 2025Bella 1PursuedCurrently tracked by U.S. Navy
High-Risk Flags (Venezuela)
Cameroon, Gabon, Palau, Marshall Islands, São Tomé and Príncipe, Equatorial Guinea, Comoros, Togo, Tanzania, Djibouti
API Endpoints
MethodEndpointDescriptionGET/api/venezuela/configGet monitoring zone configurationGET/api/venezuela/known-vesselsList known dark fleet vesselsGET/api/vessels/:id/venezuelaFull Venezuela risk analysis for vessel
Example: Skipper Detection
from venezuela import (
detect_ais_spoofing,
calculate_venezuela_risk_score,
check_venezuela_alerts
)
# Detect AIS spoofing (Skipper showed Guyana, was at Jose)
ais_positions = [{”lat”: 7.5, “lon”: -57.5, “timestamp”: “...”}]
sat_positions = [{”lat”: 10.15, “lon”: -64.68, “timestamp”: “...”}]
spoofing = detect_ais_spoofing(ais_positions, sat_positions, mmsi)
# Returns: 550km discrepancy, severity=critical
# Calculate risk score
risk = calculate_venezuela_risk_score(
mmsi=”123456789”,
vessel_info={”name”: “Skipper”, “flag_state”: “Cameroon”}
)
# Returns: score=70+, risk_level=critical
# Check alerts for vessel in Venezuela zone
alerts = check_venezuela_alerts(mmsi, “Skipper”, position, track)
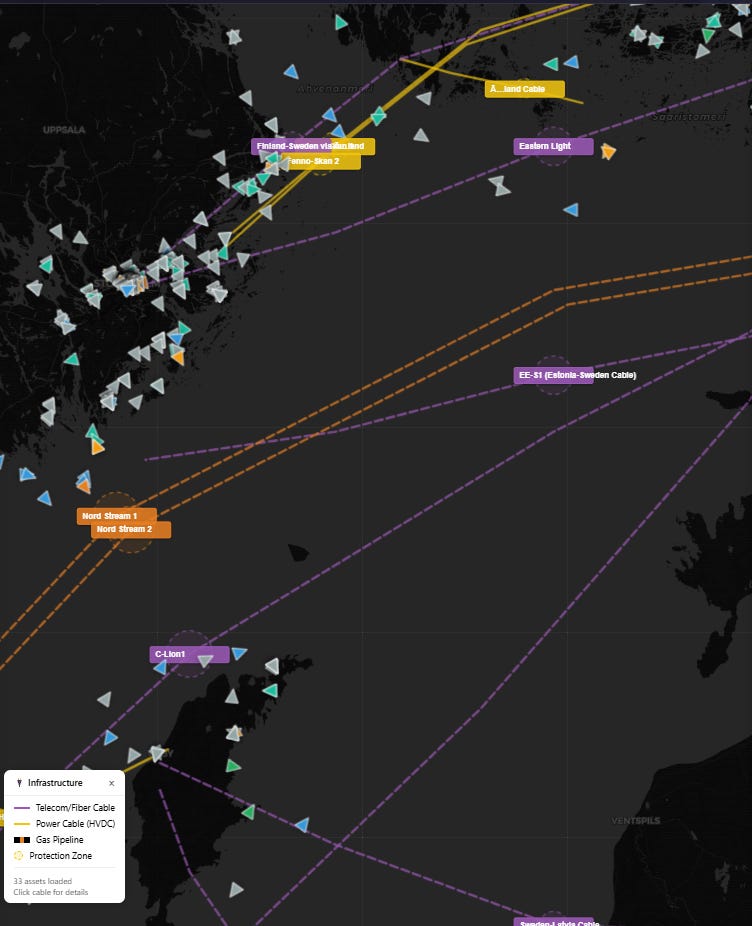
# Returns: TERMINAL_ARRIVAL, SANCTIONED_VESSEL alertsInfrastructure Threat Analysis (NEW)
Situational awareness for undersea cable and pipeline incidents, with anchor drag detection and AIS gap correlation. Developed for the Finland cable incident investigation (December 2025).
Global Infrastructure Database
56 infrastructure assets loaded from data/infrastructure.json across 7 regions:
RegionCablesPipelinesKey AssetsBaltic Sea223C-Lion1, Estlink-2, Nord StreamNorth Atlantic7-MAREA, Dunant, Grace Hopper, AmitiéTrans-Pacific4-FASTER, NCP, PLCN (Google/Meta)Asia-Pacific3-AAG, APG, SEA-ME-WE 3Taiwan Strait3-Cross-Strait 1/2, Taiwan-MatsuSouth China Sea1-SJC (Singapore-Japan)Gulf of Mexico-5Mars, Mardi Gras, Gulfstream
Strategic Cables:
CableRouteCapacityOperatorMAREAUS-Spain200 TbpsMicrosoft/MetaGrace HopperUS-UK-Spain350 TbpsGoogleFASTERJapan-US60 TbpsGoogle/KDDINCPChina-US80 TbpsChina Telecom/MicrosoftCross-StraitTaiwan-ChinaHighChunghwa/China Telecom
Recent Incidents Tracked:
InfrastructureDateVesselStatusC-Lion1Dec 31, 2025Under investigationDamagedEstlink-2Dec 25, 2025Eagle SDamagedEESF-1Dec 25, 2025Eagle SDamagedTaiwan-MatsuFeb 2, 2023Chinese vesselDamagedBCS East-West InterlinkNov 17, 2024Yi Peng 3DamagedBalticconnectorOct 8, 2023Newnew Polar BearDamaged
Detection Capabilities
DetectionMethodIndicatorsAnchor DragSpeed 0.3-4 kts + heading variance >15°Slow drift with erratic courseLoiteringExtended time in protection zoneCircling or stationary patternsAIS SuppressionSignal gaps correlating with zone entryDeliberate signal lossProximity AlertsDistance to infrastructure routesClose approach warnings
Risk Scoring
FactorWeightDescriptionProximity30%Distance to nearest infrastructureTime in Zone20%Duration within protection radiusBehavioral Indicators40%Anchor drag, loitering, AIS gapsAIS Gaps10%Signal loss near infrastructure
API Endpoints
MethodEndpointDescriptionGET/api/infrastructure/balticGet Baltic infrastructure for map overlayGET/api/vessels/:id/infra-analysisRun infrastructure incident analysis
Map Features
Infrastructure overlay - Colored lines for cables/pipelines with labels
Protection zones - Dashed circles showing exclusion areas
Toggle button - Enable/disable infrastructure layer (blue cable icon)
Legend panel - Color key in bottom-left corner when layer is active
🟣 Purple = Telecom/Fiber cables
🟡 Yellow = Power cables (HVDC)
🟠 Orange (dashed) = Gas pipelines
Click for details - Popup with operator, capacity, incident notes
Track timestamps - Hover on track markers to see position time, speed, and course
Usage Example
from infra_analysis import analyze_infrastructure_incident
# Analyze vessel track for cable incident correlation
analysis = analyze_infrastructure_incident(
track_history=positions,
mmsi=”518100989”,
vessel_name=”FITBURG”,
incident_time=”2025-12-31T06:00:00”
)
# Returns: risk_score, anchor_drag_detected, proximity_events, indicators
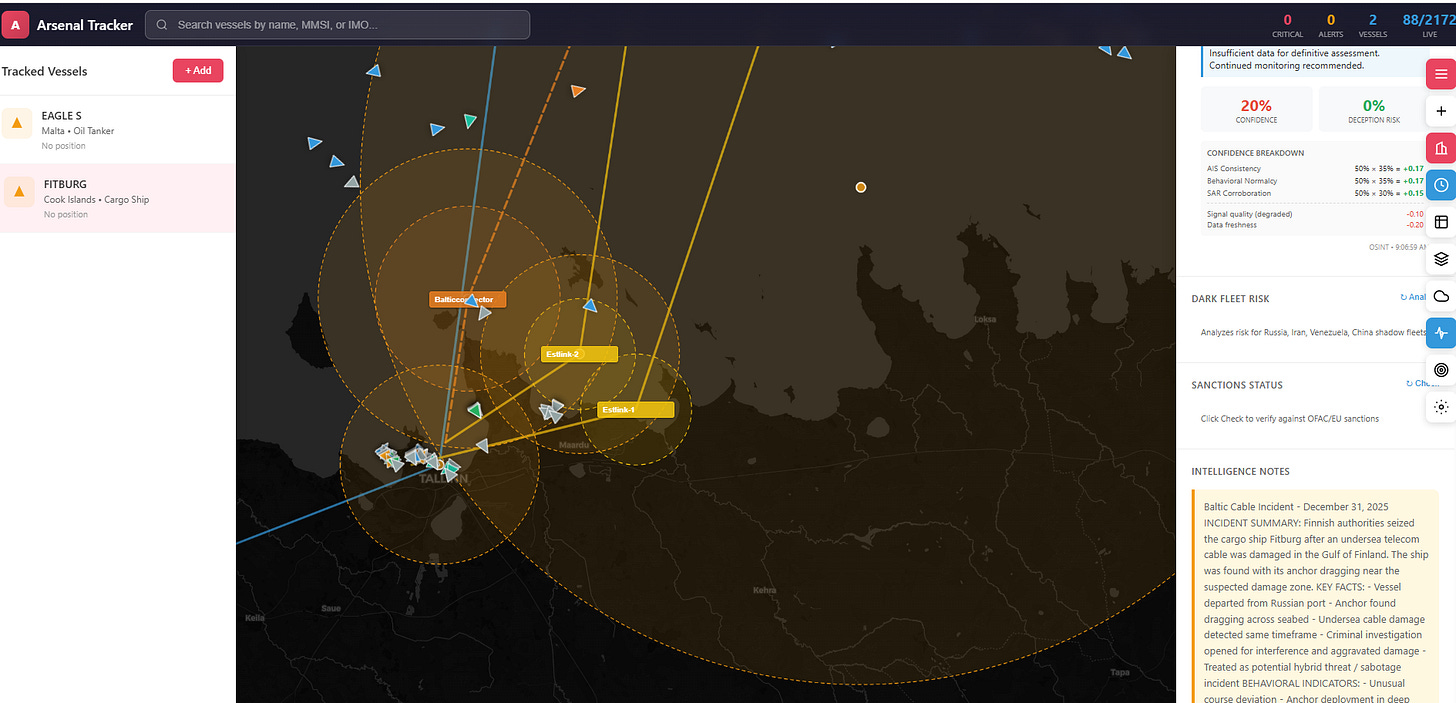
print(analysis.generate_report()) # Human-readable incident reportBaltic Cable Incident POC
Load via UI (recommended):
Click the purple POC button in the vessel list header
Select “Baltic Cable Incident” scenario
Map auto-pans to the Gulf of Finland with vessels loaded
Set up script for Finland cable incident analysis:
Or via command line:
python scripts/setup_baltic_poc.pyAPI Endpoints:
MethodEndpointDescriptionPOST/api/poc/loadLoad POC scenario (body: {"poc": "baltic"})POST/api/poc/listList available POC scenarios
Adds:
FITBURG (MMSI: 518100989) - C-Lion1 incident vessel
EAGLE S (MMSI: 255806583) - Estlink-2 incident vessel
Infrastructure zones (C-Lion1, Estlink-2, Balticconnector)
Incident timeline events
Baltic Sea bounding box configuration
Laden Status Detection (NEW)
Cargo loading/discharge detection through draft change analysis - essential for dark fleet monitoring.
Detection Methods
MethodDescriptionUse CaseDraft ChangesMonitor AIS-reported draft variationsDetect loading/unloading operationsSTS DetectionStationary draft changes at seaShip-to-ship transfer identificationAIS/Satellite DiscrepancyCompare AIS draft with satellite observationsDetect unreported transfersStatic Draft AnomalyNo draft change during extended port visitsIdentify data manipulation
Laden States
StateDescriptionDraft RatioLADENFully loaded>85% of max draftPARTIALPartially loaded55-85%BALLASTEmpty/light<55%
API Endpoints
MethodEndpointDescriptionGET/api/vessels/:id/laden-statusAnalyze vessel laden status from draft changes
Example Response
{
“current_state”: “laden”,
“current_draft_m”: 14.2,
“loading_ratio”: 88.7,
“sts_transfer_count”: 2,
“high_priority_anomalies”: 1,
“recent_events”: [
{”event_type”: “loading”, “draft_change_m”: 6.0, “estimated_cargo_tonnes”: 85000}
]
}Satellite Intelligence (NEW)
Framework for satellite imagery integration (optical and SAR) for vessel monitoring.
Supported Providers
ProviderTypeResolutionAccessSentinel-2Optical10mFree (Copernicus)Sentinel-1SAR20mFree (Copernicus)PlanetOptical3-5mCommercialMaxarOptical0.3mCommercialICEYESAR1mCommercial
Features
Imagery Search - Find available satellite passes over vessel location
Vessel Detection - Automated ship detection from SAR imagery
Laden Status - Freeboard analysis from high-resolution optical
STS Detection - Identify ship-to-ship transfer operations
Dark Vessel Detection - SAR vessels without AIS correlation
API Endpoints
MethodEndpointDescriptionGET/api/satellite/search?lat=X&lon=YSearch for satellite imageryGET/api/vessels/:id/satelliteGet imagery for vessel locationGET/api/storage-facilitiesList monitored tank farmsGET/api/storage-facilities/:id/analysisAnalyze storage levels
Shoreside Photography (NEW)
Crowdsourced port photograph collection for vessel verification and intelligence.
Photo Metadata
FieldDescriptionLocationGPS coordinates or port nameTimestampWhen photo was takenVessel IDLinked vessel MMSI/nameIntel Valuelow/medium/high/criticalStatuspending/verified/rejected
Photo Types
TypeUse CasevesselGeneral vessel identificationstsShip-to-ship transfer documentationcargoCargo operation evidencemodificationVessel alteration detectionfacilityPort/terminal documentation
API Endpoints
MethodEndpointDescriptionGET/api/photosList recent photosGET/api/photos/:idGet photo detailsGET/api/vessels/:id/photosGet photos for vesselGET/api/photos/nearby?lat=X&lon=YPhotos near locationPOST/api/photos/uploadUpload new photoPOST/api/photos/:id/verifyUpdate verification status
Upload Example
curl -X POST http://localhost:8080/api/photos/upload \
-H “Content-Type: application/json” \
-d ‘{
“image”: “base64_encoded_image_data”,
“filename”: “vessel_photo.jpg”,
“photo_type”: “vessel”,
“vessel_mmsi”: “518100989”,
“vessel_name”: “FITBURG”,
“port_name”: “Helsinki”,
“latitude”: 60.15,
“longitude”: 24.93,
“tags”: [”dark_fleet”, “sanctions”]
}’Oil Storage Inventory (NEW)
Tank farm monitoring for supply chain intelligence.
Monitored Facilities
FacilityCountryTypeNotesJose TerminalVenezuelaTerminalMain crude exportTanjung PelepasMalaysiaFloating StorageIran STS hubKalamata AnchorageGreeceFloating StorageRussia STS hubNingbo-ZhoushanChinaTerminalMajor import terminal
API Endpoints
MethodEndpointDescriptionGET/api/storage-facilitiesList monitored facilitiesGET/api/storage-facilities?region=venezuelaFilter by regionGET/api/storage-facilities/:id/analysisAnalyze fill levels from satellite
Feature Status API
Check which modules are available:
curl http://localhost:8080/api/features{
“laden_status”: true,
“satellite”: true,
“photos”: true,
“dark_fleet”: true,
“infra_analysis”: true,
“sanctions”: true,
“gfw”: true,
“gfw_configured”: true,
...
}Global Fishing Watch Integration (NEW)
Free API integration for vessel event data - AIS gaps, encounters, loitering, port visits.
Features
FeatureDescriptionAIS GapsPeriods where vessel stopped transmittingEncountersShip-to-ship meetings (STS detection)LoiteringExtended time in an areaPort VisitsPort call historyVessel IdentitySearch by MMSI, IMO, name
Setup
Register at https://globalfishingwatch.org/our-apis/ (free)
Get API token
Configure via one of these methods:
Option A: UI Entry (Recommended)
Click any vessel in the watchlist
Scroll to “Global Fishing Watch” section
Paste your token and click Save
Reload the page
Option B: API Configuration
curl -X POST http://localhost:8080/api/gfw/configure \
-H “Content-Type: application/json” \
-d ‘{”token”: “YOUR_GFW_TOKEN”}’Option C: Environment Variable
export GFW_API_TOKEN=your_token_hereOption D: Config File Create gfw_config.json:
{”api_token”: “your_token_here”}API Endpoints
MethodEndpointDescriptionGET/api/gfw/statusCheck if GFW is configuredGET/api/gfw/search?mmsi=XSearch vessel identityGET/api/vessels/:id/gfw-eventsGet all events for vesselGET/api/vessels/:id/gfw-riskGet dark fleet risk indicatorsGET/api/gfw/sts-zone?min_lat=X&...Check STS activity in zonePOST/api/gfw/configureConfigure API token
Example: Dark Fleet Risk Analysis
curl http://localhost:8080/api/vessels/1/gfw-risk?days=90{
“risk_score”: 65,
“risk_level”: “high”,
“risk_factors”: [
“Extended AIS gaps: 72 hours”,
“Multiple encounters: 4”
],
“ais_gaps”: {”count”: 3, “total_hours”: 72},
“encounters”: {”count”: 4},
“loitering”: {”count”: 2, “total_hours”: 48}
}STS Zone Monitoring
Monitor known STS hotspots:
# Check Tanjung Pelepas (Malaysia) - Iran oil STS hub
curl “http://localhost:8080/api/gfw/sts-zone?min_lat=1.2&min_lon=103.4&max_lat=1.5&max_lon=103.7&days=30”Sanctions Database Integration (NEW)
Real-time sanctions data from multiple sources for vessel compliance checking.
Data Sources
SourceVesselsCoverageFormatFleetLeaks800+OFAC, EU, UK, CA, AU, NZCSV/JSONOFAC SDNOfficialU.S. TreasuryXML/CSVTankerTrackers1,300+Blacklisted tankersCSV
FleetLeaks API Endpoints (No Auth Required)
EndpointDescriptionGET /export/vessels.csvBulk CSV export (primary)GET /api/vesselsJSON APIGET /api/vessels/{imo}Single vessel detailGET /api/search?q=Search by name/IMO
Confidence-Weighted Scoring
AuthorityWeightNotesOFAC / UN1.0Highest enforcementEU / UK0.95Strong enforcementCA / AU0.85ModerateNZ0.80Lower
+0.05 bonus for 3+ authorities (cross-jurisdictional designation)
API Endpoints
MethodEndpointDescriptionGET/api/sanctions/check?imo=XCheck vessel by IMOGET/api/sanctions/check?name=XCheck vessel by nameGET/api/sanctions/check?mmsi=XCheck vessel by MMSIGET/api/sanctions/statsDatabase statisticsGET/api/vessels/:id/sanctionsSanctions status for vessel
Usage
from sanctions import SanctionsDatabase, fetch_fleetleaks_map_data
# Fetch all sanctioned vessels from FleetLeaks (800+ vessels)
vessels = fetch_fleetleaks_map_data()
# Initialize database
db = SanctionsDatabase()
db.load_known_vessels() # Load built-in database
# Check vessel
result = db.check_vessel(imo=”9179834”)
# Returns: {”sanctioned”: True, “authorities”: [”OFAC”, “UK”], ...}
# CLI commands
# python sanctions.py init - Load known vessels
# python sanctions.py update - Fetch from FleetLeaks/OFAC
# python sanctions.py stats - Show statistics
# python sanctions.py check --imo 9328716Example API Response
curl “http://localhost:8080/api/sanctions/check?name=SKIPPER”{
“sanctioned”: true,
“vessel”: {
“imo”: “9179834”,
“name”: “SKIPPER”,
“flag”: “Cameroon”,
“vessel_type”: “Crude Oil Tanker”
},
“authorities”: [”OFAC”, “UK”],
“venezuela_linked”: true,
“iran_venezuela_china_route”: true
}Academic References
The behavior detection algorithms are based on peer-reviewed research:
Foundational Studies
Global Fishing Watch Nature Study (2024) - “Satellite mapping reveals global scope of hidden fishing activity”
Finding: 75% of industrial fishing vessels not publicly tracked
Method: SAR/GPS correlation with machine learning
URL: https://globalfishingwatch.org/research/global-footprint-of-fisheries/
MPA Compliance Study (Science, July 2025) - First demonstration that SAR can detect fishing in protected areas
Finding: AIS missed 90% of SAR-based detections in MPAs
URL:
https://www.science.org/
AIS Manipulation Research
“AIS Data Manipulation in the Illicit Global Oil Trade” (MDPI JMSE, 2023)
Focus: Russian sanctions evasion via tanker AIS spoofing
“AIS Data Vulnerability Indicated by a Spoofing Case-Study” (MDPI, 2021)
Finding: Chinese GPS spoofing devices creating “crop circle” patterns
Shadow Fleet Analysis
“Shadow Fleets: A Growing Challenge in Global Maritime Commerce” (MDPI Applied Sciences, 2025)
Framework: Distinguishes “dark fleets” from “gray fleets.”
Finding: Shadow fleets now ~10% of global seaborne oil transport
STS Transfer Detection
“Automatic Detection of Dark Ship-to-Ship Transfers” (arXiv, 2024)
Method: SAR/AIS correlation for sanctions evasion detection
Operational Systems
“INSURE System for Ghana IUU Fishing Monitoring” (MDPI Remote Sensing, 2019)
Performance: 91% detection rate, 75% SAR detections had no AIS
Intelligence Output
The intelligence module (intelligence.py) produces standardized, defensible assessments:
Intelligence Object
{
“vessel_id”: 1,
“assessment”: “Likely gray-zone logistics. Key indicators: AIS gap detected, loitering behavior”,
“assessment_level”: “suspicious”,
“confidence”: 0.73,
“deception_likelihood”: 0.45,
“indicators”: [
{”name”: “ais_gap_significant”, “weight”: 0.15, “description”: “Significant AIS gap detected (36 hours)”},
{”name”: “loitering_detected”, “weight”: 0.12, “description”: “Loitering behavior detected”}
],
“confidence_breakdown”: {
“confidence”: 73,
“breakdown”: [
{”component”: “AIS Consistency”, “score”: 0.6, “weight”: 0.35, “contribution”: “+0.21”},
{”component”: “Behavioral Normalcy”, “score”: 0.7, “weight”: 0.35, “contribution”: “+0.25”},
{”component”: “SAR Corroboration”, “score”: 0.5, “weight”: 0.30, “contribution”: “+0.15”}
],
“adjustments”: [
{”name”: “Signal quality”, “source”: “medium”, “adjustment”: “-0.03”},
{”name”: “Data freshness”, “adjustment”: “-0.05”}
]
},
“data_sources”: [”AIS”, “SAR”],
“last_updated”: “2025-12-31T12:00:00Z”
}Assessment Levels
LevelDescriptionbenignNormal operating patternmonitoringInsufficient data for assessmentanomalousSingle behavioral deviation detectedsuspiciousMultiple indicators triggeredlikely_gray_zoneHigh deception likelihood with technical/behavioral anomaliesconfirmed_threatVessel classified as a confirmed threat
Indicator Types
TypeExamplesbehavioralAIS gaps, speed anomalies, and loiteringtechnicalPosition jumps, SAR mismatchesownershipFlag of convenience, ownership opacity
Running Tests
# Run all tests
python3 run_tests.py
# Run with verbose output
python3 run_tests.py -v
# Run specific test module
python3 run_tests.py test_confidence
python3 run_tests.py test_intelligence
python3 run_tests.py test_sar_import
python3 run_tests.py test_database
python3 run_tests.py test_apiDemo Data
The tracker includes comprehensive demo data for ZHONG DA 79:
{
“description”: “Tracked vessels for OSINT correlation”,
“vessels”: [
{
“id”: 1,
“name”: “ZHONG DA 79”,
“mmsi”: “413000000”,
“flag_state”: “China”,
“vessel_type”: “Container Feeder”,
“aliases”: [”ZHONGDA 79”, “ZHONGDA79”, “ZHONG DA79”],
“keywords”: [”arsenal ship”, “containerized missile”, “VLS”, “CIWS”, “Type 1130”],
“related_locations”: [”Shanghai”, “Longhai”, “Fujian”, “Huangpu River”, “Hudong-Zhonghua”]
}
]
}Architecture
┌─────────────────────────────────────────────────────────────────────────┐
│ Arsenal Ship Tracker │
├─────────────────────────────────────────────────────────────────────────┤
│ │
│ ┌─────────────┐ ┌─────────────┐ ┌─────────────┐ ┌─────────────┐ │
│ │ AISStream │ │ AISHub │ │ Marinesia │ │ Open-Meteo │ │
│ │ (WebSocket) │ │ (REST) │ │ (REST) │ │ (Weather) │ │
│ └──────┬──────┘ └──────┬──────┘ └──────┬──────┘ └──────┬──────┘ │
│ │ │ │ │ │
│ └───────────────┼───────────────┼───────────────┘ │
│ │ │ │
│ ┌──────────────────────▼───────────────▼──────────────────────┐ │
│ │ AIS Source Manager │ │
│ │ (Priority-based fallback system) │ │
│ └──────────────────────────┬───────────────────────────────────┘ │
│ │ │
│ ┌─────────────────────────┼─────────────────────────┐ │
│ │ │ │ │
│ ▼ ▼ ▼ │
│ ┌──────────────┐ ┌──────────────┐ ┌──────────────────────┐ │
│ │ Live Vessel │ │ Geofence │ │ AI Intelligence │ │
│ │ Tracking │ │ Detection │ │ (OpenAI + MMSI │ │
│ │ │ │ │ │ Lookups) │ │
│ └──────┬───────┘ └──────┬───────┘ └──────────┬───────────┘ │
│ │ │ │ │
│ ┌─────▼─────┐ ┌─────▼─────┐ ┌─────▼─────┐ │
│ │ SAR Ship │ │ Confidence│ │ OSINT │ │
│ │ Detection │ │ Scoring │ │ Correlator│ │
│ │ (SNAP) │ │ │ │ │ │
│ └─────┬─────┘ └─────┬─────┘ └─────┬─────┘ │
│ │ │ │ │
│ └─────────────────┼─────────────────────┘ │
│ │ │
│ ┌──────▼──────┐ │
│ │ SQLite │ │
│ │ (WAL Mode) │ │
│ └──────┬──────┘ │
│ │ │
│ ┌──────▼──────┐ │
│ │ REST API │ │
│ │ Server │ │
│ └──────┬──────┘ │
│ │ │
│ ┌──────▼──────┐ │
│ │ Dashboard │ │
│ │ (Web) │ │
│ └─────────────┘ │
│ │
└─────────────────────────────────────────────────────────────────────────┘
Key Intelligence: ZHONG DA 79
AttributeValueVessel TypeContainer FeederLength97 metersFlag StateChinaClassificationConfirmed Arsenal ShipVLS Cells48-60 (containerized)CIWSType 1130 30mmDecoysType 726Possible MissilesCJ-10, YJ-18, YJ-21Refit LocationLonghai Shipyard (Apr-Aug 2025)Current LocationShanghai Huangpu RiverPLAN RegistryNOT LISTED (civilian status)
Sources
License
Internal use only. OSINT compilation for research purposes.